
People browse the web using web browsers installed on their devices. Through them, the web is open to see and visit.
But what will happen when those web browsers have flaws? If the flaw is a security issue, then catastrophe can happen. Considering that there are billions of internet users worldwide, even a single flaw that is present on those web browsers is a recipe for a global disaster.
This time, some of the world's most popular browsers have become targets of a malware campaign, dubbed the 'Adrozek'.
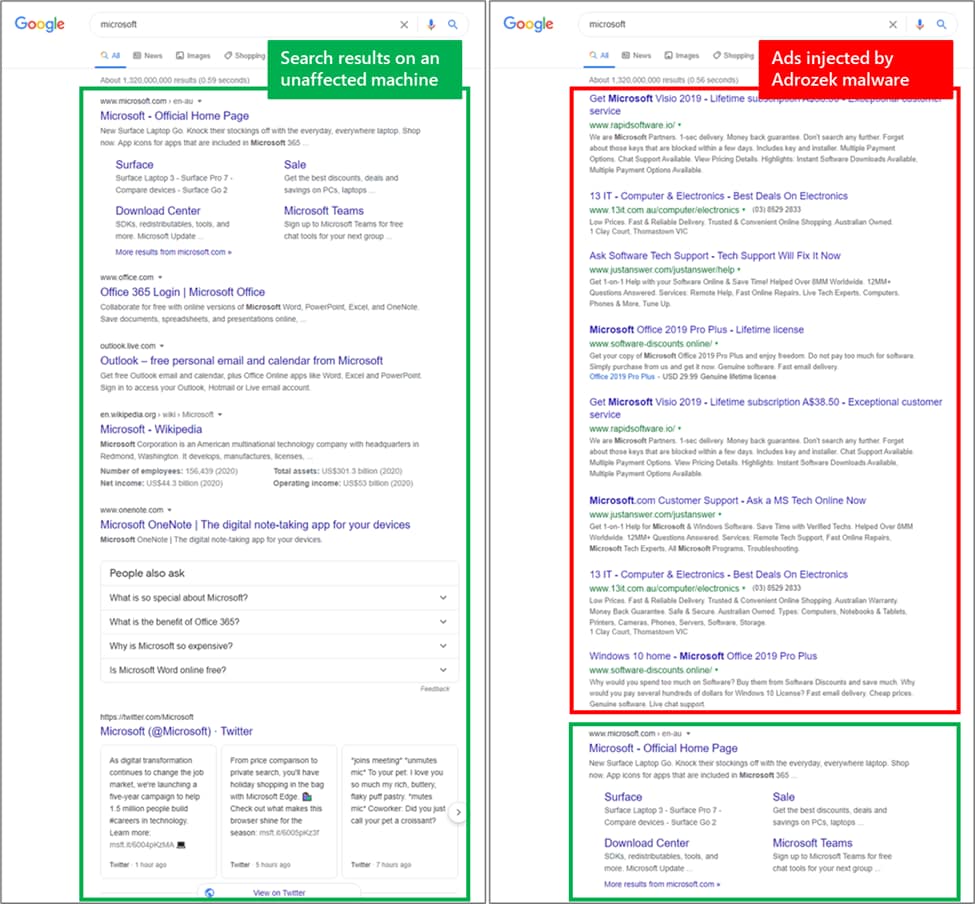
Discovered by Microsoft, the malware injects ads, "often on top of legitimate ads from search engines." It does this primarily to lead people to affiliate pages so the authors can earn money.
But in doing so, the malware also silently adds malicious browser extensions and changing the browser settings to insert ads into webpages. It is also modifying the Dynamic Link Library (DLL) files per target browser, in order to turn off the browser's built-in security controls.
Circulating since at least May 2020, the malware claims tens of thousands of new victims every day.
According to Microsoft on its report:
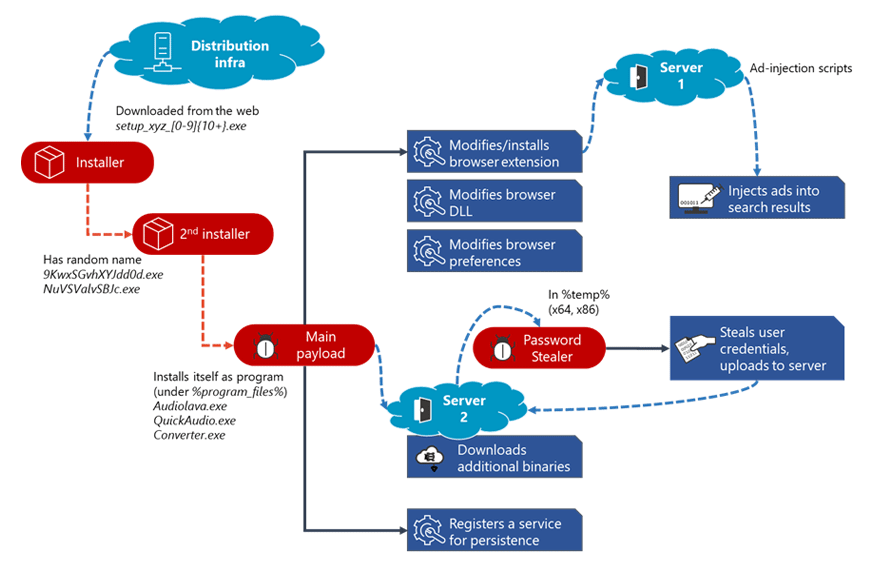
The researchers from Microsoft said that the Adrozek malware is installed on devices through drive-by download.
The authors of the malware distribute the campaign through thousands of unique Adrozek installer samples. Each of these files is heavily obfuscated, and created using unique file name, in order to fool antivirus security systems.
When run, the installer drops an executable file with a random file name in the %temp% folder. This file drops the main payload in the Program Files folder using a file name that makes it look like a legitimate audio-related software.
The malware is then installed like a usual program in Windows.
The malware targets different extensions on each browser, but it still uses the same malicious scripts to infect these extensions. These then help the attackers connect the browser to their server and then inject advertisements into search results.
Microsoft managed to track 159 unique domains, with each hosting an average of 17,300 unique URLs, which in turn host more than 15,300 unique malware samples on average.
"While many of the domains hosted tens of thousands of URLs, a few had more than 100,000 unique URLs, with one hosting almost 250,000. This massive infrastructure reflects how determined the attackers are to keep this campaign operational," the researchers said.
The attackers rely on polymorphism, a method to continually change the characteristics of the malware to avoid detection. Polymorphism also allows the authors to distribute the malware in huge volumes of samples.
"In total, from May to September 2020, we recorded hundreds of thousands of encounters of the Adrozek malware across the globe, with heavy concentration in Europe and in South Asia and Southeast Asia. As this campaign is ongoing, this infrastructure is bound to expand even further."
Adrozek specifically targets Microsoft Edge, Google Chrome, Yandex Browser, and Mozilla Firefox.
But with the first three are all based on the Chromium open-source browser, other browsers such as Brave, Opera and Vivaldi should also be considered vulnerable.
Usually, malware on a web browser can be removed by using antivirus solutions or by resetting the browser.
But Adrozek is a little smarter than the average browser-hijacking adware, because it burrows deep into the browsers, altering or mimicking legitimate extensions, switching off security protections, disabling automatic updates and even altering Registry entries and creating a separate Windows service to run independently.
What this means, getting rid of this particular malware, requires a lot more attention.
"While the malware's main goal is to inject ads and refer traffic to certain websites, the attack chain involves sophisticated behavior that allow attackers to gain a strong foothold on a device," the Microsoft blog post said.
"The addition of credential-theft behavior shows that attackers can expand their objectives to take advantage of the access they're able to gain."
Effectively protecting against rampant, persistent campaigns like the Adrozek requires advanced, behavior-based detection system that can spot anomalies across the whole attack chain rather than specific components.
Using endpoint protection solutions for example, can help block the treat posed by Adrozek.