People are always urged to update their operating system as soon as a newer version comes out. But hackers here managed to get into the cracks to launch their campaigns.
One of which, is by using the 'TrickBot' malware. Better known as a cybercrime malware that uses Windows backdoor, it was thought to have compromised at least 250 million email accounts in 2019. And here, it has evolved to target and infect even more Windows users.
As security researchers from Morphisec Labs discovered, TrickBot has evolved to be able to target Windows 10 users far more deeply by bypassing User Account Control (UAC).
According to Morphisec in a blog post:
"On almost a daily basis, malicious actors reinvent Trickbot and work to find new pathways to deliver the trojan onto user machines. This is what makes Trickbot among the most advanced malware delivery vehicles; the constant evolution of methodologies used for delivery."
Windows 10 uses a security mechanism called User Account Control (UAC) that displays a prompt every time a program is run with administrative privileges.
When these prompts are shown, they will ask logged in user if they wish to allow the program to make changes, and if the program is suspicious or unrecognized, users can prevent the program from running. This safety precaution is very useful from preventing bad programs from running.
But the TrickBot malware here, has evolved to bypass this, as it can execute itself with elevated privileges, without showing any UAC prompt.
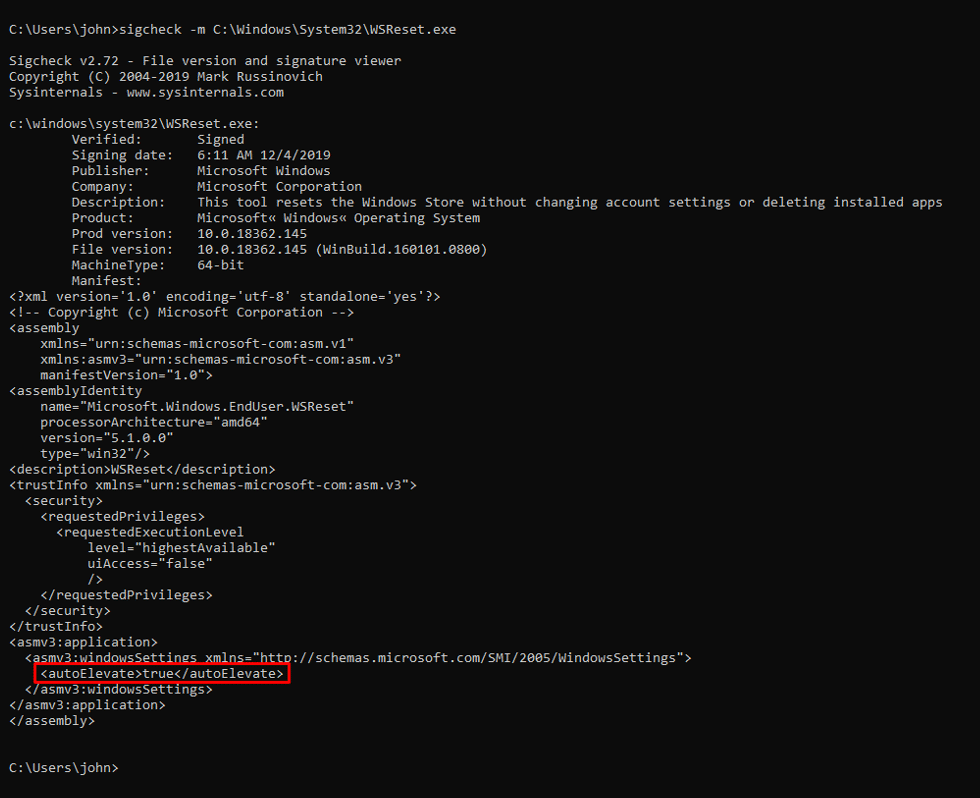
This is done with TrickBot using legitimate Microsoft executables that can bypass UAC, like the WSRESET UAC Bypass on Windows 10 machines.
And if the victim runs older version of Windows, like Windows 7 for example, the malware will utilize the CMSTPLUA UAC Bypass.
This way, the malware can run silently in the background while harvesting login credentials, SSH keys, browser history, cookies, and more.
The danger can go beyond that, as it can also sneak into the network the system is connected to, and if it gains administrator access to control the domain controller, it can also steal Active Directory database to gain further credentials on the network.
Eventually, TrickBot is known to open a reverse shell back to the Ryuk Ransomware actors so that they can encrypt the entire compromised network.
Later, the malware again evolved, with the method of attack pinpointing to Windows 10.
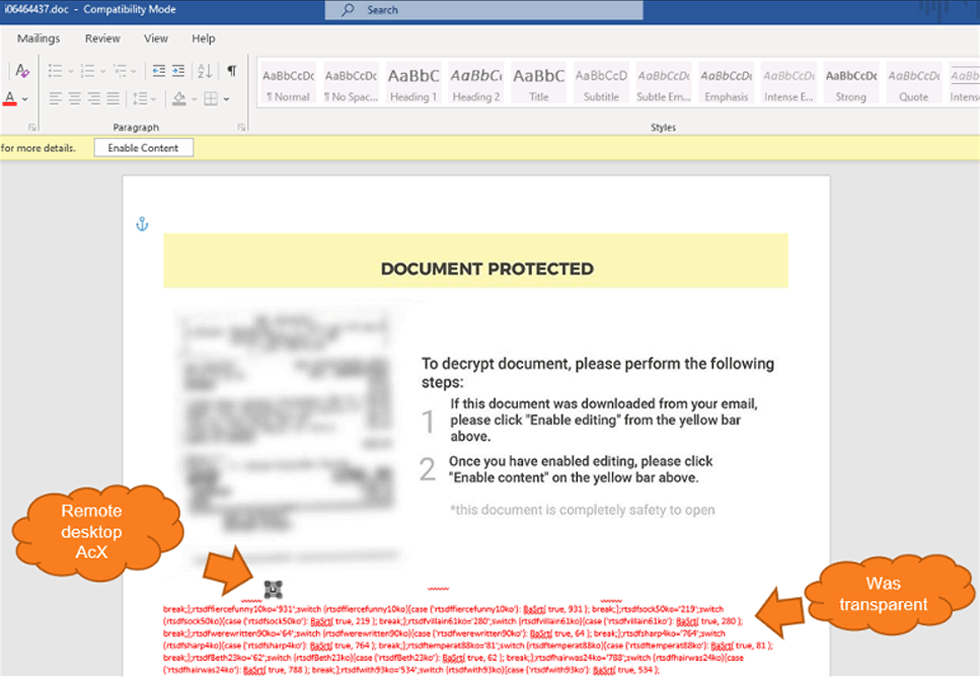
After finding a few dozen documents that execute the OSTAP javascript downloader, the researchers at Morphisec found that hackers are targeting the remote desktop ActiveX control function in Microsoft Word documents as a method to download TrickBot.
In a blog post, Morphisec said that:
As a modern operating system, Microsoft updates Windows 10 to introduce new feature and functionalities.
With the pace Microsoft is updating its popular operating system, security vendors need to keep up and update their techniques to protect the system. And here, hackers are exploiting the brief moment to exploit any vulnerable system they can find.
TrickBot is trojan-type malware designed intentionally to steal users' private data. It was first identified in 2016, targeting various financial institutions, banks, and credit card providers. Since then, the malware authors seem to continuously update the malware, making it one of the most advanced malware in the wild.
Mainly distributed via spam and phishing emails, it can also take form in fake Adobe Flash Player updates.
People are always urged to update their operating system to gain the advantages of better security. But with this kind of malware, updating to the most recent version may not always serve that purpose.
Even with an updated operating system, users need to understanding preventive measures to reduce the attack surface and harden their system.
For example, people should never open email attachments that they aren't expecting, never enable macros, content or editing in them if they do.
Google that is said to have scanned 300 billion attachments per week with its AI technologies, found that malicious documents represent 58% of all the malware that targets Gmail users.