
Internet-connected devices face threats that are more than plenty. And Microsoft Defender is one sitting at the line of defense.
Microsoft Defender is an antivirus and anti-malware solution built into Windows operating system. It has evolved from a downloadable program to a full-fledged security tool, replacing Microsoft Security Essentials.
And Microsoft Defender for Endpoint is a "cloud delivered endpoint security solution that includes risk-based vulnerability management and assessment, attack surface reduction, behavioral based and cloud-powered next generation protection, endpoint detection and response (EDR), automatic investigation and remediation, managed hunting services, rich APIs, and unified security management."
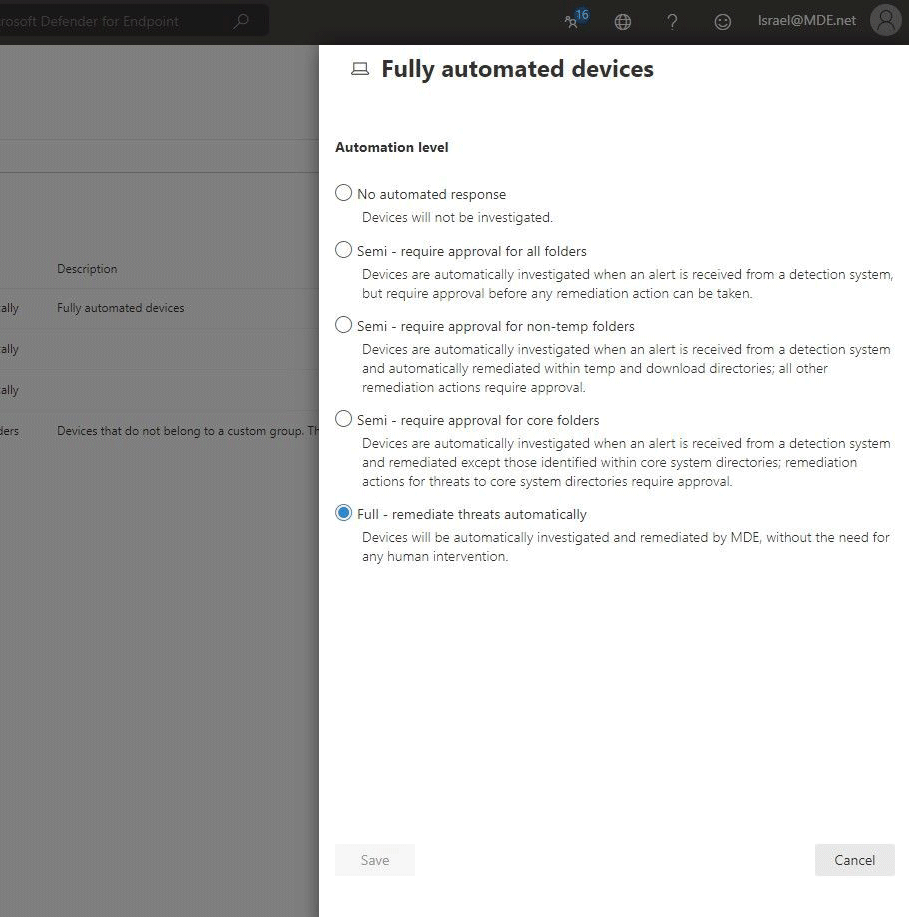
Users of Microsoft Defender for Endpoint can set the tools to default to 'Semi' or 'Full' in their protection mechanism. But according to Microsoft, the company found that using full automation by default is more successful in remediating and containing threats.
"Data collected and analyzed over the past year shows that organizations who are using full automation have had 40% more high-confidence malware samples removed than customers using lower levels of automation," Microsoft explains.
"Full automation also frees up our customers’ critical security resources so they can focus more on their strategic initiatives."
This is why Microsoft wants to enable fully automated threat remediation by default for Microsoft Defender for all Endpoint customers who have opted into public previews starting February 16, 2021.
According to Microsoft on its web page:
"The result of an automated investigation started by an alert is a list of related entities found on a device and their verdicts (malicious, suspicious, or clean)."
When remediation is set to default, Microsoft Defender for Endpoint can remove or contain a malicious entity it finds, without user intervention.
What this means, the process will commence automatically, without the organization's security operations team having to remotely connect to the device or having to wait for the remediation action to be approved.
"These actions are defined, managed, and executed by Microsoft Defender for Endpoint without the security operations team having to remotely connect to the device," explained Microsoft.
The change comes after Microsoft has increased malware detection accuracy, upgraded its automated investigation capabilities, and added an option to undo remediation actions.
Since automated investigation and remediation capabilities were first added to Microsoft Defender for Endpoint, Microsoft found that organizations with fully automated tenants have been able to successfully remediate and contain threats while tenants with semi-automation were left waiting for manual approval.
"We have seen thousands of cases where organizations with fully automated tenants have successfully contained and remediated threats, while other companies, left with the default 'semi' level, have remained at high risk due to lengthy pending time for approval of actions," said Microsoft, adding that customers have had "40% more high-confidence malware samples removed than customers using lower levels of automation."
"The new default automation level can be kept (this is recommended) or changed according to your organizational needs," Microsoft added.
To start using Microsoft Defender for Endpoint public preview capabilities, customers have to manually toggle on the preview features in the Microsoft Defender Security Center.
By switching to full auto, this should leave security operations centers with more free time to deal with other more important things that really require human intervention.
"This change does not impact or override device group definitions that were previously set to control automation level."
