
Android is the operating system from Google, which powers a lot of smartphones and smart devices.
While it's a formidable, powerful and a very capable operating system, it's far from perfect. It's also prone to various security bugs and other weaknesses.
And this time, Netlab, the networking security division of Chinese security firm Qihoo 360, has discovered a malware operation utilizing DDoS botnet.
Calling it the 'Matryosh', the botnet targets Android devices where vendors have left a diagnostics and debugging interface known as Android Debug Bridge (ADB) enabled and exposed on the internet.
ADB which uses port 5555, has been riddles with various problems on Android for years. And this Matryosh malware is one among others that target Android devices where the ADB interface has been left active.
Others include, and not limited to other malware families like ADB.Miner, Ares, IPStorm, Fbot, and Trinity.
These malware are known to exploit weaknesses in ADB to install malicious payloads.
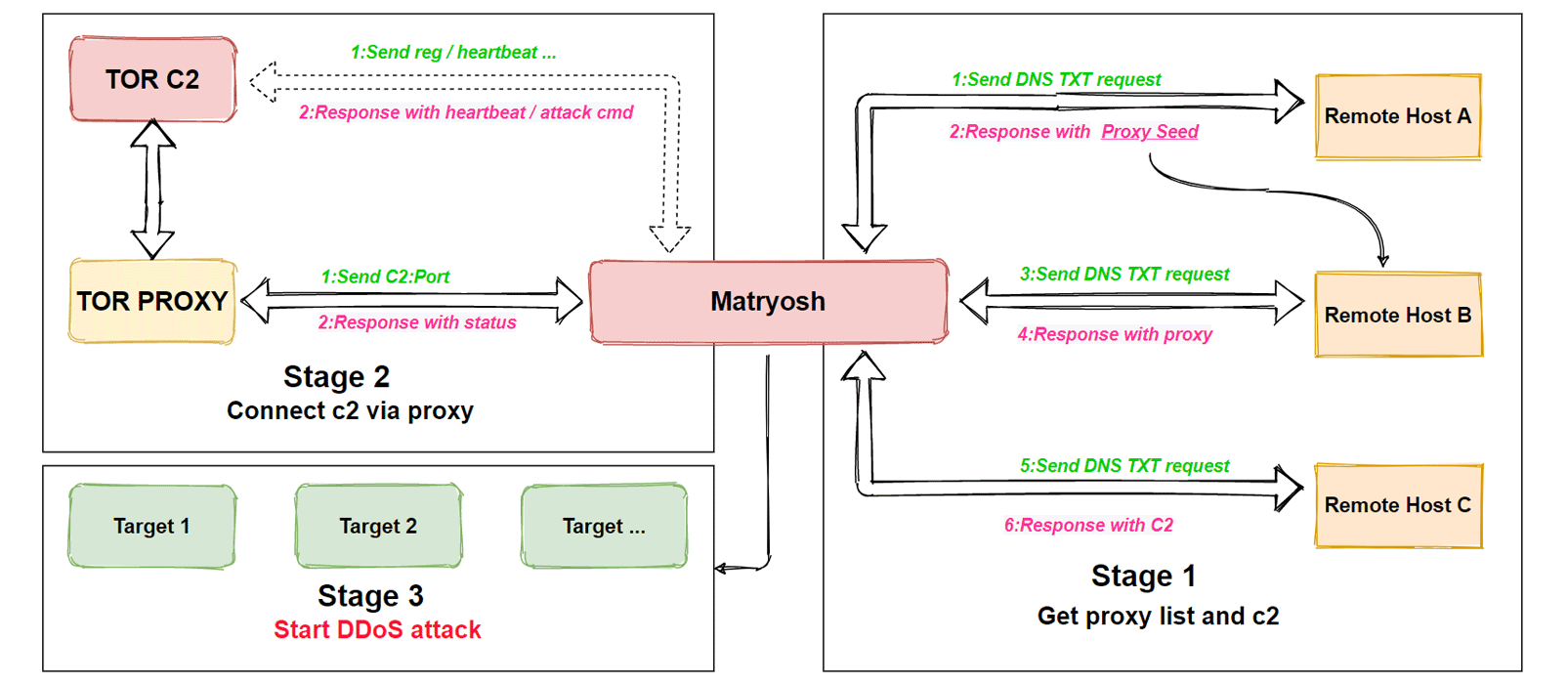
According to Netlab's blog post, its system first found and labeled a suspicious ELF file as Mirai. But when the team looked at it, the network didn't have the Mirai characteristics.
"It redesigns the encryption algorithm and obtains TOR C2 and the TOR proxys from remote hosts via DNS TXT."
Upon closer inspection, the team saw that the file uses encryption algorithm that is nested in layers.
This is why the team named it the 'Matryosh', taking its name from the Matryoshka doll, which is a Russian tea dolls that are basically a set of dolls of decreasing sizes placed one inside another.
As the team dug further, they finally found the malware and its command and control instructions.
The Netlab team also said that they found functions in the code specific to features that will use infected devices to launch DDoS attacks via protocols like TCP (tcpraw), UDP (udpplain ), and ICMP (icmpecho).
"We speculate that it is another attempt by the Moobot group, which is very active at the moment," the team said.
"Matryosh's cryptographic design has some novelty, but still falls into the Mirai single-byte XOR pattern, which is why it is easily flagged by antivirus software as Mirai."
While the malware botnet has been found, there is little that users can do to stop incoming attacks.
This happened not because of the nature of the malware, but because of the ADB issue that started all this.
ADB is a versatile command-line tool on Android, allowing users and developers to communicate deeper into a device, in a way that a normal user-interface can never provide. The function facilitates a variety of device actions, such as installing and debugging apps, as well as providing access to a Unix shell that developers can use to run a variety of commands on a device.
ADB is a essentially a client-server program that allows developers to "connect your development workstation directly to your Android device."
While smartphone owners can easily turn off their ADB feature through their phone's settings, for other types of Android-based devices, the option to do that isn't available.
Knowing that Android also powers watches, smart TVs, set-top boxes, home appliances and home automation systems, cameras, in-car infotainment system, and other smart devices, the attack will remain.
As these devices (to some degree) don't allow thorough customizations and tweaks, they will remain vulnerable and exposed to abuse to this botnet malware campaign.
Besides DDoS attacks, Matryosh and other botnets can also abuse systems for cryptocurrency mining, DNS hijacking, and more.