
Things that are simple, are usually small. And complex things tend to be larger. But 'Kobolos' is small, yet complex.
Discovered by researchers at ESET and as described in a blog post, the malware's codebase is tiny.
But yet, it is sophisticated enough that it is portable to many operating systems including Linux, BSD, Solaris, and possibly AIX and Windows.
Because of its tiny size that packs a lot of tricks, the cybersecurity team named the malware 'Kobalos', in reference to the kobalos, which is a small and mischievous goblin-like creature from the Greek mythology.
The researchers found this malware when working with the CERN Computer Security Team.
During that time, researchers at ESET found a "unique, multiplatform" malware targeting high performance computer (HPC) clusters.
The researchers have traced the malware to attacks against supercomputers used by a large Asian Internet Service Provider (ISP), a U.S. endpoint security vendor, and a number of privately-held servers, among others.
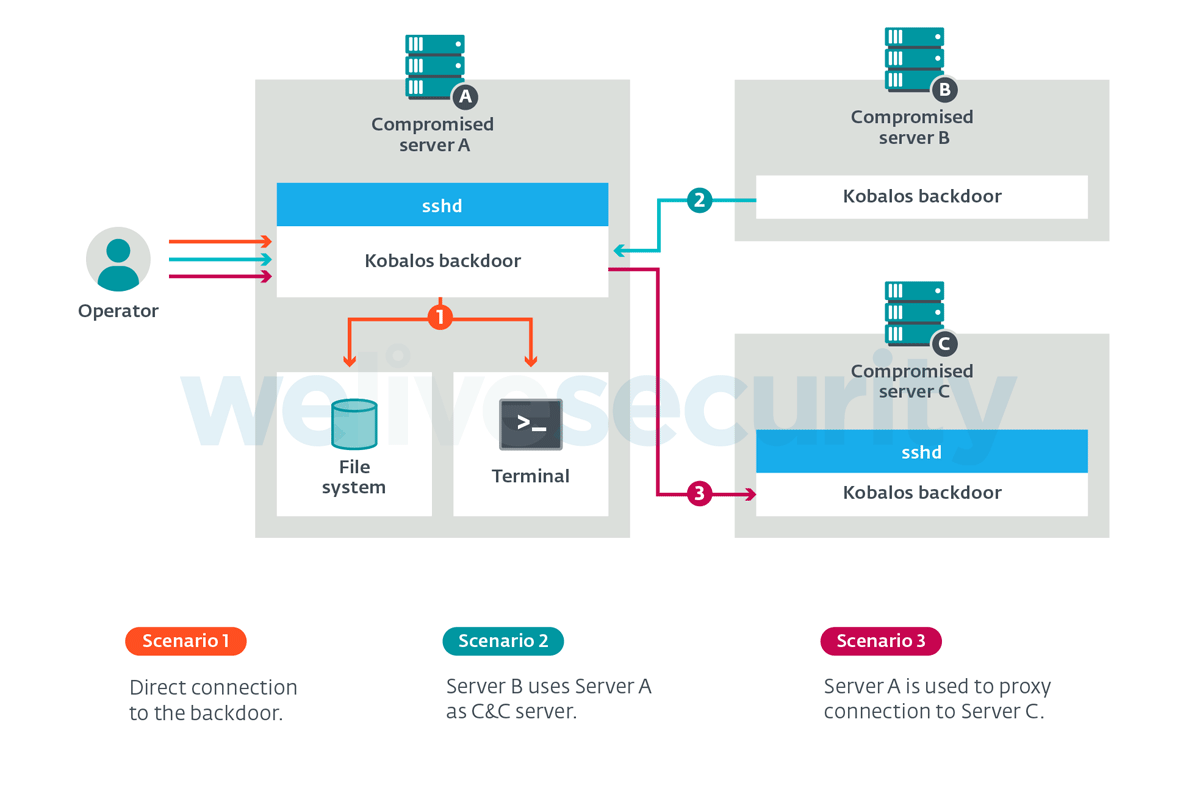
Kabalos is essentially a backdoor.
What it does, is burying itself deep in an OpenSSH server executable. Once installed on a supercomputer, it will automatically open a backdoor if a call is made through a specific TCP source port.
With a backdoor open, hackers behind the campaign can have remote access to the supercomputers' file systems. This would allow them to create terminal sessions, and also act as connection points to other servers infected with the malware.
ESET said that Kobalos' unique ability is its ability to turn any compromised server into a command and control server through a single command.
"As the C2 server IP addresses and ports are hardcoded into the executable, the operators can then generate new Kobalos samples that use this new C2 server," the researchers noted.
"This credential stealer is unlike any of the malicious OpenSSH clients we’ve seen before, and we’ve looked at tens of them in the past eight years. The sophistication of this component is not the same as Kobalos itself: there was no effort to obfuscate early variants of the credential stealer. For example, strings were left unencrypted and stolen usernames and passwords are simply written to a file on disk. However, we found newer variants that contain some obfuscation and the ability to exfiltrate credentials over the network," the researchers added.
"The presence of this credential stealer may partially answer how Kobalos propagates."
Most machines compromised by Kobalos also have their SSH client compromised.
"Anyone using the SSH client of a compromised machine will have their credentials captured. Those credentials can then be used by the attackers to install Kobalos on the newly discovered server later."
The malware was a challenge to analyze because all of its code is held in a "single function that recursively calls itself to perform subtasks," explained ESET, adding that all of its strings are also encrypted.
This makes it difficult for the researchers to reverse engineer the malware.
On their report, ESET researchers said that they were unable to determine the intention of the operators of Kobalos.
"No other malware, except for the SSH credential stealer, was found by the system administrators of the compromised machines. Hopefully, the details we reveal today in our new publication will help raise awareness around this threat and put its activity under the microscope."
According to ESET, Kobalos is detected as Linux/Kobalos or Linux/Agent.IV. The SSH credential stealer is detected as Linux/SSHDoor.EV., Linux/SSHDoor.FB or Linux/SSHDoor.FC.
The malware's activities can be detected through non-SSH traffic initiated on the port attributed to an SSH server.
As for remediation, the researchers suggested people to always use two-factor authentication (2FA) for connecting to SSH servers.
"Kobalos is another case where 2FA could have mitigated the threat, since the use of stolen credentials seems to be one of the ways it is able to propagate to different systems," the researchers said.