Previously, software products have to be installed through a storage medium. Later, with the internet, people could start downloading software from various sources.
During this time, malicious actors try to infect victims by distributing their software in as many places as possible. The more places they can place their malware, the higher the chance they can infect more people. But since more and more people started to realize that the safest place to download apps is from trusted and official sources, hackers needed a revised plan.
This is why more and more malicious actors are distributing the malware-laced software on official app stores, like through Google Play Store, for example.
And not just that, as Microsoft Store is also experiencing the same issue.
A researche from Check Point Research has found a strain of malware called the 'Electron Bot' spreading on the official store, posing as a trojanized gaming apps.
According to the report, the malware has infected at least 5,000 Windows machines, mostly in Sweden, Bulgaria, Russia, Bermuda, and Spain.
When Windows users download the infected apps and install them on their machines, the malware within will open a hidden browser window to carry out SEO poisoning, generate clicks for ads, direct traffic to contents on YouTube and Soundcloud, and promote a number of products to generate profits through ad clicks and increasing store ratings.
The malware can do this by first dropping and installing its next stage dropper via JavaScript.
But what it does worse, is its ability to control victims' social media accounts.
According to the researchers, the malware can hijack victims' Facebook, Google, and SoundCloud accounts, and is also capable of registering new accounts, signing in, and even commenting or Liking others' posts.
"As the bot's payload is loaded dynamically at every run time, the attackers can modify the code and change the bot's behavior to high risk," Marelus noted. "For example, they can initialize another second stage and drop a new malware such as ransomware or a RAT. All of this can happen without the victim's knowledge."
"This enables the attackers to modify the malware's payload and change the bots' behavior at any given time," Marelus explained.
The malware in question is being distributed via the Microsoft Store platform, hiding in dozens of infected apps – mostly games – that the attackers are “constantly” uploading, the report said.
The strain for the Electron Bot as an ad clicker was first spotted back in October 2018, with the malware hiding in plain sight in the form of a Google Photos app, as disclosed by Bleeping Computer.
Since the, the malware has undergone numerous iterations and tweaks, where the authors behind have added more features and more powerful evasive capabilities.
And as years past, the malware has gotten bigger and more capable.
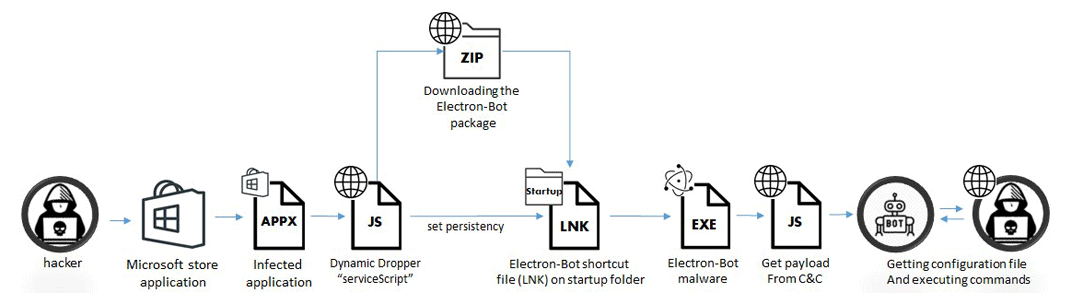
The malware gets its name from Electron, an open-source framework for building cross-platform, native desktop applications using web technologies such as JavaScript.
It's worth noting that the malware's activities when infecting machines aren't terribly high-risk, researchers noted.
However, as previously mentioned, the authors could modify its codes at any time. And given that the Electron framework’s granting of access to all computer resources, including GPU computing, there are chances that the malware could deplete its victims' resources.
At this time, the malware has been distributed through games like Temple Endless Runner 2, a clone of Temple Run 2, the popular “infinite” runner game.
"Given most people think that you can trust application store reviews, they do not hesitate to download an application from there."
To prevent downloading malicious apps, Check Point Research suggests users to avoid downloading apps with small number of reviews, always look for apps with good and consistent, reliable reviews, and pay attention to suspicious app naming that’s not identical to the original name.