It was in June 2015 when Google first introduced its bug bounty program for Android. At that time, the biggest reward was $38,000.
As Android grew in popularity, the reward grew over time. As a result, more researchers got on board, and more bugs were found and squashed. In November 2019, Google's Security Rewards Program bumped the top reward tremendously to $1 million.
But that amount isn't going to be paid out for just any bug found.
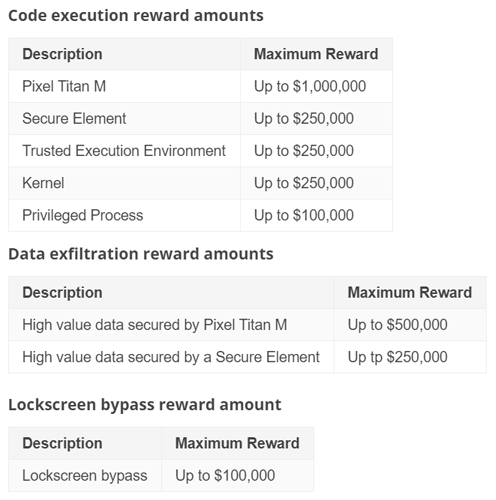
The most people can earn in this bug bounty, is if they can discover "full chain remote code execution exploit with persistence which compromises the Titan M secure element on Pixel devices”.
What this means, Google is looking for a bug that, without the attacker having physical access to the device, can execute code even after a device is reset and breaks into the dedicated security chip built into its Pixel phones.
And if they can do it on “specific developer preview versions” of Android, Google is giving a 50% bonus reward, bumping the maximum reward to $1.5 million.
Google first introduced the Titan M security chip alongside the Pixel 3.
According to Google on its October 2018 blog post, the Titan M is "an enterprise-grade security chip custom built for Pixel 3 to secure your most sensitive on-device data and operating system. With Titan M, we took the best features from the Titan chip used in Google Cloud data centers and tailored it for mobile."
The chip is meant to supervise and double check boot conditions, verifies firmware signatures, handles lock screen passcodes, secure transactions on third-party apps, handles on-device encryption, and tries to keep malicious apps from forcing users' device to roll back to "older, potentially vulnerable" builds of Android.
$1.5 million bounty price is a big increase, considering that the figure is roughly what Google paid out for all bug bounties in the last 12 months.
Before the announcement, the top reward in 2019 was $161,337 for a "1-click remote code execution exploit chain on the Pixel 3 device", and the average payout was about $3,800 per finding.
Since Pixel phones use "the most secure version of Android", Google is taking no chances.
Given the potential severity of hackers persistently busting through security systems inside devices, Google is willing to pay huge sum to whoever can crack its flagship's security chips.
