People use password managers for reasons, and one of which is to store passwords into a single place for easier management and convenience.
While password managers are meant to be secured no matter what, a report from Independent Security Evaluators has found security flaws in five of the most popular password managers.
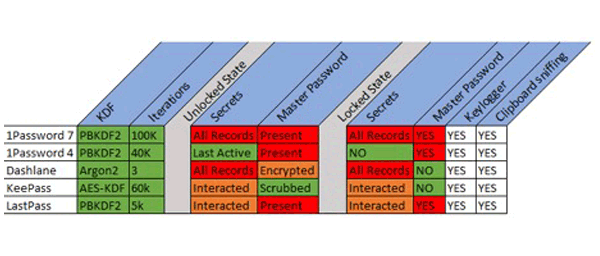
The study found that the Windows 10 apps for 1Password, Dashlane, KeePass, LastPass and RoboForm can leave some passwords exposed in users computer’s memory when the apps were in “locked” mode.
What this means, if a hacker has access to the PC, the passwords that should have been hidden, were no more secure than a text file.
Making things worse, 1Password, LastPass and Roboform even exposed users' master passwords, used to unlock all your other passwords.
"The ‘lock’ button on password managers is broken — some more severely than others," continued Bednarek.
The researchers said the flaw is present on those password managers' Windows apps, but say it may affect Apple Macs and mobile operating systems, too.

Password managers are those programs made to keep all users' login credentials in one safe place. The database file can be stored offline, or in the clouds for even better convenience.
What they these apps do, is solving one of the most annoying problem when using the internet: having to remember passwords.
With the many online services people use, it can be difficult to memorize all those login credentials. Because of this, people tend to reuse passwords, which is considered the worst mistake someone can do, besides using weak passwords.
This is so common that hackers that got their hands on one of users' login credential, will use that username-password combination on multiple other online services to see which works.
And here, password managers solve this issue by keeping track of all of users' passwords, putting them in one place. Those products can also suggest strong passwords for even better protection.
All users need to do, is to remember just one master password, and use that password to unlock all of their passwords.
The question that has haunted these programs is that: is it actually safe to put all password in one place? After all, if that master password falls to the wrong hands, it's game over.
Any exposure “puts users’ secret records unnecessarily at risk,” wrote lead researcher Adrian Bednarek in his report.
Read: Tips In Creating A Strong Password That's Hard To Guess But Easy To Remember
As for LastPass and RoboForm, they said that they would issue updates to fix this flaw. Dashlane on the other hand, said that it has documented the issue for some time and has been working on fixes, but it has higher-priority security concerns.
KeePass and 1Password however, shrugged it off as a known limitation with Windows and an accepted risk.
Password companies have some of the highest standards of security. The news highlights how the a software that is anticipated to be the most secured, can have critical flaw that makes them useless.
But still, many have urged users to keep using these password managers.
The ethical hackers at Independent Security Evaluators that found the flaw, also said that users shouldn't stop using passwords managers just because of this issue. People wouldn’t stop using a seat belt because it couldn’t protect them from every kind of vehicle accident, and this applies to password managers.
But with this finding, users should know that their password managers can be the target for malware attacks. And this is why they should bolster their defenses by:
- Updating the computers' OS and password manager whenever available, as new versions can contain important security patches.
- Using the auto lock feature on OS to prevent ‘walk by’ targeted malicious activity.
- Selecting a strong password for the master password to thwart brute force possibilities on a compromised encrypted database file.
- Checking the computer for malware using well-known and tested antivirus solutions.
- Utilizing features provided by some password managers, such as 'Secure Desktop'.
- Being very careful when installing software that comes from places other than Microsoft, Apple and Google-managed app stores.
- Never using web browser extensions, or interact with pop-up messages.
- Not storing extremely valuable information, such as Bitcoin private keys inside password managers.
- Using full disk encryption to prevent the possibility of information extraction in the event of crash logs and associated memory dumps.
- Closing a password manager down completely when not in use even in a locked state.
At the moment of the finding, the researchers found no evidence of hackers targeting the PCs of individual password manager users.
So the risk is relative. When it comes to software and the internet, there is never a guaranteed “safe” and “unsafe.” Being 100 percent safe would require disconnecting from the Internet. So here, there’s only “safer than,” or “better than."
Further reading: Developers, Inplementers And Users, The Three Parties Responsible In Securing Apps