
People store almost anything on their mobile devices, and that anything can be some sensitive data, or even private information.
With this already a fact, malicious actors are already targeting mobile devices in order to extract those data. And it's through infecting victims with malware that hackers can make target devices to leak data, allowing sensitive information open for them for the taking.
This time, security researchers have discovered a novel malware strain with spying and surveillance capabilities.
The spyware in question, targets people on both Android and iOS.
Named the 'Goontact', this malware has the ability to collect contacts from infected victims' devices, as well as phone identifiers, SMS messages, photos, and also location information.
Goontact was discovered by mobile security firm Lookout, saying in a blog post that the threat targets users in Chinese speaking countries, including Korea and Japan, with evidence on distribution sites spanning to also include Thailand and Vietnam.
After these malware-infected apps collect user data, they will send them to the servers operated by the hackers.
Researchers at Lookout believe that Goontact's operation is very similar to sextortion campaign detailed by Trend Micro in 2015. The researchers believe that the data collected through these apps could later be used to extort victims into paying ransoms or to attempt sexual encounters to have them exposed to friends and contacts.
"Tablets and smartphones are a treasure trove of personal data. These devices store private data, such as contacts, photos, messages and location. Access to all of this data enables cybercriminals like the operators of Goontact to run a successful extortion campaign," the researchers said.
Based on the language used in the admin panels of the servers, the researchers at Lookout believe that the operators are most-likely Chinese-speaking hackers.
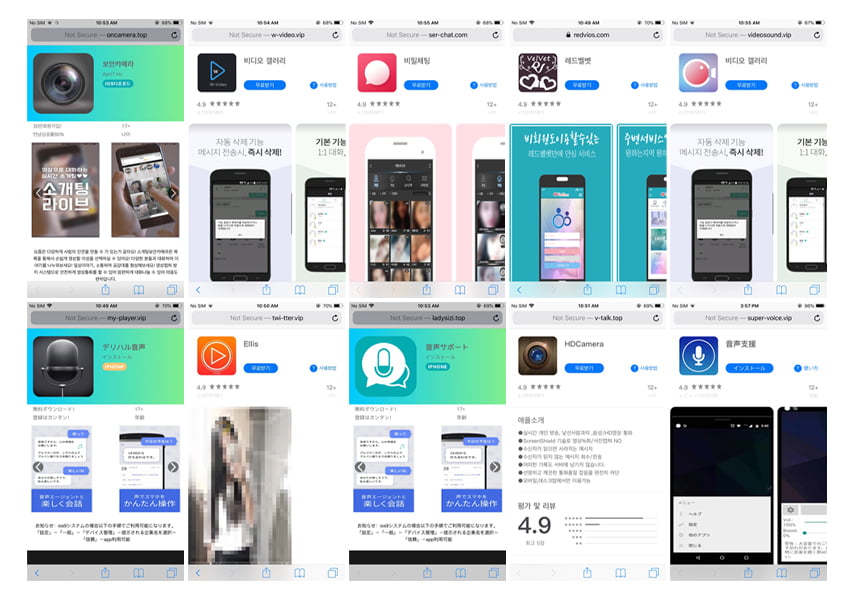

At the moment of finding, the malware has yet to enter Apple App Store and Google Play Store, but there are signs that people are downloading and side-loading Goontact-infected applications.
The researchers have notified both Google and Apple about this threat.
In response, Apple is said to have revoked enterprise certificates used to sign the malicious apps and, as a result, the apps in question should stop working on devices.
And as for Google, a Lookout engineer added that Play Protect will notify users if any Goontact-infected Android apps are installed on their device.