
Extensions on web browsers extend what browsers can do. Since developers can create whatever extensions they see fit for users, there can be some drawbacks.
One of which, is in the security side. To make sure that developers aren't violating users' rights, Google has made several announcements for its Chrome Web Store that aims at making Chrome extensions more secure and transparent.
Over the years, Chrome has become one of the most popular web browser with the most market share. But that also gave a rise in malicious extensions that appear to be useful, but apparently also run some hidden malicious scripts without users' knowledge.
Google that is aware of the issue, has been proactively working to change the way its Chrome web browser handles extensions. For example, the company has banned extensions using cryptocurrency mining scripts, and also disabled inline installation of Chrome extensions completely. Google has also been using machine learning technology to detect and block malicious extensions.
This time, Google went further, announcing five major changes that should give users more control over certain permissions, enforces security measures, as well as makes the ecosystem more transparent.
1. Host Permission For Chrome Extensions
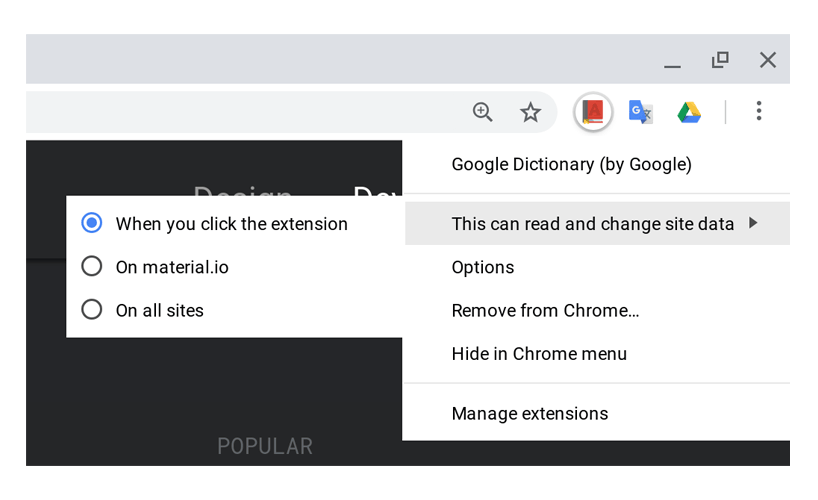
Chrome extensions have to ask permission from users before they can read, write or change data on all websites. However, there is no option for users to explicitly blacklist or whitelist specific set of websites.
"While host permissions have enabled thousands of powerful and creative extension use cases, they have also led to a broad range of misuse—both malicious and unintentional—because they allow extensions to automatically read and change data on websites," explained Chrome extensions product manager James Wagner.
Starting Chrome 70, Google is giving users the ability to control how Chrome extensions can access site data. This would allow them to restrict access for all websites, or grant temporary access to specific websites, only when required.
Users can also enable permissions for a specific set of websites or all sites.
2. Google Bans Code Obfuscation For Chrome Extensions
Google has several security measures, but still bad authors can create malicious extensions and make them appear on Google Chrome Web Store.
Those developers managed to make that happen by using obfuscation, which is a technique that aims to protect their intellectual property by making programs harder to understand, detect or analyze. Malware authors for example, can pack their extension using obfuscation techniques to make it difficult for Google's automated scanners to review extension and detect or analyze the malicious code.
According to Google, more than 70 percent of "malicious and policy violating extensions" that it blocks contain obfuscated code.
With Chrome 70, the Chrome Web Store is no longer allowing extensions with obfuscated code.
3. A Mandatory 2-Step Verification Process For Developers
Google plans to make two-step verification a mandatory for all developers.
"If your extension becomes popular, it can attract attackers who want to steal it by hijacking your account, and 2-Step Verification adds an extra layer of security by requiring a second authentication step from your phone or a physical security key. We strongly recommend that you enroll as soon as possible," said Google.
For even stronger account security, Google considers developers to use its Advanced Protection Program that offers the same level of security that Google relies for its own employees. The Advanced Protection Program requires developers to use a physical security key to provide the strongest defense against phishing attacks.
4. A Strict Chrome Extension Review Process
"Going forward, extensions that request powerful permissions will be subject to additional compliance review," said Google.
The company is also looking closely at extensions that use remote hosted codes, with ongoing monitoring.
With Chrome 70, "Your extension’s permissions should be as narrowly-scoped as possible, and all your code should be included directly in the extension package, to minimize review time," continued Google.
5. Manifest Version 3 For Chrome Extensions
Google also plans to introduce Manifest version 3, which entails additional platform changes that aim to create stronger security, privacy, and performance guarantees. "We want to help all developers fall into the pit of success; writing a secure and performant extension in Manifest v3 should be easy, while writing an insecure or non-performant extension should be difficult," said Google.
Manifest version 3 include:
- More narrowly-scoped and declarative APIs to decrease the need for overly-broad access and enable more performant implementation by the browser, while preserving important functionality.
- Additional, easier mechanisms for users to control permissions granted to extensions.
- Modernizing to align with emerging web capabilities, such as supporting Service Workers as a type of background process.
"We intend to make the transition to manifest v3 as smooth as possible and we’re thinking carefully about the rollout plan."
With Google having more than 180,000 extensions in the Chrome Web Store, the company believes that the above changes are necessary. The measures should make the web more secure for its billions of Chrome users.