
Tor has long been the refuge for people who need to move through the internet without leaving a trail.
Activists, journalists, researchers, whistleblowers, or simply anyone who refuses to be profiled, tracked, or monitored have relied on it for years. What began as a U.S. Naval Research Lab project grew into a global privacy network maintained by volunteers and supported by a community that believes anonymity is a right, not a luxury.
Over time, Tor Browser became the most accessible doorway into that network, wrapping powerful anonymity technology inside something anyone can use: a familiar, Firefox-based browser that leaves no breadcrumbs behind.
Across its lifetime, Tor Browser kept evolving while holding fiercely to its principles.
Each new version tries to balance modern browser features with strict privacy safeguards. That march forward continues with the major leap to Tor Browser 15.0, followed closely by its security-focused sibling update, Tor 15.0.1.
Together, they show how the project is modernizing without loosening its grip on user protection.

Tor Browser 15.0 marks the first stable release based on Firefox ESR 140, bringing in a year’s worth of upstream improvements.
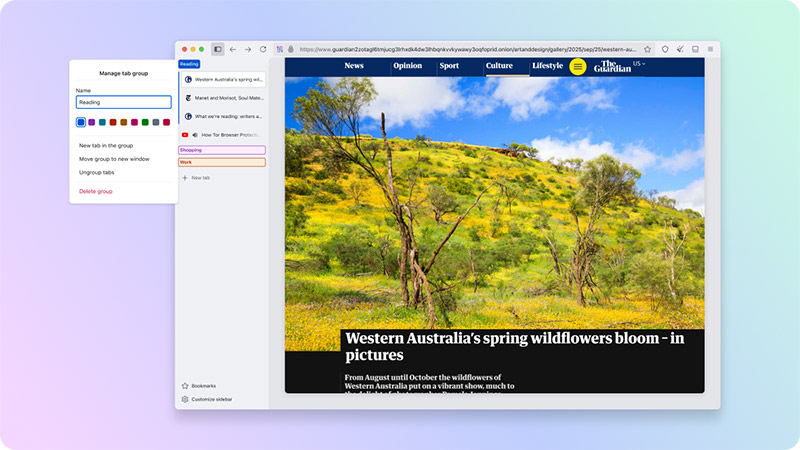
For desktop users, the most noticeable additions are vertical tabs, tab grouping, and a unified search button, features that make everyday browsing feel smoother even though every session still resets when the browser closes. Tor’s tabs remain strictly private, wiping themselves clean so no session data lingers.
Yet for researchers, analysts, and users who tend to accumulate a forest of tabs, these new organizational tools offer a bit of breathing room before everything is cleared away.
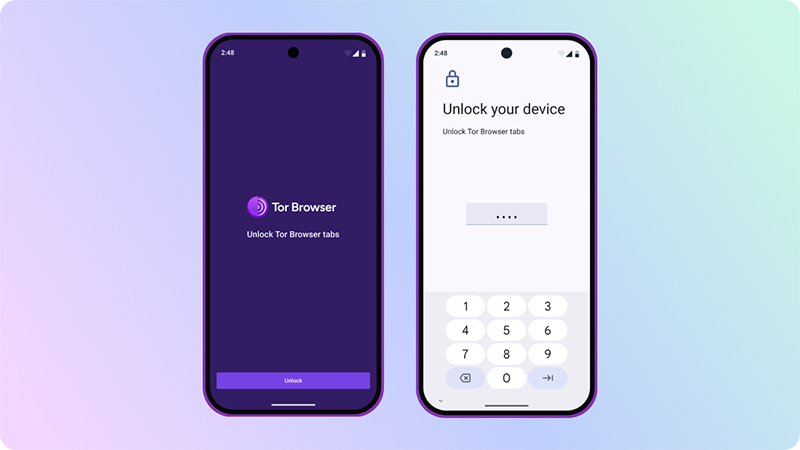
The Android release received its own meaningful upgrade: a built-in screen lock. Anyone who hands their phone to a friend or leaves it on a table for a moment now has an added layer of protection, as returning to Tor Browser can require authentication.
Like the desktop version, Android now also clears the session when the app closes, reinforcing Tor’s principle of starting every session fresh.
This release also represents a turning point in platform support.
Tor Browser 15.0 is the final major version for 32-bit Linux and older Android versions (5, 6, and 7). By the time Tor Browser 16.0 arrives in 2026, those systems will no longer receive new features.
The decision echoes Mozilla’s own support changes and reflects growing technical limitations, especially for Android devices constrained by strict app size limits.
Another important shift lies in how Tor handles WebAssembly.
Previously, Wasm was disabled entirely at higher security levels, which caused issues when Firefox revamped its PDF viewer to rely on it. Tor now delegates Wasm blocking to NoScript, allowing internal components like the PDF reader to function correctly while still preventing Wasm execution on websites at safer settings.
This keeps users protected without breaking core browser features.
Behind the scenes, Tor developers also completed a rigorous ESR transition audit, reviewing around 200 Firefox bug reports to ensure that nothing introduced upstream weakens Tor’s threat model.
This audit is part of what makes Tor different from a standard privacy browser; every inherited change is checked, questioned, and adapted with anonymity first in mind.
The team’s stance on embedded AI features is another example of that philosophy.
Firefox’s recent direction toward integrating machine-learning tools didn’t align with Tor’s mission. These systems often require cloud communication, accounts, or opaque data handling. These are all incompatible with anonymity. In the alpha builds leading up to Tor Browser 15.0, the Tor Project removed these AI integrations completely, reaffirming that the browser should never include features that can’t be independently verified or that expose users to new fingerprinting risks.
Shortly after 15.0 came out, Tor Browser 15.0.1 followed with critical security fixes. This update backported important patches from Firefox 145 and ESR 140.5.0, ensuring Tor users stay protected from fresh vulnerabilities. It also included an upgraded NoScript release, improved search engine handling, restored more readable fonts on Linux, and fixed quirks like zoom settings resetting unintentionally.
Android’s underlying GeckoView engine was updated as well, bringing performance and stability gains.
Even the little things matter in a browser built for anonymity.
Tor developers refined signing tools, improved build systems, and updated bundled components like Go to keep the entire software chain trustworthy.
Together, these updates show a project that isn’t standing still.
Tor began as a research experiment, matured into a haven for people who need to stay unseen, and today continues pushing forward, carefully, deliberately, and always with privacy at its core.
