Android users may envy iOS users for this feature. But no, not every feature is without bugs.
Apple's AirDrop is a feature available on Apple products, like the iPhones and MacBook computers. It allows seamless and quick wireless sharing of photos, documents and other files with other Apple devices that are nearby.
This feature uses Bluetooth Low Energy and Wi-Fi for discoverability.
AirDrop is extremely easy to use. But sadly, it has a severe bug that leaves users' devices open to potential data theft.
That, according to a report from the researchers at the Technical University of Darmstadt in Germany.
For example, the bug could give scammers access to their email and phone number, said the team of researchers.
They said that it happens because AirDrop uses those two information to to authenticate file sharing.
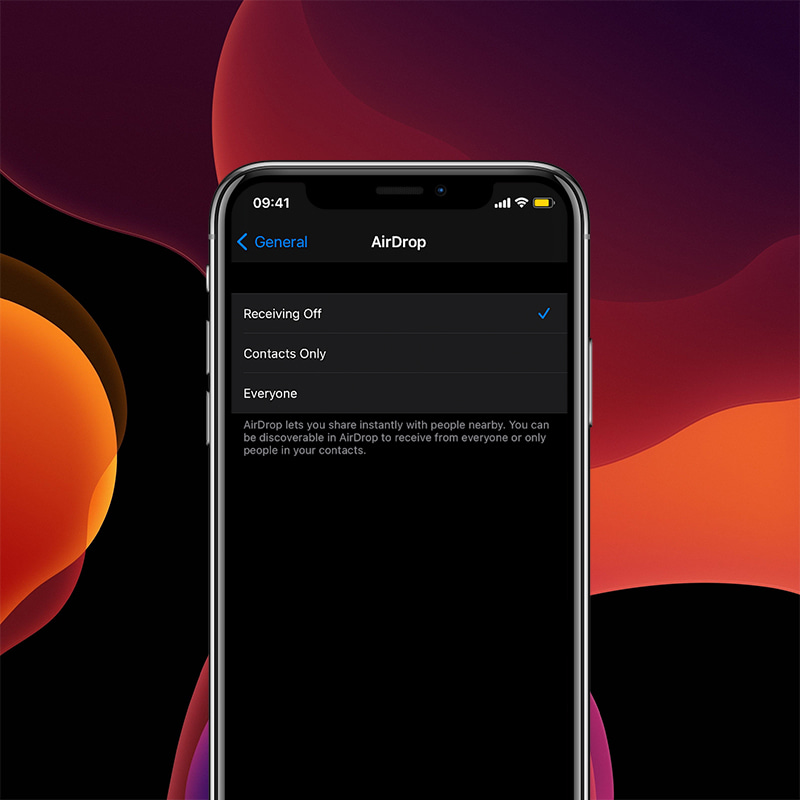
AirDrop has modes that allow only contact to connect, allows anyone to connect, and allows no connections at all.
To determine if the device of a would-be sender is allowed to connect, AirDrop broadcasts Bluetooth advertisements that contain a partial cryptographic hash of the sender's phone number and email address. If any of the truncated hashes matches any phone number or email address in the address book of the receiving device or the device is set to receive from everyone, the two devices can then engage in a mutual authentication handshake.
In other words, AirDrop needs to check phone numbers and email addresses against the other user's address book, before a connection can happen.
And it's during the handshake, that the devices exchange their full SHA-256 hashes that contain users' phone numbers and email addresses.
Things don't stop there, because the "hash values can be quickly reversed using simple techniques such as brute-force attacks."
What this means, the bug potentially expose Apple users to phishing attempts and other scams.
And this bug happens to be around, just because of the way AirDrop works.
Making things even worse, the researchers added that Apple users don't have to initiate a connection with the other device for the bug to be potentially exploited by eavesdroppers.
The researchers said that they have notified Apple about the vulnerability in May 2019. But after two long years, Apple "has neither acknowledged the problem nor indicated that they are working on a solution," they said.
"This means that the users of more than 1.5 billion Apple devices are still vulnerable to the outlined privacy attacks."
"This is an important finding since it enables attackers to get hold of rather personal information of Apple users that in later steps can be abused for spear phishing attacks, scams, etc. or simply being sold," said Christian Weinert, one of the researchers at Germany's Technical University of Darmstadt. "Who doesn't want to directly message, say, Donald Trump on WhatsApp? All attackers need is a Wi-Fi-enabled device in proximity of their victim."
Because the bug is here to stay, or for at least at this time, the researchers suggested that users of Apple devices to disable AirDrop.
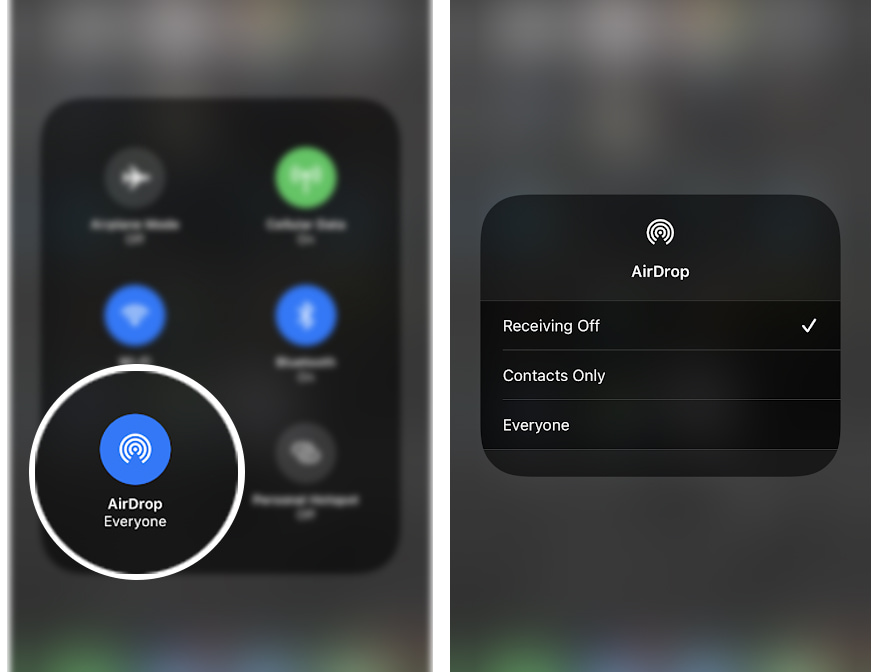
They can do this by navigating to their devices' Settings, to open General. There, they an select AirDrop and select the Receiving Off.
Users are also advised to not open the sharing menu.
When users really need to share files, they can turn the function back on and turn it off as soon as they are finished.
Apple is a company that moves towards privacy, almost faster than anyone else in the industry. It's known for its mature ecosystem, and more polished platforms, if compared to most others. But this AirDrop case, is one good example that not everything Apple makes "just works" — at least not as intended.
Related: How Apple's IOS Devices Were Vulnerable To 'Wi-Fi Broadcast Packet Of Death'