
With people putting more and more information on their devices, as long those devices are capable of accessing the internet, people will try to hack them.
According to a report from researchers at Zscaler ThreatLabZ, the team has found a new breed of trojan, called Saefko.
Written in .NET, the malware can come equipped with a variety of functions to steal sensitive information, bank details, online gaming credentials, cryptocurrency wallets and more.
Being sold on the Dark Web, the malware is considered a RAT (Remote Access Trojan).
After the attackers trick victims into opening the malware, either by phishing email with malicious attachments, drive-by downloads or others, the malware can infect a machine by first creating a startup key to maintain its persistence.
Saefko attempts to stay under the radar, waiting to ambush.
What makes this RAT particularly dangerous is that, it has a long and specific list of things do once it is installed.
Supporting multiple operating systems, including Windows and Android, Saefko can harvest a victim's personal information and sending them to its operator through its command-and-control (C&2) center.
Saefko also scans for Google Chrome history records for financial website visits, social media, cryptocurrency, gaming, and retail activities, to see whether the victim's worth is worth compromising,.
The websites Saefko checks, include and not limited to: Amazon, BitPay, Mastercard, Steam, Twitch, GameStop, Microsoft, YouTube, Capital, Bitstamp, Facebook, Instagram, and Google's Gmail. And as for understanding more about its victims, it may scan for sites like LinkedIn, the Financial Times, Investing.com, Reuters, and Zacks.
For e-commerce sites, Saefko checks for Boohoo, Superdry, Macy's, Target, and Alibaba.
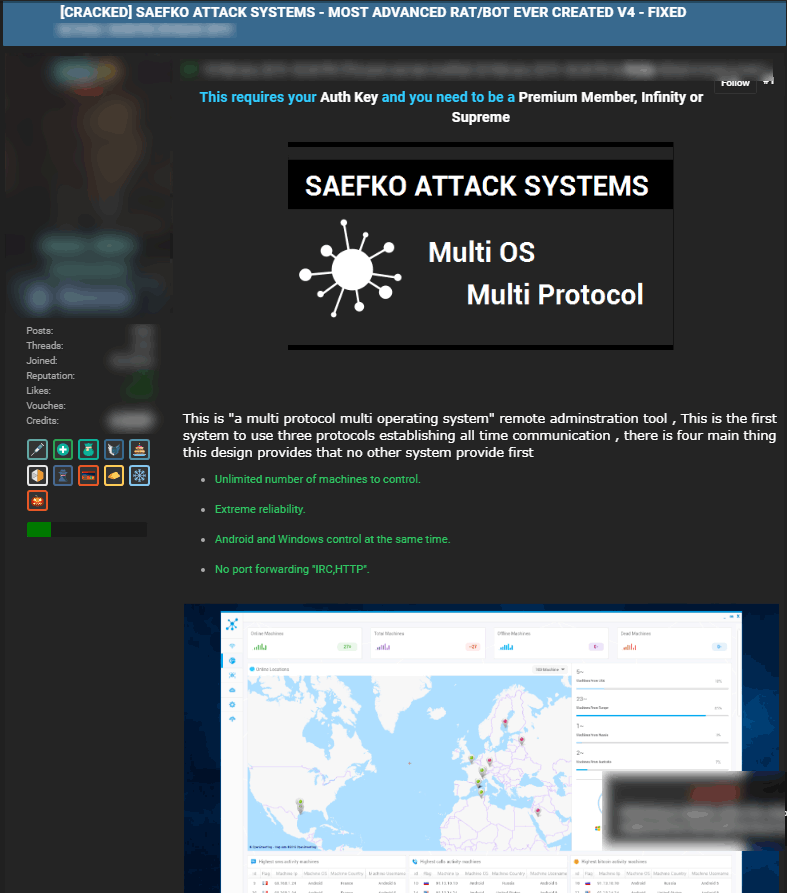
Saefko will occasionally check for an internet connection. And if it sees no connection, it will stay dormant until the next time it re-awakes.
And during a successfully connection to its C&C, it sends all it knows about users' browsing habits to its operator, and awaits for commands. If it receives a green light from its operators, the malware goes to work by launching four different modules:
- HTTPClinet to gather system information, and send it to the C&C, and request additional payloads.
- KEYLogger to capture keystrokes and save them in a text file.
- StartLocalServices to check if removable or networked drives exist, and copy the malware to any removable USB devices found.
- IRCHelper to ping a range of servers for data theft commands, such as downloading and executing new files, opening URLs, grabbing system location information, and the transfer of the keystroke log.
With these malicious activities, the malware can control victims, capable of monitoring their full behavior, access confidential information, compile video files with footage found, activate a webcam, take screenshots, and format drives, among other things.
When it comes to preventing such RAT from infecting devices, users must always stay safe by never download any program or attachments from untrusted sources. They should block any unused port, switch off unused devices, and monitor all outgoing traffic.