In what is reported as the "2020 United States federal government data breach," the U.S. fell government became a victim of a massive hack by a cyberattack group backed by a foreign government.
Until this date, the breach is considered one of the worst ever experienced by the U.S. government, due to the high profile of the targets and the duration for which the attacker had access. the data breach was said to have been initiated by the Cozy Bear hacking group, backed by the Russian state agency SVR.
The hack was first spotted on December 13, attacking the U.S. Treasury Department and the National Telecommunications and Information Administration (NTIA). The next day, more departments reported breaches, suggesting that the hack campaign expanded.
Investigators said that multiple attack vectors were used in this supply-chain attack.
The attacker was said to have exploited software from at least three U.S. firms: Microsoft, SolarWinds, and VMware, all of which are widely used in government and the industry.
Exploiting them, hackers managed to steal data, get access to emails and other documents, allowing them to perform federated authentication across victim resources.

The data breach was a result of at least 8 or 9 months of occurrences that happened during the final year of Donald Trump's presidency.
Throughout this time, many parts of the government were left without cybersecurity coordinators and officials. Also at that time, the DHS, which manages CISA, lacked a Senate-confirmed Secretary, Deputy Secretary, General Counsel, Undersecretary for Intelligence and Analysis, Undersecretary for Management, and Deputy Director of CISA.
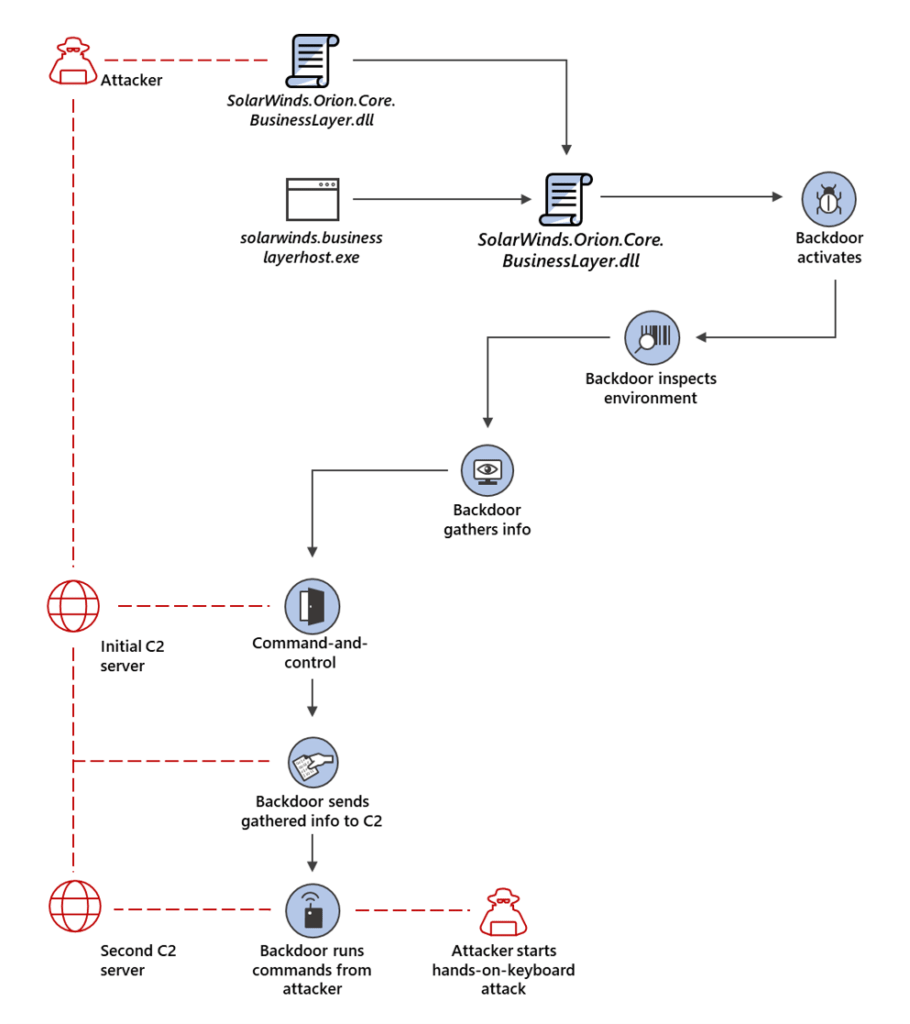
The first path towards the hack, was through SolarWinds, the provider of network monitoring software used by the U.S. federal government.
The company was already suffering from numerous shortcomings, due to the fact that hackers have been selling access to its infrastructure since at least 2017. And it was on December 7, that hackers breached the federal government's system through trojanized SolarWinds software.
The hackers planted the remote access tool malware into updates for Orion, a network monitoring software.
SolarWinds published a press release, saying that Orion update versions 2019.4 through 2020.2.1, released between March 2020 and June 2020, have been riddled with malware.
"We’ve been advised that the nature of this attack indicates that it may have been conducted by an outside nation state, but SolarWinds has not verified the identity of the attacker," the company said on its Security Advisory web page.
Following SolarWinds, the hackers used Microsoft as their next attack vector. It was through exploiting a vulnerability in Microsoft's authentication protocol NetLogon that the hackers gained access to credentials of Microsoft Accounts inside the Orion network they breached.
This allowed them to access additional credentials necessary to assume the privileges of any legitimate user of the network, which in turn allowed them to compromise Microsoft Office 365 email accounts.
The last, was through VMware, where the hackers exploited bugs in VMware Access and VMware Identity Manager. This allowed them to infiltrate the networks.
The months-long hacking campaign came to light only after security firm FireEye admitted that itself had been breached by a nation-state hack campaign.
It was only during the following investigations that hackers didn't only use FireEye's tools, but also by exploiting others in the supply-chain attack.
FireEye named this malware 'Sunburst', detailing it in a published a technical report, along with the countermeasures on GitHub.
Microsoft named the campaign 'Solorigate', a sophisticated attack that started from library poisoning.
In all, the hack managed to infiltrate at least 18,000 servers through SolarWinds alone.
As of Microsoft, the company has identified more than 40 of its customers around the world experienced problematic versions of a third-party IT management program, 80% of whom are in the U.S. while the rest are in seven other countries: Canada, Mexico, Belgium, Spain, the United Kingdom, Israel and the United Arab Emirates.
This massive hacking campaign is considered one of the worst espionage happening since the last decade if not of all time.
The scale of this sophisticated cyberattack is also much bigger than first anticipated.
"The victims have included government, consulting, technology, telecom and extractive entities in North America, Europe, Asia and the Middle East. We anticipate there are additional victims in other countries and verticals," FireEye said.
The Cybersecurity and Infrastructure Security Agency said in a summary, that the threat "poses a grave risk to the federal government."
It then that "state, local, tribal, and territorial governments as well as critical infrastructure entities and other private sector organizations" are also at risk.
Microsoft President Brad Smith said that "this is not espionage as usual" and "while governments have spied on each other for centuries, the recent attackers used a technique that has put at risk the technology supply chain for the broader economy."
As for U.S. President-elect Joe Biden, he pledged to make cybersecurity a key area of focus for his administration.
"A good defense isn't enough; We need to disrupt and deter our adversaries from undertaking significant cyberattacks in the first place," Biden said in a statement.
"We will do that by, among other things, imposing substantial costs on those responsible for such malicious attacks, including in coordination with our allies and partners. Our adversaries should know that, as President, I will not stand idly by in the face of cyber assaults on our nation."
President Donald Trump, remained mostly silent about the hacking.
And for its part, the Russian presidential spokesman Dmitry Peskov rejected the accusations, according to the Tass news agency.
"Even if it is true there have been some attacks over many months and the Americans managed to do nothing about them, possibly it is wrong to groundlessly blame Russians right away," the official said. "We have nothing to do with this."
Further reading: Microsoft's Exchange Server Leaked Emails Of More Than 30,000 Organizations