 A group of computer scientists have discovered a dangerous security flaw that could make many mobile devices and other internet connected machines in risk of attack.
A group of computer scientists have discovered a dangerous security flaw that could make many mobile devices and other internet connected machines in risk of attack.
The security flaw, dubbed as the "FREAK attack', is reported to be rooted from the U.S. government effort in preventing consumers from having access to powerful encryption methods.
The flaw that was discovered on March 3rd, 2015, by Karthikeyan Bhargavan of INRIA, a French science and technology research institute, and by Microsoft Research, is revealed from poor implementation of encrypted links that are generated between browsers and websites user visits.
The researchers involved in the finding, discovered that they could launch an attack to secure websites (including government websites and banks), and force their browsers to use a weaker type of encryption that can be cracked in a matter of hours.
Researchers are blaming the problem on an abandoned government's policy which required U.S. software vendors to use weaker security encryption when they sell their products outside the country. The weakened encryption code is meant to help the government in fighting crime and threats to national security.
They have, however, warned that those policies could inadvertently provide access to hackers.
"This was a policy decision made 20 years ago and it's now coming back to bite us," said Edward Felten, Professor of Computer Science and Public Affairs at Princeton.
Many popular browsers from both desktop and mobile, continued to accept this policy, despite knowing it or not. As of the day of its discovery, the flaw has made a third of all encrypted websites vulnerable to hackers eavesdropping visitors when they type sensitive information on the site.
"The export mode feature was not removed from the protocol because some software still depended on it," wrote Felten.
Opening Attack Possibility in the Middle
FREAK, which stands for "Factoring RSA Export Keys", have left millions of people vulnerable to hacker attacks while surfing the internet. The flaw that has been around undetected for decades can weaken the encryption connection between computers and websites.
The flaw allows attackers to downgrade the security of connections from the default strong encryption to the weaker one, also called export-grade encryption. The keys can be downgraded by performing the man-in-the-middle attack that eavesdrop the process of encryption.
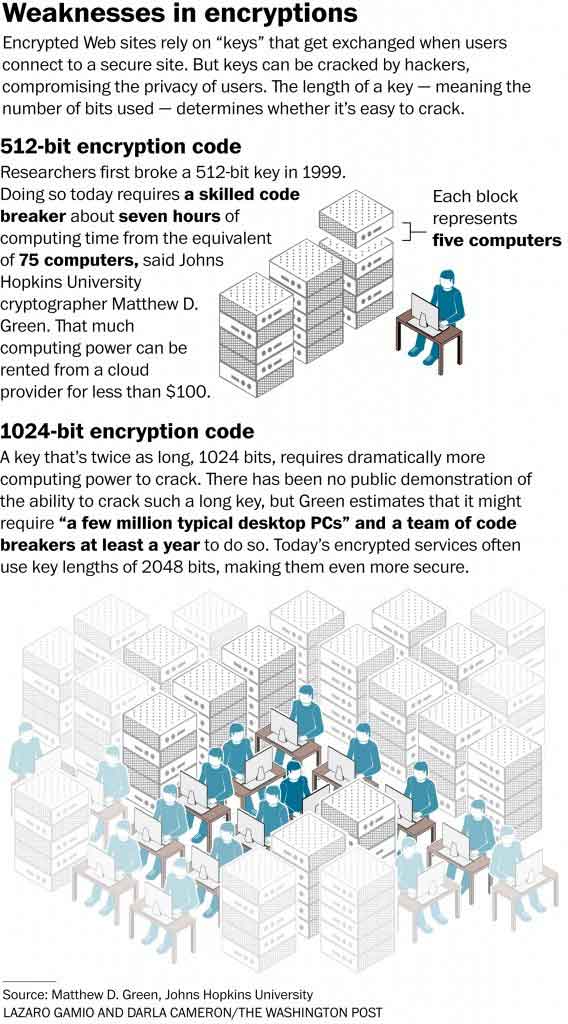
Although encryption protocols can actually prevent such tampering, hackers can still change the encryption to the 512-bit key which can be revealed using today's powerful computers. With the data traffic intercepted and decrypted, the supposedly secure data can then be readable.
Once the encrypted data is cracked, hackers could easily steal passwords and other personal information, and potentially launch a larger attack on the websites themselves by taking over elements on a page, or do damage elsewhere on the internet.
Today's encryption protocols use longer keys, and the standard is 2,048-bit RSA. The 512-bit keys were considered secure two decades ago, but not at all today.
"Back in the '90s, that would have required a heavy-duty computation, but today it takes about seven hours on Amazon EC2 and costs about $100," continued Felten.
It affects Secure Sockets Layer protocol (SSL) and Transport Layer Security (TLS). Detailed in report, including many Google and Apple devices, embedded systems and other products, and servers or clients that accept the RSA_EXPORT cipher suites, are all at risk.
Google and Apple
As both are two of the most popular mobile operating system makers, the flaw affects many of their mobile users.
University of Michigan computer scientist Zakir Durumeric said the vulnerability affects Apple's iOS web browsers and the Google's Android web browsers. The research concluded that the flaw is not affecting Google's Chrome browser or other browsers from Microsoft and Mozilla.
After one flaw to another. the U.S. government is still engaging in policies that will result in similar security flaws tomorrow. When the NSA asks companies to build backdoors into their software for the government, it will inevitably create a similar problem in the future.
The backdoors are meant for the authorities. But unfortunately, they can be exploited by anyone with skill and experience.
