Quantum computing is poised to revolutionize technology, but it also presents significant challenges to cryptography – the backbone of modern digital security.
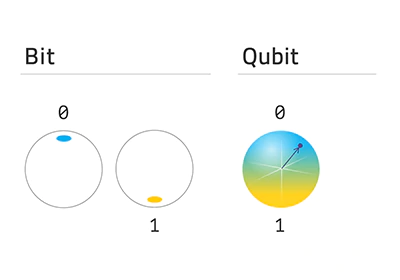
Quantum computers use quantum bits (qubits), unlike classical computers that rely on binary bits (0s and 1s). Qubits can exist in superposition, representing multiple states simultaneously, and leverage entanglement, allowing qubits to influence each other instantly over distance.
This enables quantum computers to perform complex calculations at exponentially faster rates than classical systems.
Among the key advantages of quantum computing, include, massive parallel processing, in which these computers can solve problems traditional computers would take millennia to compute.
And this is where cryptography is at a threat.

Cryptography secures communication by encrypting data, ensuring confidentiality, integrity, and authentication. Most modern-day encryption relies on mathematical problems that are extremely difficult for classical computers to solve, such as:
- RSA (Rivest-Shamir-Adleman): Relies on the difficulty of factoring large numbers.
- ECC (Elliptic Curve Cryptography): Based on elliptic curve mathematics.
- AES (Advanced Encryption Standard): Symmetric encryption for secure data exchange.
And here, quantum computing is posing a threat to cryptography, mainly because of its immense processing power.
Quantum computers have the potential of rendering modern cryptographic systems vulnerable.
Algorithms that are practically unbreakable today could be cracked in seconds by large-scale quantum machines.
Key risks include, and not limited to:
- Breaking public key cryptography.Compromising data Integrity.
- Risking digital signatures.
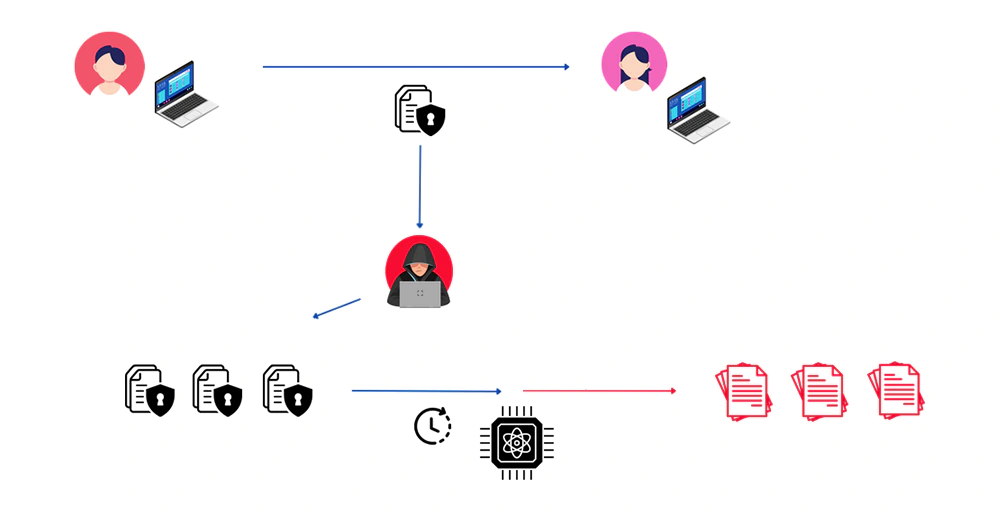
Before hackers can get their hands on a working, commercial, and capable quantum computer, the term "harvest now, decrypt later" is gaining a lot more attention.
Or also known as "store now, decrypt later" or "steal now, decrypt later," it's a term to describe a surveillance tactic involving the collection and long-term storage of encrypted data that cannot currently be deciphered.
The goal is to retain a data until advancements in technology, such as future breakthroughs in quantum computing, make it possible to unlock whatever is decrypted in it to read the information within.
The hypothetical point at which this occurs is often referred to as Y2Q (Quantum Day or Q-Day), drawing a parallel to the Y2K phenomenon.
The primary concern surrounding this strategy is the potential for quantum computers to break today's strongest encryption algorithms, making previously secure communications and data vulnerable to decryption. This means that sensitive material encrypted today could be exposed years later once quantum technology becomes viable.
Hackers are increasingly harvesting data just to store them, because they know that encryption is the foundation of modern technology, safeguarding critical aspects of everyday life.
Financial systems depend on RSA encryption to protect online transactions, ensuring sensitive data like credit card details and account information remains secure. Without encryption, online banking would not exist.
E-commerce also relies on encryption to shield payment data as it moves between buyers and sellers. Without it, digital commerce would collapse.
Healthcare systems use encryption to transfer electronic health records (EHRs) and process patient payments securely. Without it, modern medical infrastructure would falter.
Encryption is equally vital for government agencies, protecting classified communications and preserving national secrets. Without encryption, national security would be compromised.
Even Internet of Things (IoT) devices – from smart homes to connected cars – are safeguarded by encrypted commands, preventing hackers from hijacking everyday technology. Without encryption, smart devices would be vulnerable and unsafe.
The idea harvest now, decrypt later is simple: intercept and store encrypted data today, even if it can’t yet be decoded, hoping that one day quantum advancements may break current encryption standards, turning stored data into valuable intelligence.
Hackers are willing to do this because some data remains valuable even decades later – particularly state secrets, military intelligence, or encryption keys reused across systems.
In sensitive sectors like defense, intelligence, and critical infrastructure, adversaries are likely collecting encrypted data now, anticipating future breakthroughs.
The rise of this harvest now, decrypt later tactic has fueled global efforts to accelerate the adoption of post-quantum cryptography (PQC), which aims to create encryption techniques resistant to quantum attacks.
Examples of PQC include:
- Lattice-Based Cryptography.
- Hash-Based Cryptography.
- Code-Based Cryptography.
- Multivariate Polynomial Cryptography.
Whereas current cryptography tactics are based on problems like integer factorization and discrete logarithms. This method is proven difficult for classical computers but vulnerable to quantum attacks.
PQC tactics on the other hand, leverage mathematical problems that are hard for both classical and quantum computers, such as lattice problems, multivariate equations, and error-correcting codes.
