With people becoming more dependent to the internet, providers are doing whatever they can to meet those high demand.
As a result, internet connection is becoming more abundance. There are even many that offer 'free hotspots' to whoever wish to connect. Life is never easier, and unfortunately, also never scarier.
While computers and mobile devices have become better and better in protecting their hardware and software from malicious attacks, their protection capabilities can be rendered next to useless if users don't take precautions for themselves.
And one of the cases here, is disabling one particular feature that deals with Wi-Fi.
People should be well aware of the dangers of using public Wi-Fis. These hotspots can be found in many places, like inside airports, shopping malls, coffee shops, stores, hotels, and even on the streets.
While many of them require password to connect, or require users to enter its portal first before doing anything, many others are free to use.
Anyone can join, anyone can be connected to the internet instantly. But that is where the problem starts.
The problem can start as soon as when people connect their devices to public Wi-Fi.
When a device connects to a Wi-Fi, it relies on the network’s service set identifier, or SSID for short, in order to pick a live connection. In public Wi-Fi networks, this SSID is often the name of the place or location. Like for example, the name of the hotel the public Wi-Fi is offered.
This is done for the purpose of keeping things simple.
The problem happens when users' devices are configured to automatically connect to known hotspots.
When devices are configured this way, they will automatically connect to Wi-Fi networks they recognize, every time the Wi-Fis are in range. Again, this is intended as a convenience.
But that simple convenience is a significant security risk that people must address.
First, people can never know who is behind that public Wi-Fi. It can be portable device, a mobile phone, a fixed router, or others. Second, it can be owned by anyone, and can be placed anywhere. And third, besides being hard to trace, they can be also turned off instantly.
The attack vector that people should worry, is called the 'evil twin attack'. It's the wireless LAN equivalent of the phishing scam.
The attack goes on like this: attackers attempt to make victims connect to their Wi-Fi network, by simply setting up their own Wi-Fi hotspots to have the same SSID as what the victims have previously used.
For example, someone who has his/her device set to automatically connect to known hotspots, and has previously connect to a hotspot in a hotel, attackers can have that device to automatically connect to their network when the victim is in range, by making their network to have the same SSID as the hotel's.
One of the most commonly used attacks using this 'evil twin attack', is by using a captive portal:
Attackers would create a fake wireless access point that has a similar SSID or other legitimate access point. After that, the attackers would then launch a Denial-of-Service attack to the legitimate access point to make it go offline.
This way, users who connect to the legitimate network would disconnect because the access point crashes. If users have set their devices to automatically connect to known network, their devices will scan for known networks, and quickly pick the attackers network to connect to.
Those users would then become victims.
Making things worse, many people set their devices to constantly look for familiar Wi-Fi networks by continuously send out probes for hotspots it is looking to connect to, meaning that they can be constantly vulnerable.
So what can happen when hackers can have victims to connect to their "free" public Wi-Fi.
As a start, it's possible for them to extract information. This can be done by eavesdropping for packets, or push phishing pages, or more. This 'evil twin attack' can also be used to steal passwords, monitor victims' connections, and more.
According to the FBI, there are some signs to look for when attempting to know whether or not a device has been compromised.
People can protect themselves by using a VPN, for example. By creating an encrypted tunnel to access the internet, data that is transferred to the World Wide Web via the malicious network will be unreadable by the attackers.
But unfortunately, many people don't use VPNs, even when connecting to public Wi-Fis. And worse, those people that do use VPNs, don't use a secure and trusted VPN.
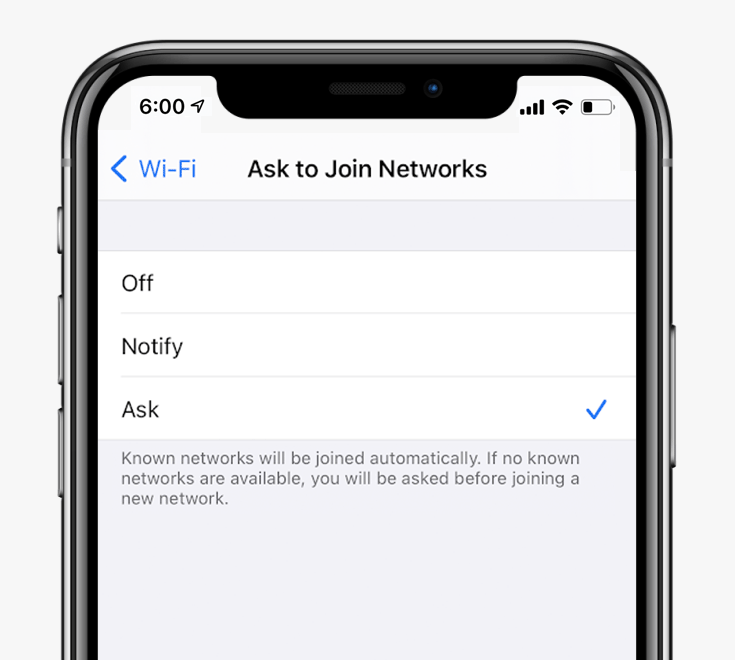
As a solution, people should at least set their devices to "Ask to Join Networks" or similar, or disable the "Auto-Join" feature. This will stop the devices to connect to new or known network or hotspots without the users realize. This configuration simply gives users an exercise option before clicking 'Yes'.