With the internet, spying doesn't require sending a person behind the enemy lines. Instead, espionage has gone global, and hackers can do this while behind their desks, sitting halfway across the globe.
In fact, they can also do this through their laptops in a public space at restaurants, as long as there is an internet connection. Hackers can also do this while lying on their beds in their bedrooms in their pajamas.
And among the many hackers that work by preying on unsuspecting victims, North Korea hackers are among the most prominent.
In the country known for its Hermit kingdom, researchers believe that hackers there have been pushing a specialized, Trojanized version of PuTTY, in order to create backdoors on targets' network.
This way, they can spy on them, and also extract data from them.
PuTTY is a free and open-source terminal emulator, serial console and network file transfer application. It supports a number of protocols, including SCP, SSH, Telnet, rlogin, and raw socket connection. It can also connect to a serial port.
While it was originally created for users on Microsoft Windows, the utility tool has been ported to other operating systems as well, including Unix, macOS, and even Symbian.
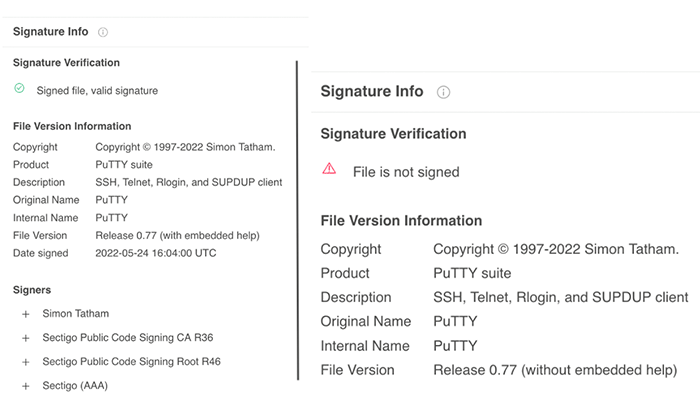
And here, according to a report by researchers from security firm Mandiant, at least one of its customers had an employee who installed a fake PuTTY by accident.
The case happened when the said the employee downloaded the fake PuTTY not from its official source.
The employee apparently failed to detect the threat, when they were contacted by someone claiming to be someone from Amazon.
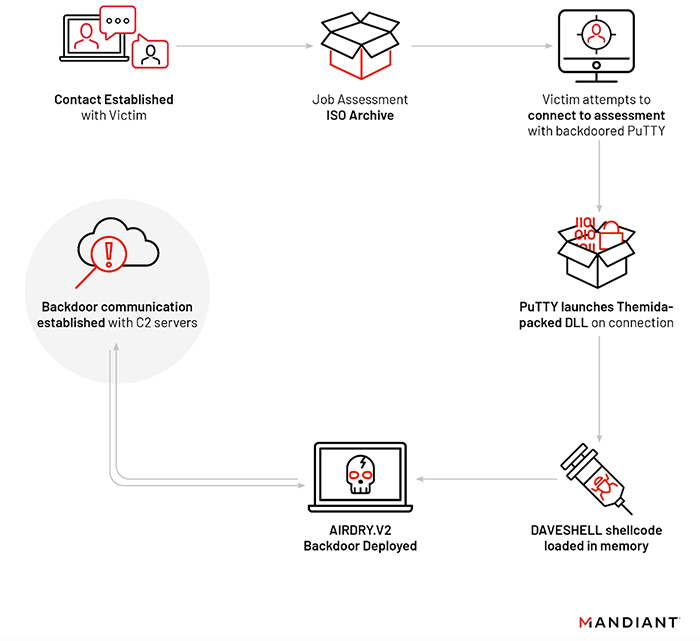
The alleged threat actor sent the target a message through WhatsApp messaging app, and sent over a file named amazon_assessment.iso.
This kind of file has become a common way for hackers to infect targets, simply because double-clicking it can usually make Windows machines to mount the file.
In this case, the ISO file has the fake PuTTY software, which is infected with AIRDRY.V2.
The executable file installed the latest version of AIRDRY is known as backdoor the U.S. government has attributed to the North Korean government.
Similarly, Japan's community emergency response team has this description of the backdoor, which is also tracked as the BLINDINGCAN.
The backdoor has been thoroughly documented in reports published by CISA and JPCERT.
Earlier versions of AIRDRY supported numerous backdoor commands, including file transfer, file management, and command execution. But in its more recent versions, the traditional backdoor commands have been removed in favor of a plugin-based approach that supports multiple communication modes.
Many of the improvements are included in AIRDRY.V2.
The researchers at Mandiant track the file as UNC4034.
"Mandiant identified several overlaps between UNC4034 and threat clusters we suspect have a North Korean nexus," company researchers wrote. "The AIRDRY.V2 C2 URLs belong to compromised website infrastructure previously leveraged by these groups and reported in several OSINT sources."
