
WordPress is one of the most famous and the most widely-used Content Management System (CMS). This makes it an alluring target by cybercriminals.
According to the researchers at website security company Sucuri, malicious WordPress plugin is being used to surreptitiously mine cryptocurrency by running Linux binary code. The malicious plugin is also being used to maintain access to compromised servers.
Essentially, the malicious plugin is a lone of the legitimate plugin.
What this means, the hackers can skip the process of creating the plugin from scratch, and simply alter some of the existing codes to include nefarious components, designed for for illicit purposes.
The approaches in this attack are nothing new, but they do demonstrate how important it is for developers to run a comprehensive malware clean.

As explained by by Sucuri on a blog post:
"These plugins appear to be legitimate, but inspecting the code reveals that the plugin is not just an innocent plugin at all. The fake plugins are actually part of the attack—and in most cases used as a backdoor for the attacker to maintain access to the compromised website environment, even after the initial infection vector has been cleaned up."
The researchers found the first instance of malicious cryptomining malware plugin on compromised websites containing 'wpframework' in September 2019.
This plugin has been planted by bad actors to gain and maintain unauthorized access to the site environment.
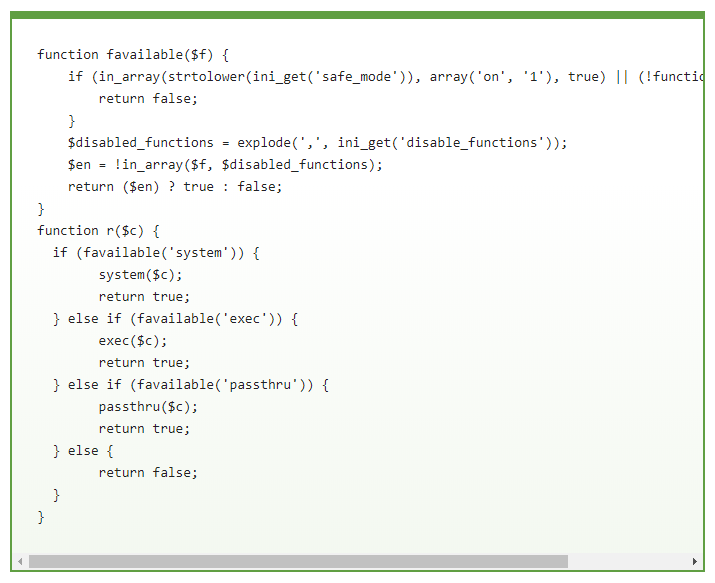
Once installed, the plugin initially checks to see whether there are any disabled functions. It then scans for the usual 'system', 'exec', and 'passthru' functions, which allow for command execution on the server level.
After digging deeper through the codes, this was where the researchers noticed that the malicious plugin directory has a binary file. This file was the cryptocurrency miner, already identified by multiple antivirus vendors.
On its conclusion, the researchers said that malware can hide anywhere. And in this case, they can also hide within plugins, which many webmasters may not suspect.
"We have seen many cases where website owners replace the WordPress core files during a malware cleanup, but keep their existing plugins and themes," explained the researchers. "By simply migrating their third-party extensions to a new site, they maintain the backdoor and get reinfected in the process."
"What is especially concerning about this particular fake plugin is that it can be easily used to just run just about any code through the eval function," they added.
To prevent malicious plugins from infecting websites, developers should monitor changes to active plugins installed on their sites, and see if they ever provide unauthorized access. Using a web application firewall can also prevent most attacks and further restrict unauthorized access to the WordPress administrator dashboard.
Previously, the researchers at Sucuri also found that bad developers were also using malicious plugins to to encrypt WordPress posts