
People can do anything for money. From scamming to threatening, from the real-world and to the internet.
On the internet, one of the ways people can force people to pay a sum of money, is by using a malware which does damage, like for example, using a ransomware, which encrypts users data and hold them as ransom. There is also another way which has become more common: sextortion.
What it does, is recording victims' screen and browsing activities, to then record them when they visit porn websites.
And here, researchers from antivirus developer ESET have discovered a variant of these sextortion malware, but with added abilities.
Dubbed the 'Verenyky', the malware can also steal unsuspecting users' passwords, financial data and more.
According to the researchers, the malware was primarily designed to target victims in France, who use the French ISP Orange SA. But that doesn't indicate that the malware can't do anything beyond the said ISP.
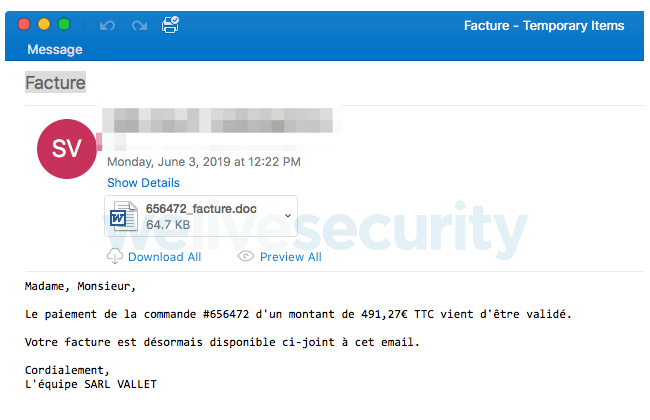
The malware spreads using spam emails, which trick potential victims into believing that the attachment contains a protected and secured document by Microsoft.
But what it really does is activating a virus which gives it permission to run macros in Microsoft Word.
"Overall, the email text content, the document’s filename and the 'protected' content of the document emphasize to the recipients that they are dealing with a real bill and that they should open it. The quality of the French is very good; overall, the document is convincing."

Once activated, the macro in the fake document executes processes that would allow the malware to download additional files for its sextortion attempt, as well as to gather other users' sensitive data.
According to the researchers, the sextortion scam aspect of the malware shouldn't be a major threat, with ESET researcher Bruce P. Burrell saying that in most cases, these attempts are launched by so-called hackers using a "sextortion scam kit" purchased from the dark web.
Until its finding, no one had been extorted using the Varenyky malware.
However, the more concerning part is that, the downloaded document when allowed to run macros in a system, can pose significant risks. If this happens, the hacker can easily steal users' passwords and financial data, and spreading the malware to all people in their contact lists.
According to ESET, the developers are still developing and tweaking the malware, saying that:
To defend against this kind of malware, ESET suggests people to keep their operating systems up to date, as well as using antivirus software, and avoid opening any email attachments or downloading files unless it's certain that they're safe.