
As sneaky as it can be, malware comes in various forms.
And one of the most dangerous of them all, is the ones that can steal sensitive data, and use that data to steal even more data. And the 'Chameleon' malware, fits this trait, as it packs powerful features, including the ability to bypass Android fingerprint and face locks.
The Chameleon Android malware is a banking malware, first discovered earlier this 2023.
Its primary focus, was targeting mobile banking applications in Australia and Poland, before expanding to other countries.
It was originally meant to impersonate government agencies, banks, and a cryptocurrency exchange, performing keylogging, overlay injection, cookie theft, and SMS theft on compromised devices.
At first, it uses multiple loggers, had somewhat limited functionality, and contained various unused commands, suggesting that it was still under development.
This time however, the Chameleon has evolved.
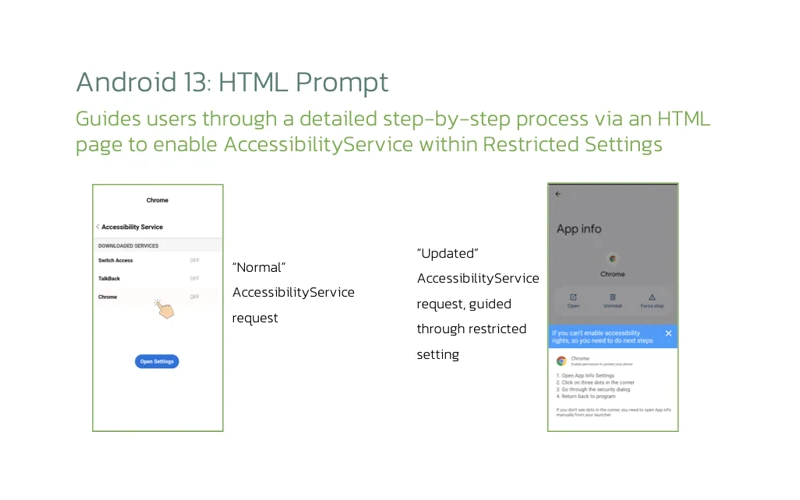
According to researchers from ThreatFabric, the malware is tricking people into turning on accessibility services, which then allows attackers to change the phone from a biometric to a PIN lock.
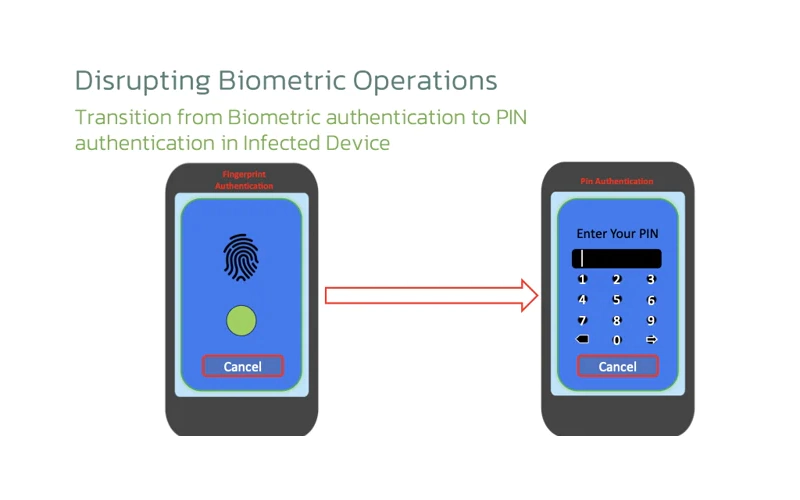
It does this by posing as legitimate Android apps and then displaying an HTML page that asks potential victims to turn on accessibility settings. When biometric is off, attackers can then attempt to bypass the protection by making the phone to use a PIN or password to unlock.
When the victim inputs this sensitive information, the attackers can then steal it.
Then malware can disrupt the phone's biometric operations by employing the KeyguardManager application programming interface and AccessibilityEvent, an Android system-level event that provides information about changes in the user interface to assess the screen and keyguard status.
Keyguard in Android is a system component responsible for managing device security, such as screen lock and authentication mechanisms.
Once the victim is tricked, the malware can then perform unauthorized actions on the user’s behalf.
When this Chameleon variant is installed to a victim's phone, it will start by scanning to see if the Android version installed is version 13 or newer, before doing any of the actions.
According to the researchers, the enhancements elevate the sophistication and adaptability of the new Chameleon variant, making it a more potent threat in the ever-evolving landscape of mobile banking trojans.
"This banking trojan displayed a distinctive capability to manipulate a victim's device, executing actions on the victim's behalf through a proxy feature. This feature enables advanced maneuvers like Account Takeover (ATO) and Device Takeover (DTO) attacks, particularly targeting banking applications and cryptocurrency services. These functionalities relied on the abuse of Accessibility Service privileges," the researchers said in their report.
In all, "the emergence of the new Chameleon banking trojan is another example of the sophisticated and adaptive threat landscape within the Android ecosystem," the researchers concluded.
"Evolving from its earlier iteration, this variant demonstrates increased resilience and advanced new features."
To avoid being infected, users should use common sense when installing apps, such as never install apps from dubious unofficial sites and employing security measures such as Play Protect, a security feature on Android devices that scans and verifies apps to prevent the installation of harmful software.