
One of the most sensitive things that people should keep away from anyone, is passwords. This is why hackers are doing whatever they can to get their hands on them.
This time, researchers have discovered a strain of Android malware that is capable of stealing passwords from Google, Facebook, WhatsApp and more than 200 other apps.
It can even steal Google Authenticator two-factor authentication codes, steals contact lists, acts as keylogger, and install malicious apps.
Making things worse, the malware can also give hackers a near-total control of victims' phone, when it's granted administrative rights..
The ultimate goal of this malware, is to steal online accounts, especially bank accounts, in order to steal money out of them.
This vicious malware is dubbed the 'Alien', a variant of the Cerberus banking trojan, which went open-source in August, following issues by the malware authors.
According to ThreatFabric on its blog post:
The post advertised a kind of malware with VNC (Virtual Network Computing). This kind of malware is often extremely dangerous, as it can be a trojan capable of remote access capabilities (RAT).
Digging deeper, the team matched the fact that the samples did include RAT feature, and relatable codebase to Cerberus.
However, there was a conflict: this new RAT and Cerberus were operated by a separate group. Curious, the team decided to investigate further, and found what was going on weeks later.
This was when the team found that an actor, who later proclaimed himself author of the 'BlackRock' malware, left a review on the profile of the RAT author, reviewing his malware-rental service.
"After we established a solid link between the actor running the private rental service and the samples, the only aspect we were missing was the name of the Trojan. Fortunately for us, after a while topics showing interest in a certain 'Alien' malware started to appear in the underground forum and the author himself confirmed his affiliation to, and the name of, the Trojan."
The team speculated about what had happened Cerberus and Alien, saying that Cerberus was on the decline as the developers behind the trojan shifted away from the project with the original source in order to start their own.
The result is the Alien trojan, which was born from the demised of the popular banking trojan.
But this is where the similarities end.
The Alien malware offers more-than-average capabilities of Android banking Trojans. Among the aforementioned abilities, the malware can also steal notification from infected devices, abusing TeamViewer app to plant its RAT, and more.
This Alien embeds itself inside fake fitness apps, fake Flash Player apps, fake coronavirus-related apps, and even fake versions of Google Update.
ThreatFabric speculates that the apps are mainly distributed via malicious websites and through SMS text messages.
Upon installation, Alien-infected apps will always ask for intrusive permissions in order to get administrative privileges on victims' phone.
If users grant the permissions the malicious app asks, the malware can then process in doing what it's designed to do.
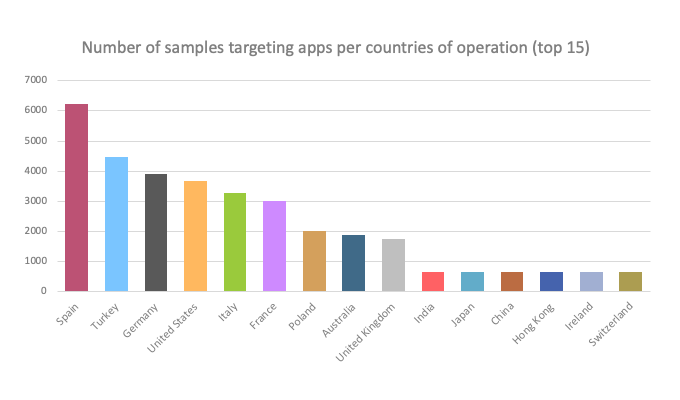
Among the more than 200 apps targeted by the Alien malware, include leading banking apps, as well as some cryptocurrency apps.
What's more, it was also found on many widely-used online services, including Amazon, AT&T, eBay, Facebook, Gmail, Google Play, Google Play Games, Instagram, Netflix, Outlook, PayPal, Skype, Snapchat, Telegram, Twitter, USAA, Viber, WhatsApp and Yahoo! Mail.
This is why the team at ThreatFabric echoes what other security researchers have said in the past: never download apps outside the Google Play Store, and never grant administrative privileges to some random apps, unless there is a very specific reason for the app to have them.
"Once again, 2020 shows interesting changes to the mobile threat landscape," the team at ThreatFabric said.
"More and more Trojans embed features that enable the criminals to take remote control of the infected device (RAT) - like the Alien Trojan itself - in order to perform the fraud from the victim’s device."
The team "strongly recommend all financial institutions to understand their current and future threat exposure and consequently implement the relevant detection and control mechanisms."