
Android is one of the most flexible and popular mobile operating system. But with the many varieties of customizations, the operating system isn't considered the safest.
Cybersecurity firm ThreatFabric found A new strain of Android banking malware that can steal information from an hundreds of apps, including Amazon, Facebook, Gmail, Tinder and more.
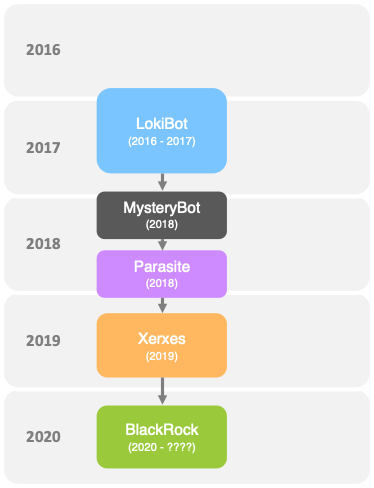
The malware, dubbed BlackRock, the researchers said that it's a tweaked version of a malware called LokiBot.
LokiBot was first observed between end 2016 and beginning 2017 as a rented malware. When the source code of the Trojan was leaked, some malicious actors tweaked it to create a malware called MysteryBot. This malware was again tweaked to create another malware called Parasite.
In 2019, the Parasite malware was further developed to create the Xerxes Trojan, which was unsuccessful.
After the actors made the source code publicly available, in May 2020, the source code was used to create BlackRock.
The threat actors not only adopted the source code from Xerxes, but also tweaked the code to make it more damaging and capable of operating much longer.
The tweak also widens the scope of its attacks beyond online banking apps to general-purpose apps.
BlackRock is capable of:
- Overlaying.
- Keylogging.
- SMS harvesting: SMS listing and SMS forwarding.
- Device information collection.
- SMS sending.
- Remote actions for screen-locking.
- Self-protection to hide its app icons and preventing removal.
- Notifications collection.
- Grant permissions.
- Antivirus detection.
BlackRock's more alarming capability, is its way of harvesting users' account credentials.
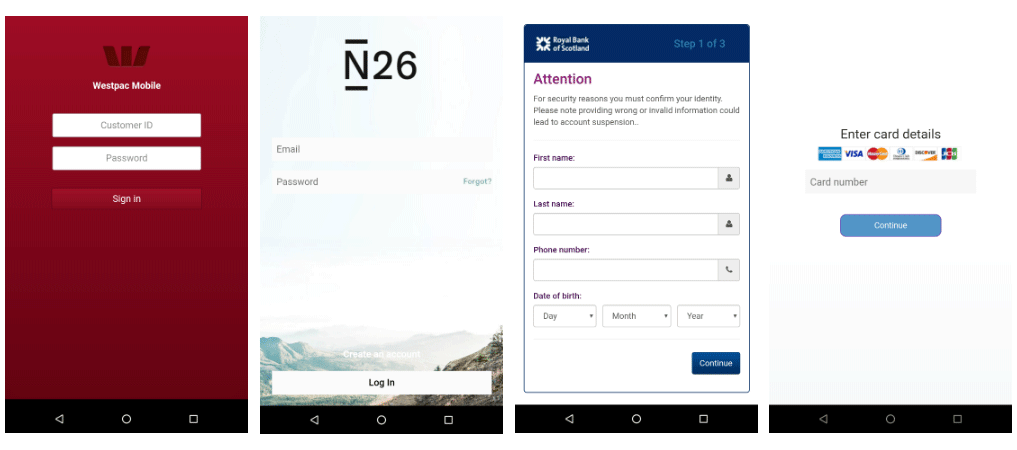
Using a method known as “overlays”, the malware can put its own version of a login page to encourage users into to revealing sensitive information, such as username and password, and credit card information.
The malware can do this on 226 apps, including Amazon, Cash App, eBay, Gmail, Google Play, Hotmail, Instagram, Microsoft Outlook, myAT&T, Netflix, PayPal, Uber and Yahoo Mail, as well as a long list of banking and cryptocurrency apps.
The malware is also capable of stealing credit card numbers from an additional 111 apps, including Facebook, Facebook Messenger, Google Hangouts, Grindr, Instagram, Kik, Periscope, Pinterest, PlayStation, Reddit, Skype, Snapchat, Telegram, TikTok, Tinder, Tumblr, Twitter, Viber, the Russian social network VK, WhatsApp, WeChat and YouTube.
Just like many kinds of malware out in the wild, BlackRock disguises itself as legitimate apps from a wide range of categories, including business, messaging, dating, entertainment, finance, lifestyle, news, social media and more.
BlackRock works by abusing Android's Accessibility Service privileges, for which it seeks users' permissions under the guise of fake Google updates when it's launched for the first time on the device.
What this means, when installed, it asks users to grant various and excessive permissions. If granted, it can start steal device data without its victims' knowledge.
“When the malware is first launched on the device, it will start by hiding its icon from the app drawer, making it invisible to the end-user. As [a] second step it asks the victim for the Accessibility Service privileges,” wrote the researchers in a blog post.
“Once the user grants the requested Accessibility Service privilege, BlackRock starts by granting itself additional permissions. Those additional permissions are required for the bot to fully function without having to interact any further with the victim. When done, the bot is functional and ready to receive commands from the C2 [command-and-control] server and perform the overlay attacks.”
BlackRock can also redirect victims to the home screen of the device, whenever they try or start antivirus apps.
A specific list of antivirus apps that BlackRock can anticipate, include Avast, AVG, Bitdefender, ESET, Symantec, Trend Micro, Kaspersky, McAfee, and Avira. What's more, utility apps designed to clean Android devices, like TotalCommander, SD Maid or Superb Cleaner, are also rendered useless.
To prevent BlackRock, users should make sure that they download apps only from reputable sources, like Google Play Store, always read app reviews, and use unique passwords, as well as check for app permissions.
Related: How The Demise Of A Banking Malware Gave Birth To A Vicious Password-Stealing 'Alien'