
Since most users aren't developers, and have no technical idea about what's going on, tech companies think that they can do whatever they like behind people's back.
Just when Meta's apps are found tracking users using their respective in-app browsers, this time, it's TikTok's turn under fire. The popular social media platform is found doing the exact same thing.
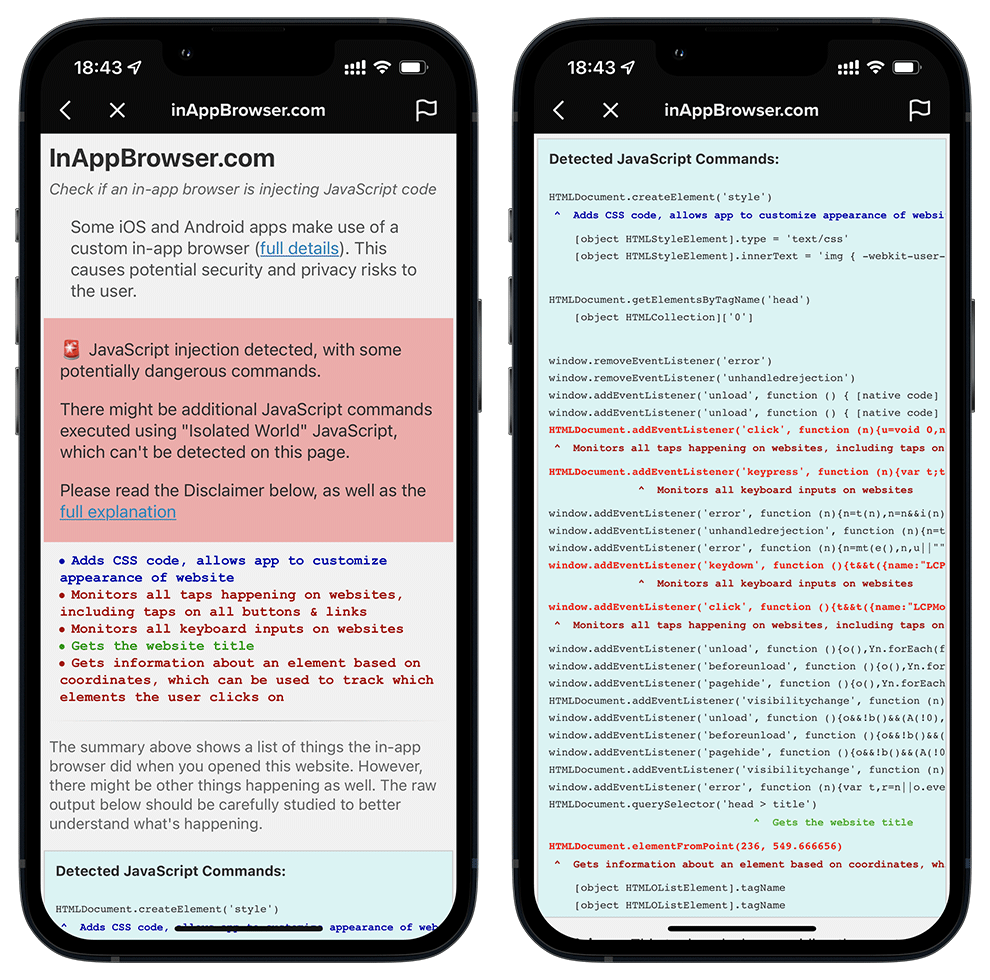
According to security researcher Felix Krause in a blog post, TikTok's custom in-app browser on iOS is able to injects JavaScript code into external websites.
This allows TikTok to practically monitor "all keyboard inputs and taps" while a user is interacting with a given website.
Krause explained that TikTok's in-app browser "subscribes" to all keyboard inputs while a user interacts with an external website.
What this means, the in-app browser is able to record sensitive details like passwords and credit card information, along with every tap on the screen.
Another way of saying this, installing TikTok is the "equivalent of installing a keylogger [...] ."
While this practice is certainly bad in terms of privacy, and indeed violates users' privacy, Krause stressed that in regards to the JavaScript code that TikTok injects, doesn't conclude that the app is bad.
He said that "just because an app injects JavaScript into external websites, doesn't mean the app is doing anything malicious."
In a statement, a TikTok spokesperson acknowledged the JavaScript code in question, and admitted that it exists.
However, the spokesperson said that the JavaScript in question is only used for debugging, troubleshooting, and performance monitoring to ensure an "optimal user experience."
"Like other platforms, we use an in-app browser to provide an optimal user experience, but the Javascript code in question is used only for debugging, troubleshooting and performance monitoring of that experience — like checking how quickly a page loads or whether it crashes," the statement said.
For privacy concerned individuals, users who wish to protect themselves from being exposed to this kind of trackers, can switch browsers.
According to Krause. users can switch to viewing a given link in the platform's default browser if possible, such as Safari on the iPhone and iPad.
"Whenever you open a link from any app, see if the app offers a way to open the currently shown website in your default browser," wrote Krause.
But for users of TikTok, they don't have the option to use other web browsers other than the in-app browser.
"During this analysis, every app besides TikTok offered a way to do this."

In an explanation, Krause said that he found the tracker by utilizing the InAppBrowser.com, which is simply a tool that can list all JavaScript commands executed by an iOS app when rendering a web page.
All users who wish to use the app needs to do, is open the app they want to check and share the InAppBrowser URL somewhere within it — such as DMing the link to a friend or posting it in a comment. From there, users can tap the link and get a report from the website on what scripts are running in the background.
"I started using this tool to analyze the most popular iOS apps that have their own in-app browser," he said.
This is made simpler for him, since all iOS apps that wish to access HTML are required to use the Safari rendering engine WebKit.
It's worth noting though, that the tool is not able to detect all JavaScript commands executed.
Furthermore, it doesn't show any tracking the app might do using native code.