
Tech companies are in constant battle with malicious actors. And this time, Microsoft as one of the players, is playing its card.
The company introduces what it calls the 'Kernel Data Protection technology', or KDP, which aims to make it even more difficult for hackers to use data corruption techniques to bypass its Windows 10 security and escalate privileges.
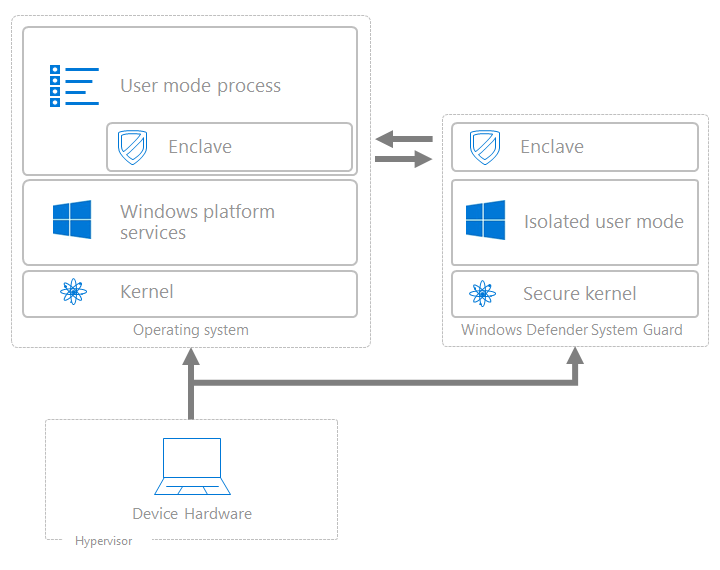
KDP does this by protecting parts of the Windows kernel and drivers through virtualization-based security (VBS).
This is done with Windows 10 in using the computer's underlying hardware to isolate a secure region of memory from the normal operating system inside a "virtual secure mode," in order to make the sections of the kernel memory read-only.
Because the data within can only be accessed but not modified, there is no way for anyone to tamper it with.
In turn, this should help block attackers and malicious software from gaining access to, and corrupting, data inside the operating system's memory.
This kind of approach should be able to mitigate emerging trend of attack, where hackers exploit signed but vulnerable drivers to install malicious and unsigned drivers which then can tamper with memory.
With read-only protection, even signed drivers would not be able to change important memory structures and settings.
In a blog post, Microsoft said that:
"KDP mitigates such attacks by ensuring that policy data structures cannot be tampered with."
KDP works by offering extra security, by granting developers access to programmatic APIs.
Microsoft also said that KDP can also improve Windows 10 performance, free up unnecessary components from constantly checking and verifying write-protected data variables, as well as boosting the operating system's reliability, as the service makes it easier to diagnose memory corruption bugs that don’t necessarily represent security vulnerabilities.
Such technology should also incentivize driver developers and vendors to improve compatibility with virtualization-based security, improving adoption of these technologies and hopefully leading to security boosts across the industry ecosystem as a whole.
The launch of KDP was motivated by a shift away from memory corruption attacks towards those targeting data corruption.
With data corruption attacks, hackers can target system security policy, allow escalated privileges, to then tamper with security detection levels. If succeeded, hackers can plant malware and other forms of malicious software, and put millions if not billions of devices at risk.
With hackers are increasingly frustrated by Code Integrity (CI) and Control Flow Guard (CFG) security technologies and look for other exploit routes, hackers in trying data corruption attack vectors is considered a logical sidestep.
And this is where KDP steps in.
The approach can be considered a significant step forward in helping secure both past future builds of its Windows 10 software.
Microsoft hopes that the new service can lessen the attack vectors within Windows 10, which has often proved a popular target for hackers and cybercriminals.
Initially, KDP is introduced on Windows 10 Insider Build only. Any computer that supports VBS can support KDP inherently.
In the meantime, VBS is supported on any computer that supports:
- Intel, AMD or ARM virtualization extensions.
- Second-level address translation: NPT for AMD, EPT for Intel, Stage 2 address translation for ARM.
- Optionally, hardware MBEC, which reduces the performance cost associated with HVCI.
- Microsoft's line of Secured-core PCs can also support VBS.