
PHP may be considered outdated in terms of methodology as it's complex as it can be. But still, it is one of the most popular languages for the web and it's in very high demand.
While many are using it, it doesn't mean that flaws are patched quickly as they are found. According to a team of South Korean academics, there are 30 vulnerabilities in the file upload mechanisms used by 23 open-source web applications, forums, store builders, and content management systems (CMSs).
The academics found the flaws using their own testing tools, which include 'FUSE', or an automated penetration testing tool created to discover UFU (unrestricted file upload) and 'UEFU' (unrestricted executable file upload).
And here, they found that there are many file-uploading vulnerabilities in PHP-powered applications
When these flaws present in live web apps, hackers can exploit the file upload forms and plant malicious files on the victims' servers.
In turn, this could translate to catastrophe.
Hackers can literally do anything with the website, including weakening the security systems, installing more malware, create backdoors and ultimately obtain full control of the website and its servers.
After they built team built the tools, they selected 33 of the most popular web apps, including CMSs, online forums, enterprise products, and e-commerce builders.
The research team, which consisted of academics from the Korea Advanced Institute of Science and Technology Constitution (KAIST) and the Electronics and Telecommunications Research Institute (ETRI), individually tested FUSE against their tools on those apps.
Using the tools' automated requests, the researchers exploited file upload mechanisms in the 33 web apps in an attempt to plant various types of malicious files (PHP, JS, HTML, XHTML, .htaccess). And here, the team discovered that the tests found 30 file upload bugs impacting 23 of the 33 applications they tested.
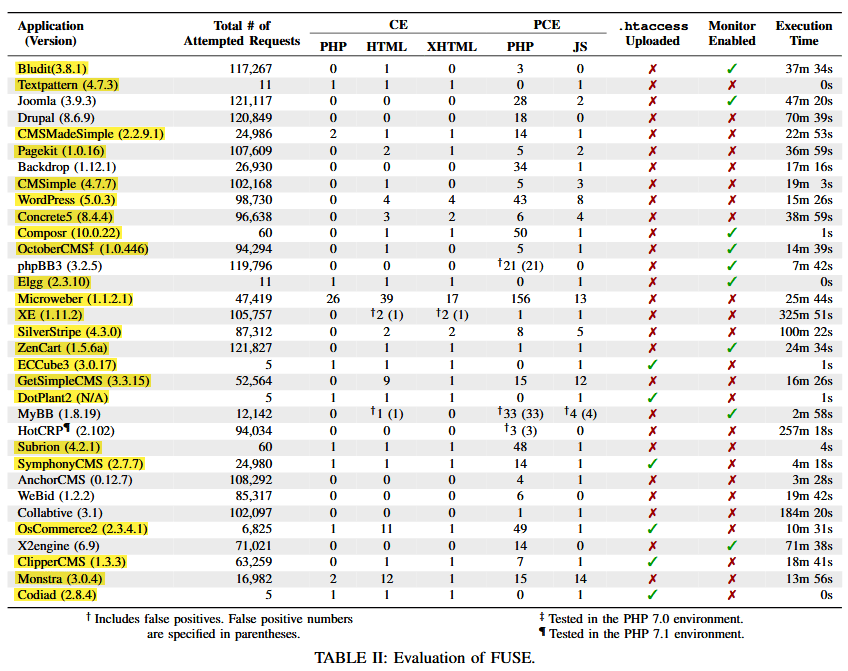
On the research team's white paper:
"Eight vulnerabilities from five vendors have been patched. Five vulnerabilities from four vendors, including WordPress, confirmed that they would address the reported vulnerabilities."
"15 bugs are awaiting confirmation from the corresponding vendors. Two vendors declined to patch the reported bugs."
The results shown above, was compiled on February 2019.
Since then, the web apps have have received updates. However, KAIST and ETRI researchers said that not all projects have patched the bugs they found, and some of the projects highlighted in yellow may still contain one or more file upload bugs.
Many errors have not yet been fixed and are not in the priority for the vendors for the simple reason that 14 out of 30 vulnerabilities require administrative access for exploitation.
The vendors don't see this as a risk because a hacker with administrator rights can in any case establish full control over a vulnerable server.