Common challenges of IT security, include, and not limited to: the complexity and resources, network trust and malware and user experience.
As technologies evolve, the strategies to hack and attack are also developing. And they are all trying to make advantages of those common challenges. This is why security perimeters should be continuously updated to make them more capable.
Conventional security models operate with an assumption that everything on the inside of an organization’s network can be trusted. This is because they are designed to protect the perimeter from whatever that wants to go in, but apparently, makes any threats that are already inside to be left invisible.
Once inside, attackers can do whatever they want. Most modern egregious data breaches happened because hackers, once they gained access inside corporate firewalls, were able move through internal systems without much resistance.
This can be a whole lot of trouble for the organization.
With increased attack sophistication, security measures should go a step up to prevent malicious attempts from spreading.

Platforms, applications, users, and devices are all moving outside. Companies data centers are serving a contained network of systems that typically use some applications on-premises and some in the clouds. This eliminates the what was once the trusted enterprise perimeter.
And 'Zero Trust' here is rooted in the principle of "never trust, always verify."
Zero Trust that was first introduced by analyst firm Forrester Research in 2010, is an alternative architecture for IT security. The security parameter verifies every user, validates their devices, and also limits the access and privilege to certain things, all that without impacting user experience.
It is centered on a belief that nothing should be trusted, whether they are inside or outside of its perimeters. Here it must verify anything and everything trying to connect to its systems before granting access.
This is done by leveraging micro-segmentation and granular perimeters enforcement, based on user, data and location.
Zero Trust works by:
- Ensuring all data and resources are accessed securely, based on user and location. Users must identify the traffic and data flow, and then have the visibility to the application, the user and the flows. Understanding who the users are, what applications and device they are using and the appropriate connection method is the way to determine and enforce policy that ensures secure access to data.
- Use the least-privileged access strategy to strictly enforce access control. This way, businesses can reduce entry-point for attackers and malware.
- By always verifying, businesses should always inspect and log all traffic. To do this, businesses need to identify the appropriate junctions for inspection and build in the inspection points. Security rules should be used to identify, to then allow or deny the incoming traffic and activity to move through the inspection points.
- Add more authentication methods to mitigate any credential based attacks.
- Never trust anyone, and always keep adding context and make roles up-to-date.
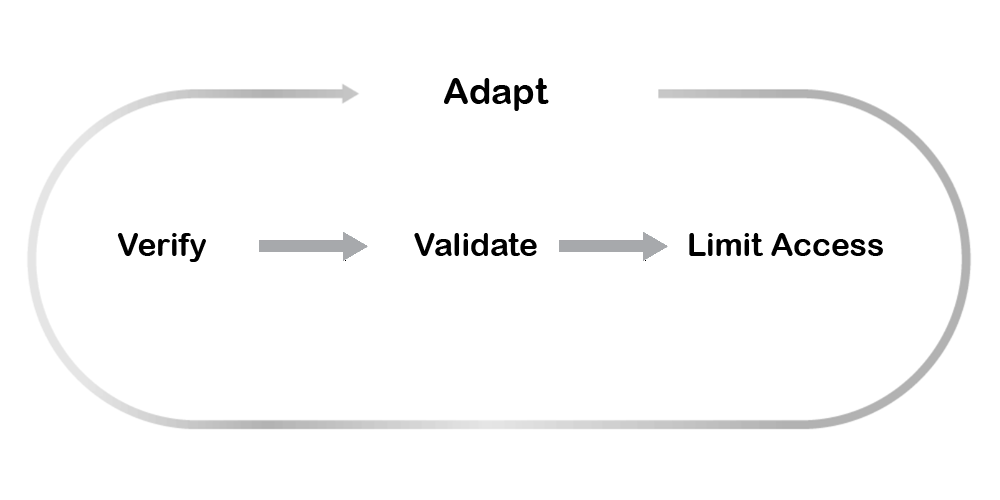
While it’s necessary to secure the external perimeter border, it’s even more crucial to gain the visibility to verify traffic as it crosses between the different functions within the network. Zero Trust can effectively get visibility and context for all traffic across user, device, location and application.
Leverage Zero Trust approach should allow businesses to see the flow, users, data, data flows, and associated risks, and set policy rules that can be updated automatically, based on the risks, with every iteration.
Bad actors and malicious threats aren’t the only thing driving this model.
In the modern IT world, it is required to improve the existing interations. In terms of security, a castle itself no longer exists in isolation as it once did.
To implement this model, businesses need to understand that Zero Trust requires ongoing effort, and may have certain pieces that create more challenges than others
