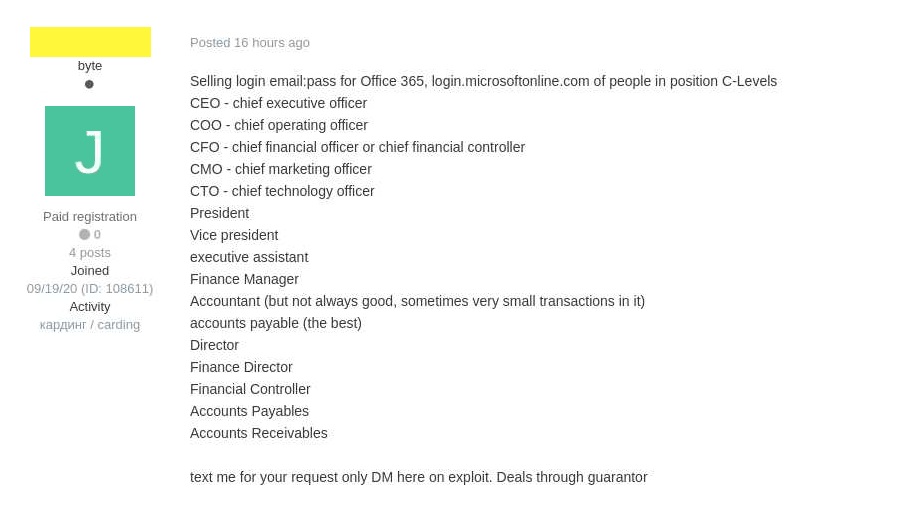
The highest-ranking senior executives of a company, include the company's CEO (Chief Executive Officer), COO (Chief Operating Officer), CFO (Chief Financial Officer), CMO (Chief Marketing Officer), CTO (Chief Technology Officer) and many fancy titles others.
These people are among 'C-Suite' class or 'C-level' individuals. They are considered the most important people inside a company.
And this time, hundreds of email credentials for those C-titled people are being sold at a price of between $100 and $1,500 at Exploit.in, a Russian-speaking underground forum for hackers.
The specific price will be set depending on the company’s size and the person’s role in it.
ZDNet discovered this after following an advertisement.
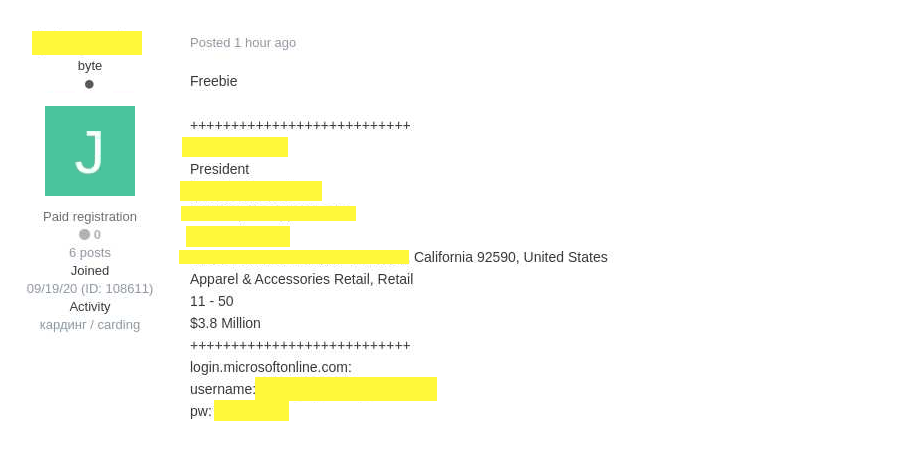
The malicious actor was marketing the information, and to prove that the data is legitimate, the ad also showcased login information for an executive at a UK business management consulting agency and an executive of a U.S. apparel and accessories maker.
ZDNet worked with an unnamed source in the cybersecurity community who contacted the actor to obtain samples of the data being sold.
The actor gave the source two Microsoft account. One belonged to the CEO of a medium-sized U.S. software company and another belonged to the CFO of a retail store in Europe. The source reporting to ZDNet confirmed the validity of the data.
The source is at this time, in the process of notifying all the companies that their executives’ email credentials have been compromised.
When asked, the seller refused to say anything about how he obtained such sensitive information. What he did say is that, he had hundreds of credentials more to sell.
According to data provided by threat intelligence firm KELA, the same threat actor had been tracked and have expressed interest in buying "Azor logs." This is a term that refers to data collected from computers infected with the information-stealer AZORult trojan.
Since this kind of malware targets usernames and passwords, anyone who can get their hands on the logs can indeed obtain some sensitive and expensive information.
This kind of information is often sold in bulk on dedicated marketplaces like Genesis, hacking forums and others.
And here, the threat actor may have managed to filter the data and extract only email credentials that are proven to be valuable.
After that, the threat actor is reselling them individually for a much higher price.
Buyers of these email credentials can use them for CEO scams.
Also known as BEC scams, the scams are by far the most popular form of cybercrime in 2019, having accounted for half of the cybercrime losses reported that year. That, according to the FBI.
"Compromised corporate email credentials can be valuable for cybercriminals, as they can be monetized in many different ways," explained KELA Product Manager Raveed Laeb to ZDNet.
"Attackers can use them for internal communications as part of a 'CEO scam' - where criminals manipulate employees into wiring them large sums of money; they can be used in order to access sensitive information as part of an extortion scheme; or, these credentials can also be exploited in order to gain access to other internal systems that require email-based 2FA, in order to move laterally in the organization and conduct a network intrusion."
One of the best ways to prevent account breach, even in cases like this, is by using multi-factor authentication method.
Also called MFA, the method requires anyone who wishes to login using a valid credential to provide the second evidence in order to prove that they are what they say they are.
In other words, anyone using a valid piece of login credential won't be able to login to that account without presenting the second authentication.
Early this 2020, Microsoft stated that 99.9% of compromised Microsoft accounts didn't use MFA.