
Malware is short for "malicious software." This software can come in many forms. While their purpose can differ, they all can cause damage, and can be a pain to deal with.
And this time, researchers from Sophos discovered the emerging threat, which exploits the ProxyShell vulnerabilities in Microsoft Exchange servers. Dubbed the 'LockFile', it uses a unique and never-before-seen “intermittent encryption” method as a way to evade detection as well as adopting tactics from previous ransomware gangs.
What LockFile does, is encrypting every 16 bytes of a file, which means that some ransomware protection solutions won't be able to notice its presence.
This is because the altered size is so small, that “an encrypted document looks statistically very similar to the unencrypted original,” said Mark Loman, the Director of Engineering at Sophos.
“We haven’t seen intermittent encryption used before in ransomware attacks,” he wrote in a post.
In detail, the ransomware first exploits unpatched ProxyShell flaws, and then uses what’s called a PetitPotam NTLM relay attack to gain control of its victims' systems.
To do this, the malware uses Microsoft’s Encrypting File System Remote Protocol (MS-EFSRPC) to connect to a server, hijack the authentication session, and manipulate the results such that the server then believes the attacker has a legitimate right to access it.
“Like WastedLocker and Maze ransomware, LockFile ransomware uses memory mapped input/output (I/O) to encrypt a file,” Loman wrote in the report.
“This technique allows the ransomware to transparently encrypt cached documents in memory and causes the operating system to write the encrypted documents, with minimal disk I/O that detection technologies would spot.”
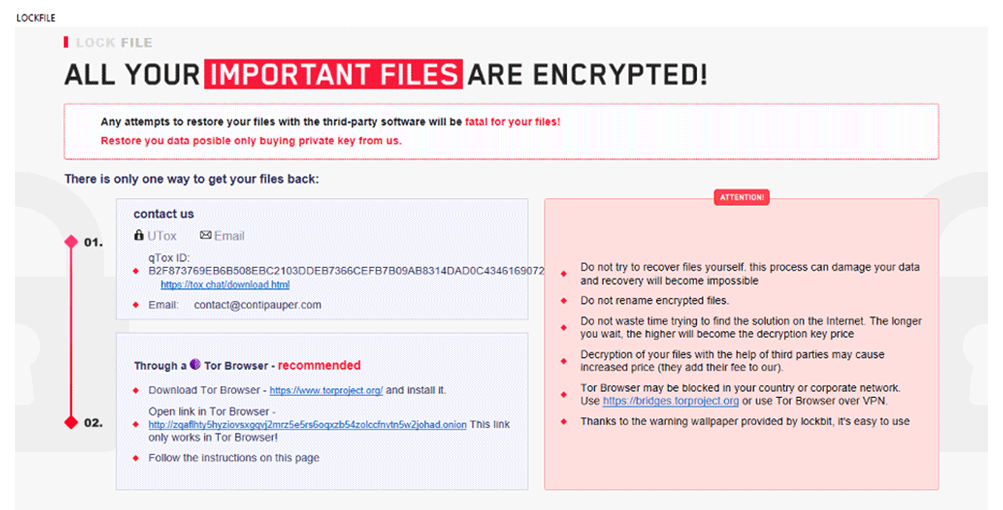
“What sets LockFile apart is that it doesn’t encrypt the first few blocks,” he wrote. “Instead, LockFile encrypts every other 16 bytes of a document. This means that a text document, for instance, remains partially readable.”
After encrypting a file, LockFile will rename the encrypted file to lower case and adds a .lockfile file extension.
Then LockFile disappears without a trace, deleting itself with a PING command, researchers said.
“This means that after the ransomware attack, there is no ransomware binary for incident responders or antivirus software to find or clean up.”
It then adds an HTML Application (HTA) ransom note looks very similar to that of LockBit 2.0, researchers said.
What makes it even scarier, LockFile ransomware doesn’t need to contact a command-and-control (C2) server on the internet to operate.
What this means, LockFile can infect and encrypt machines that do not have internet access.
