Internet-connected devices are becoming common, as people start to see their benefits. But not many people know how these devices work behind their back.
IoT, OT, networking and IT devices can connect to the internet through foundational connectivity components. And it seems that many of the components they use have zero-day vulnerabilities, four of which are critical and allow remote code execution.
According to Forescout Research Labs, 33 zero-days are impacting four widely used open source TCP/IP stacks. Dubbing them collectively as 'AMNESIA:33', the vulnerabilities reside in uIP, FNET, picoTCP and Nut/Net.
These vulnerabilities affect multiple components of the four TCP/IP stacks, including DNS, IPv6, IPv4, TCP, ICMP, LLMNR and mDNS.
And because the libraries are free-to-use and fully open source software, they have become pretty popular over the years. What this means, the AMNESIA:33's impact can be very worrying.
The researchers at the cybersecurity firm Forescout has detailed how the 33 security flaws that are present in the libraries could create catastrophic consequences for millions of devices, ranging from smart home gadgets to and industrial tech, to devices in hospitals, retailers, and even those in federal buildings.
On its report, the researchers wrote that the vulnerabilities cause memory corruption and can be exploited for:
- Remote code execution (RCE) to take control of a target device.
- Denial of service (DoS) to impair functionality and impact business operations.
- Information leak (Infoleak) to acquire potentially sensitive information.
- DNS cache poisoning to point a device to a malicious website.
The researchers said that AMNESIA:33 hasn’t been exploited out in the wild yet as far as they know.
But if it ever happened, the researchers said that hackers could benefit from a clear communication path to a vulnerable device, allowing them to exploit more of the flaws to launch a denial-of-service attack, steal sensitive information, opening device to remote code execution and more.
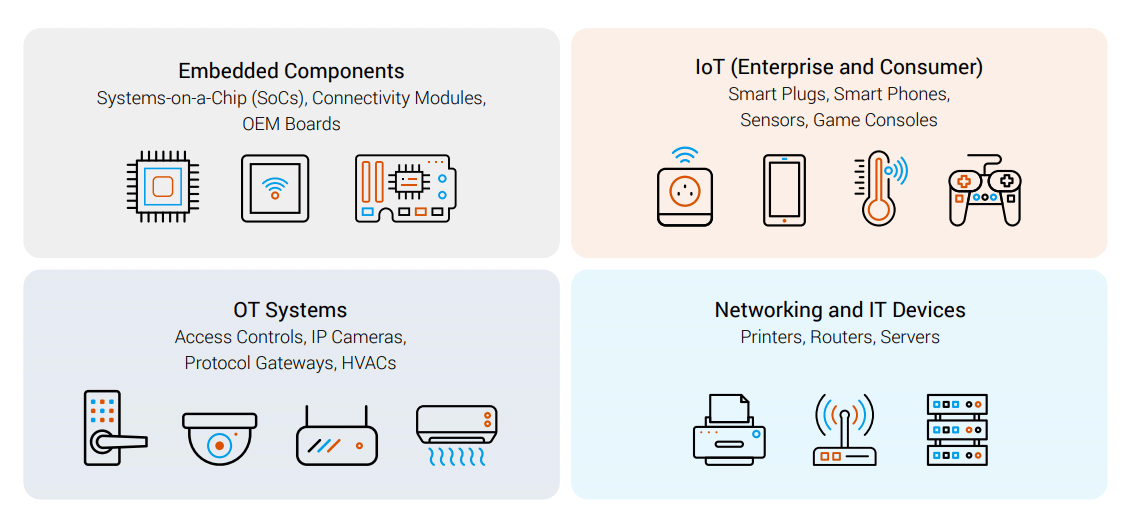
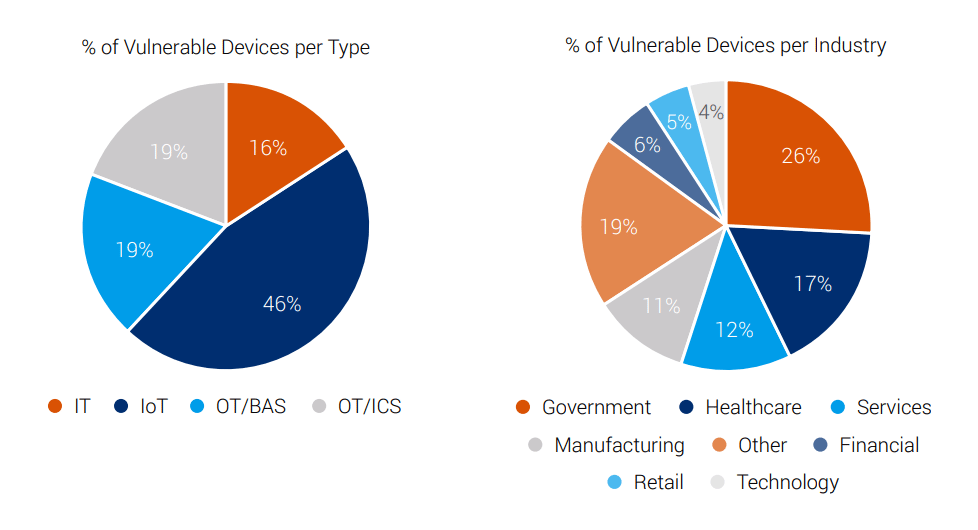
To get a better understanding about the number of affected devices, the researchers at Forescout tapped into data from both its customer base, and also from IoT search engines like Shodan and Censys.
In total, the team counted devices from over 150 vendors at risk for this particular raft of exploits, but suggested that getting the full scope of this issue is difficult because there’s so many devices in so many categories that rely on these particular code libraries.
"While it is difficult to assess the full impact of AMNESIA:33, we estimate more than 150 vendors and millions of devices worldwide are vulnerable," said the researchers.
"Since these open source stacks are widely used in embedded components, they exist in devices used in most modern enterprises. Affected devices range from network switches to smart printers, environmental sensors to security cameras, self-checkout kiosks to RFID asset trackers, and badge/fob readers to uninterruptible power supplies, to name just a few."
What makes these vulnerabilities even more worrying is that, patching them is not easy.
As the Forescout team explained in a ThreatPost post, component manufacturers have spent the decades plugging different parts of these four free-to-use libraries into code bundles of their own - which then end up inside devices.
But because of a broken link in the supply chain, device manufacturers using off-the-shelf parts may not realize the presence of the vulnerabilities on the libraries they're sourcing.
"While IoT and OT devices bring undeniable benefits to the modern enterprise in terms of automation, efficiency and powering new services, they present unique challenges for vulnerability and patch management," the researchers said.
"The long and fuzzy nature of the supply chain may not be evident at first glance."
"Even if the supply chain is well understood, patch management may be a challenge because of a broken link in the supply chain."
This is unlike traditional IT devices in general, where manufacturers and vendors can and are active in patching the components. Even users of those devices can patch them very easily through updates on firmware, for example.
Forescout recommends risk assessment, relying on internal DNS servers, disabling or blocking IPv6 traffic and segment to minimize their network exposure.
But despite the best practices the researchers recommend, ultimately, this is a long-term issue that is going to get fixed slowly, if that ever happened or possible.
