
Password managers are apps that can be life savers in the digital world that requires just too many passwords to remember.
As encrypted vaults, password managers can only be accessed by a single master password or PIN. This way, instead of remembering heaps of passwords, users are only required to create and remember one single login that is hard to guess but easy to remember.
However, researchers at the University of York have found that some commercial password managers may not be as secure after all.
On their report, the researchers said that:
"These password managers were chosen after a rigorous selection process which considered popularity and features of the individual and commercial offerings of 19 password managers."
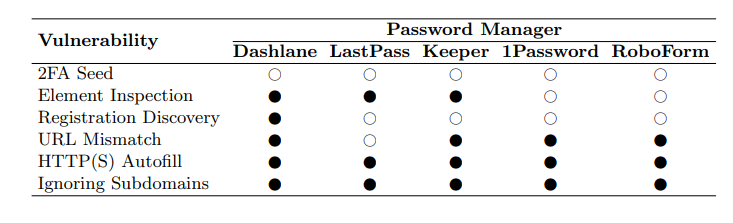
Fortunately for users, those popular password managers do frequently patch known flaws, like:
- Two-factor authentication seed vulnerability, which was disclosed for LastPass.
- Element inspection vulnerability, which leaked shared passwords through DOM element inspector tools such as Chrome’s Inspect Element, as shown in the Dashlane security analysis.
- Registration discovery vulnerability, which was a flaw in Dashlane.
- URL mismatch vulnerability, which allows autofill to fill fields with username and password despite the source and destination URLs do not match.
- HTTP and HTTPS vulnerability, which was when the autofill feature doesn't distinguish between HTTP and HTTPS when attempting to fill a credential.
- Ignoring subdomains vulnerability, where password managers simply ignore subdomains when filling passwords.
Here, the researchers found even more that are yet to be patched.
They include:
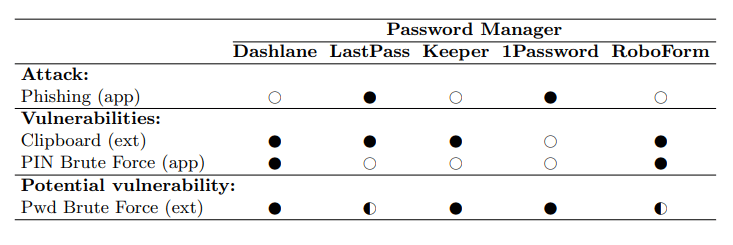
Phishing Attack
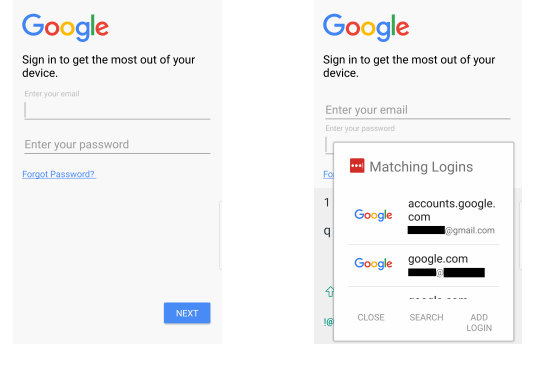
Both 1Password and LastPass for Android were found vulnerable to a phishing attack.
Both apps apparently use weak matching criteria for identifying which stored credentials to suggest for autofill. This allowed malicious app to impersonate a legitimate one, by simply crafting the package name to be identical.
In the test, the attack succeeds if two conditions are met.
The first condition is the malicious app should be first installed on the victim’s device. Hackers can do this by either getting around app store security mechanisms, or fooling the victim into sideloading the app onto their device.
The second condition, is users need to have the credentials for the target application. In this case, Google, in their vault.
Clipboard Vulnerability
A crucial usability feature of password managers is the ability to autofill users' credentials on websites.
This feature works as expected on a majority of websites. But apparently, they may occasionally don't work. And when they don't work, password managers often provide the option to copy credentials to the clipboard. And this is where the problem was found.
The researchers discovered that all of the password managers they tested, except 1Password, did not provide enough protection when users are copying sensitive items to the clipboard.
PIN Brute Force Vulnerability:
To ease authentication, some password managers on Android allow users to set a four digit PIN code to access the app. This removes the need for users to enter a long, complex master password every time they wish to enter their vault.
Here, it was discovered that both RoboForm and Dashlane Android app do not correctly implement a persistent counter on the number of times an incorrect PIN can be entered when trying to access the application.
What this means, hackers can simply launch a brute force attack to crack the master password or PIN if they have the time.
According to the researchers, brute force attack to guess a four digit PIN only takes around 2.5 hours.
Possible Brute Force via Extension:
All of the tested password managers have their respective browser extensions that enable users easy access to their vaults.
In the test, the researchers found that Keeper, Dashlane and 1Password might be vulnerable to a UI driven brute force attack when entering the master password. This was because the extensions did not observe any measures in place to stop the authentication process for the 10 tested unsuccessful login attempts the researchers made.
Vulnerabilities like these in the password managers provide opportunities for hackers to extract login credentials, allowing them to compromise commercial information or violating information.
That is because password managers are literally the gatekeepers to a lot of sensitive information, rigorous security analysis of password managers is crucial, as explained by senior author of the study, Dr Siamak Shahandashti from the Department of Computer Science at the University of York.
The researchers have disclosed these vulnerabilities to the companies developing those password managers.
Lead author of the study, Michael Carr, said that:
Previously, researchers from Independent Security Evaluators found that 1Password, Dashlane, KeePass, LastPass and RoboForm had security flaws that can leave some passwords exposed in users computer’s memory when the apps were in “locked” mode.
