What's on people's phone should stay on their phone. Private and personal conversation should never be exposed for whatever reason.
But Go SMS Pro, the Android messaging app from developer GOMO that has more than a hundred million installs on Google Play Store, seemed to have missed that memo.
Researchers at the firm TrustWave found that the app has a massive flaw, where files sent as attachments via the app can also be viewed in public.
This happened because not only that files would go from the sender to the recipient, as Go SMS Pro would also upload the files to the web, with auto-generated, publicly accessible URLs.
This is a big mistake.
While it is said that it wasn’t possible to target any specific Go SMS Pro user, "an attacker could abuse this weakness to view other users’ media content without authorization," wrote TrustWave on its report.
Go SMS Pro in generating accessible URL for photo, video or other file can come in handy when a user wants to send something to someone who doesn't have the app installed. This way, the user can instead share a web address by text message so the recipient can see the file without installing Go SMS Pro.
However, the app also generates web addresses any time a file was shared, even between app users.
The issue here, happens because the URLs the app generates are publicly accessible.
This is a big issue because this allowed anyone with an internet connection and the knowledge to retrieve those files.
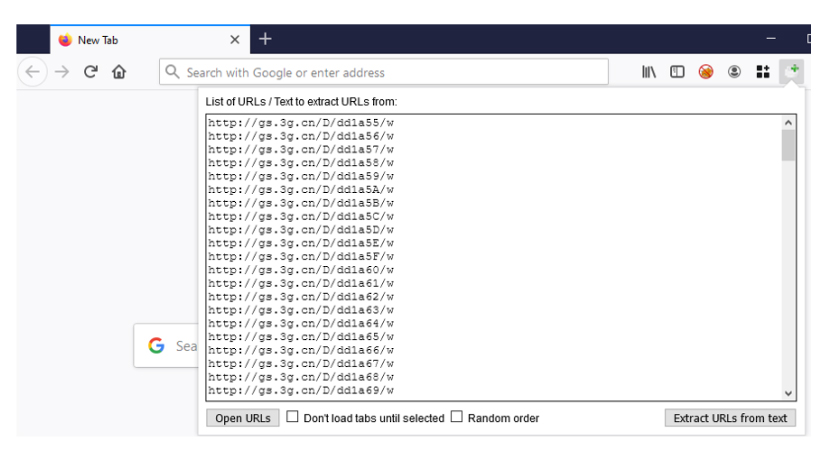
This is an even bigger issue because the app generates sequentially-ordered URLs.
What this means, anyone who knew about the predictable web address could have cycled through millions of different web addresses to see and download users' files.
Because of this, the researchers were able to retrieve sensitive financial information, home addresses, transaction receipts, arrest record and explicit photos that had been sent through the app.
That’s a huge privacy issue, but what’s most alarming is that Go SMS Pro’s developers don’t appear to be rushing to fix the issue.
When the researchers at Trustwave alerted the developers of the issue in August 2020, no one responded.
TrustWave made four more attempts, all of which were also unsuccessful. Some media companies also tried contacting the developer, also to no avail. Emails were either ignored, or returned to the sender due to "full inboxes."
TrustWave gave the app maker GOMO a 90-day deadline to fix the issue, as it's already a standard practice in vulnerability disclosure to allow enough time for a fix.
But because the deadline elapsed without TrustWave hearing anything from the developer, the researchers decided to disclose the issue to the public.
What comes later was that, GOMO, the developer behind Go SMS Pro, took the app down from the Google Play Store. GOMO's website has also been taken down.
Making things worse, there is nothing users can do about the files that they've sent using the app that were uploaded to the internet, unfortunately.
With all of the above reasons, Go SMS Pro checks all of the do not recommend boxes. Those who have installed Go SMS Pro are urged to stop using the app and delete it.