When it comes to security, biometric is considered one of the most secured as it uses certain traits that are unique from one person to another.
Fingerprints for example, they are those faint lines on our fingers. They were completely formed by the time we were 6 months old.
How our fingerprint pattern look, depends on two components: developmental and genetic. The ridge pattern development not only depends on genetic factors but also on unique physical conditions.
Factors that are thought to influence the formation of fingerprint patterns include, and not limited to: blood pressure, oxygen levels in the blood, nutrition of the mother, hormone levels, the exact position of the fetus in the womb at particular times, the exact composition and density of the amniotic fluid.
What this means, even if identical twins are genetically similar, the pressure faced by the fetus in the womb can affect their fingerprints. Even the differences in the length of umbilical cord can make changes to the fingerprints.
So here, there are myriad of variables that decide how each individual ridge is formed, which should prevent fingerprints from developing exactly the same way in any two people over the entire course of human history.
This again, should make fingerprints in humans unique.
This is why it has been used to identify people, and has also become a way to secure things.
However, things are changing a bit, since researchers from New York University have created a set of master fingerprint keys that can be used to spoof biometric identification systems.
While fingerprint scanners have the chance to falsely matching fingerprints, and so does the database of fingerprints used by the researchers, the master fingerprints they generated had the power to falsely match one out of five times.
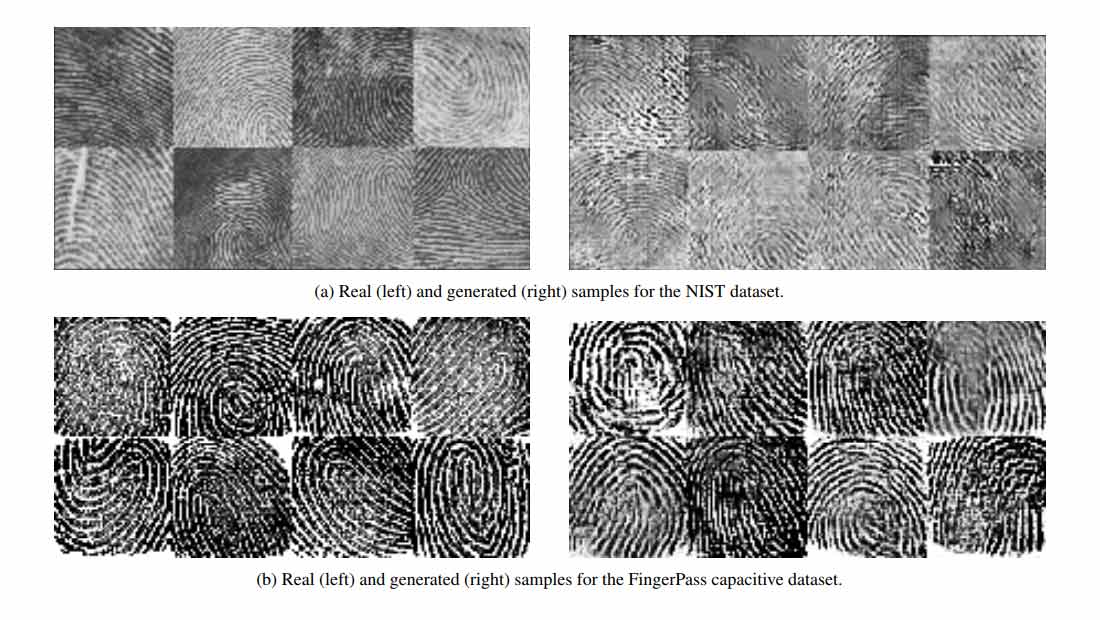
In a a paper called 'DeepMasterPrints: Generating MasterPrints for Dictionary Attacks via Latent Variable Evolution' (https://arxiv.org/pdf/1705.07386.pdf), the researchers prove that fingerprints can be artificially generated using machine learning, and be used to trick databases secured by fingerprint authentication.
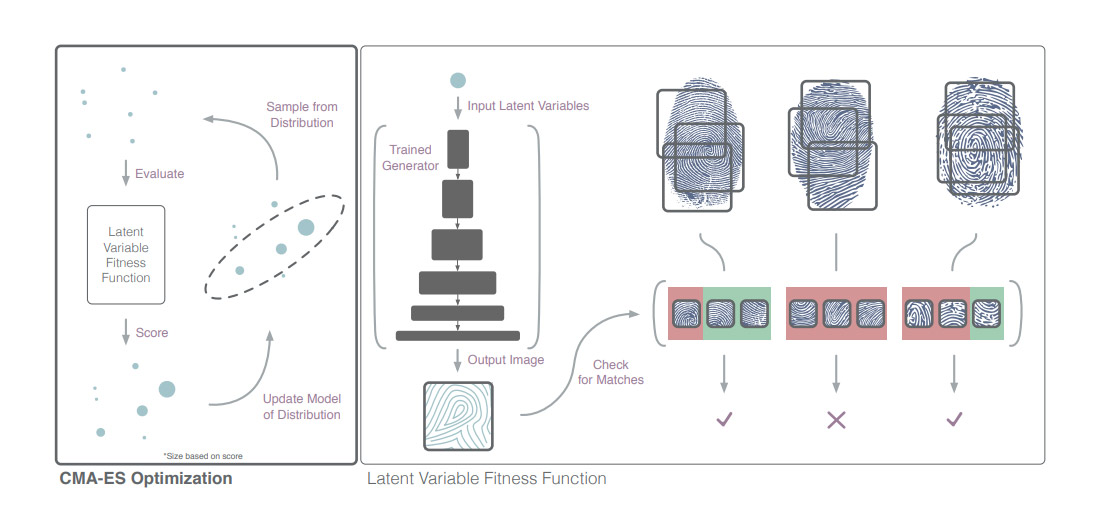
What make things worse is that most fingerprint scanners, most notably those that are found on smartphone devices, only scan for partial images of users' fingerprints. This is done by design, as people demand fast and responsive smartphones, and are not likely to appeal on devices that are slow.
The paper by the researchers noted that since partial prints are not as distinctive as complete prints, the chances of one partial print getting matched with another is high.
The artificially generated prints, called 'DeepMasterPrints; by the researchers, are making use of this vulnerability to accurately imitate one in five fingerprints in a database. The database was originally supposed to have only one error rate out of one thousand.
The DeepMasterPrints here can be used to spoof a system requiring fingerprint authentication without actually requiring any information about the user’s fingerprints. Therefore, they can be used to launch a dictionary attack against a specific subject that would then compromise the security of a fingerprint-based recognition system.
This research is alarming because there are a growing number of devices that rely on digital fingerprinting to uniquely identify users.
If hackers could get their hands on such technology, the result would be devastating.
