
New versions of technologies are meant to be better and more secured. However, since they are usually based on their previous iterations, flaws can be inherited.
A group of academics discovered three security flaws in 4G and 5G networks, which can be used to intercept phone calls and track the locations of mobile device users.
According to the researchers, this is the first time vulnerabilities have affected both 4G and the incoming 5G standard.
The researchers said that attackers exploiting the flaws can bypass 4G's security protections, as well as 5G's newer protections.
"Any person with a little knowledge of cellular paging protocols can carry out this attack ... such as phone call interception, location tracking, or targeted phishing attacks," said Syed Rafiul Hussain, one of the co-authors of the paper.
Making things worse, attacks can be carried out only by using radio equipments costing as little as $200.
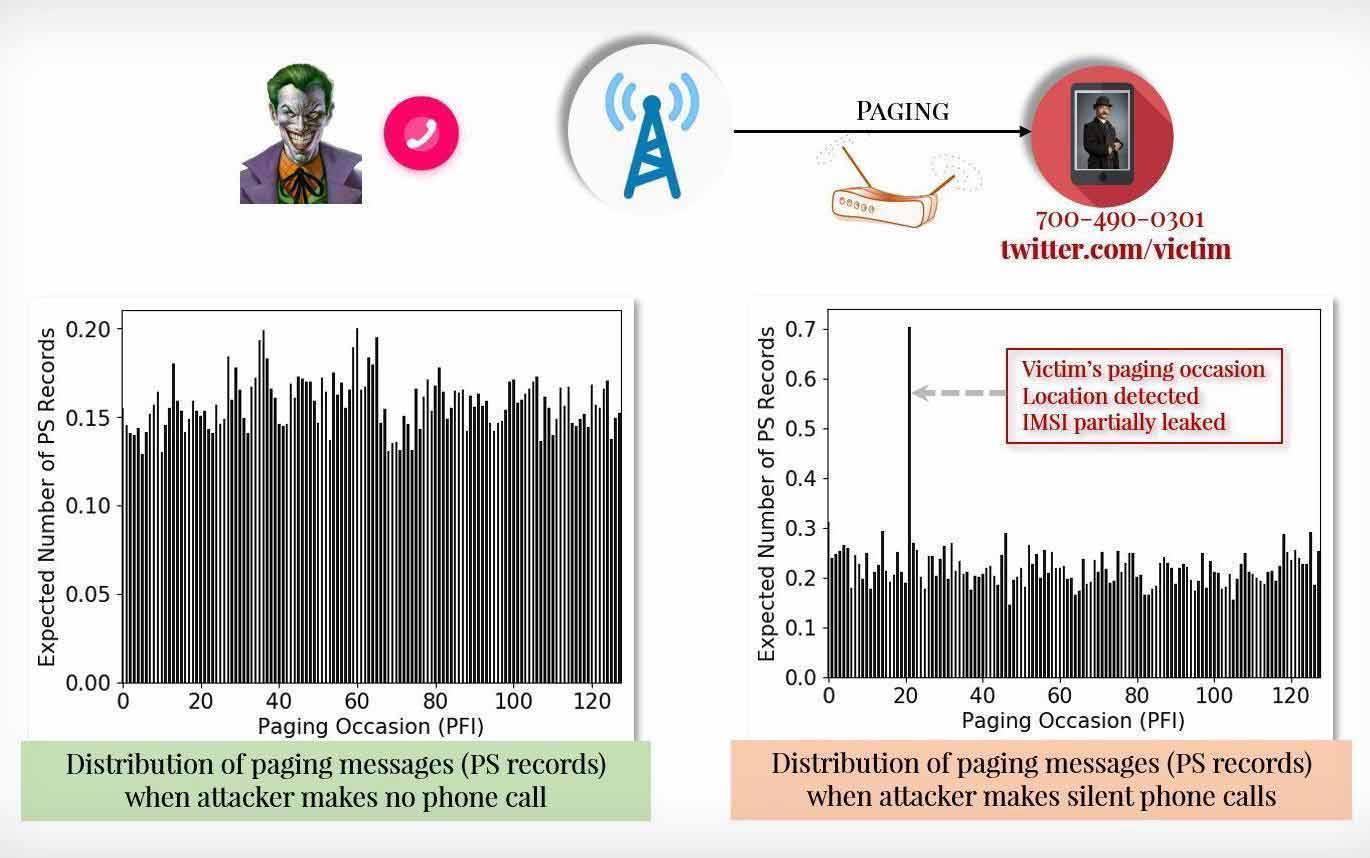
The first attack can be done using 'Torpedo' (TRacking via Paging mEssage DistributiOn), which exploits a weakness in the paging protocol that carriers use to notify a mobile devices before a call or text message is passed through.
On their research, the researchers found that when several phone calls were placed and cancelled in a short period of time, this can trigger a paging message which is created without alerting the target device to an incoming call.
This flaw allows attackers to track the victim's location.
Knowing the victim’s paging occasion also allows attackers to hijack the paging channel and inject or deny paging messages, by spoofing messages or blocking messages altogether, the researchers said.
This Torpedo flaw opens the door to two other flaws.
The first is called the 'Piercer', which the researchers say allows attackers to determine an international mobile subscriber identity (IMSI) on the 4G network. This in turn allows them to exploit the second flaw, the 'IMSI-Cracking attack', which can brute force encrypted IMSI numbers.
Given that the flaws affect both 4G and 5G networks, it can be concluded that most cellular networks are vulnerable to these attacks.
And due to the massive damage the flaws can do, the researchers decided to not release the proof-of-concept code to exploit the flaws.
According to Hussain, he said that the flaws were reported to the GSMA, an industry body that represents mobile operators.
Hussain continued by saying that both Torpedo and IMSI-Cracking flaws can be fixed by the GSMA, but as for the Piercer, it depends on the carriers to patch.
Because Torpedo is the precursor to the other flaws, Torpedo should be the priority to be fixed first.
