
Instant messaging has become a must in the modern era of technology.
From messaging apps with tons of features and gimmicks, to straightforward messaging apps, the market has it all. But what hackers know is that, people who care for privacy and wish to speak about sensitive information, tend to use privacy-focused messaging apps.
Two of the most famous messaging apps for this purpose, include Telegram and Signal.
This is why hackers are developing a specialized Android malware called 'BadBazaar', and disguising their spyware by creating a trojanized versions of the two popular, privacy-focused messaging apps.
Cybersecurity researchers have warned that state-back hackers are orchestrating a large-scale espionage operation to eavesdropping on private messages.
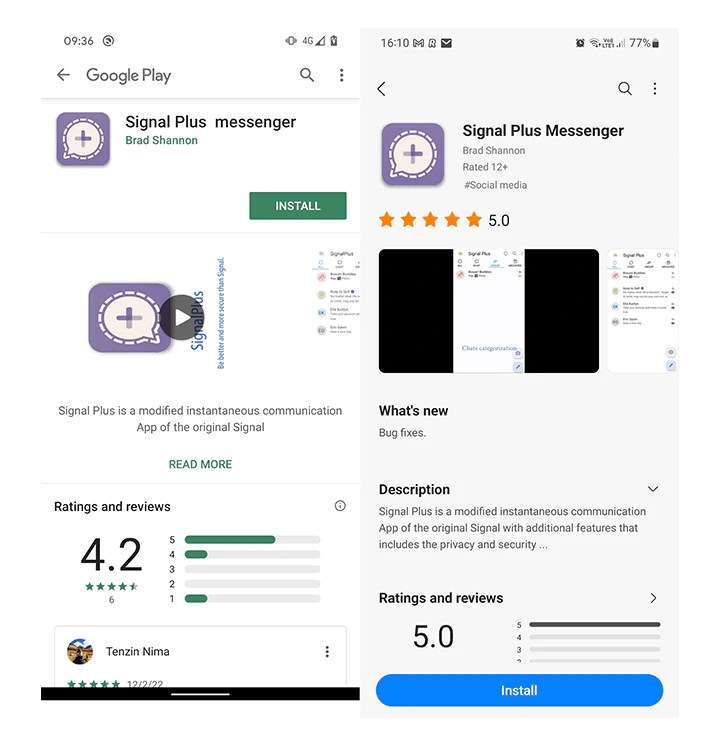
In a report by cybersecurity firm ESET, the researchers unveiled the two deceptive apps, masquerading themselves as "Signal Plus Messenger" and "FlyGram."
Besides siphoning messages, the apps can also list of all Google Accounts on a compromised Android device, steal device information and a get comprehensive list of installed apps. The apps in question can also gather targeted sensitive information, like contact lists and call records.
To lure people into downloading that apps, the malicious developers created the app to have features and modifications that not available with the official versions.
The two apps are not some ordinary apps, because of their well-developed potential and abilities.
FlyGram, the fake Telegram, for example, is capable of extract some basic metadata from Telegram apps and access a user's full Telegram backup - including contacts, profile pictures, groups, channels, and other information.
And as for the malignant Signal Plus Messenger, the app can tap into victims' Signal messages by bypassing the conventional QR-code linking process, in order to connect the compromised device to the attacker's without detection.
"This spying approach stands out due to its uniqueness, as it differs from the functionality of any other known malware," ESET said.
Signal Plus Messenger collects the same kind of device and user information as FlyGram, but its main function is to spy on the user's Signal communications.
"For specific individuals and enterprises, the impact can be huge, considering FlyGram is capable of not only spying on users but also downloading additional custom payload and making users install them," Štefanko notes. "Malicious Signal Plus Messenger, on the other hand, allows active espionage on exchanged Signal communication."

What's chilling is that these fake apps is that, they were distributed via trusted platforms, including Google Play Store and Samsung Galaxy Store.
The researchers said that BadBazaar can be linked to the Chinese hacking group, the notorious GREF, which has been using the malware to target Uyghurs and other Turkic ethnic minorities, both domestically and abroad.
But in this case, ESET has found nothing to suggest that GREF is using the malware to target specific groups or individuals, Štefanko said.
Signal Plus Messenger and FlyGram were built by merging the BadBazaar espionage code, previously used to target #Uyghurs and other #Turkic minorities, into the respective base app’s code. 2/9
— ESET Research (@ESETresearch) August 30, 2023
By putting the two apps inside the legitimate app stores, the campaigns have left a trail of victims across the globe, from Australia to the U.S., as well as victims in Brazil, Germany, and Hong Kong.
Following ESET's findings, Google took swift action and removed the malicious apps from the Google Play Store. The Signal app garnered a few hundred downloads, while more than 5,000 users downloaded FlyGram from Play before Google removed it.
However, following Google's move Samsung was way behind because there was no immediate response from the South Korean company.
It's worth noting that Signal Plus Messenger and FlyGram campaigns have been active since at least July 2020 and July 2022, respectively, according to ESET.
What's also worth noting, besides being attributed to GREF, the BadBazaar malware has also been attributed to China-based APT15, aka Vixen Panda and Nickel.
ESET however, cannot conclusively establish that link. What's certain is that the telemetry related to the malware, the trojanized apps, and the threat infrastructure, all point to BadBazaar being the handiwork of GREF.