Security is always a concern when it comes to the web. As more internet-connected devices are getting to more hands, people should know how to protect themselves from exploits.
Over the weekend, security researcher Mathy Vanhoef found a way to decrypt the WPA2 Wi-Fi security protocol. The KRACK hack, short for Key Reinstallation Attacks, were revealed.
WPA2 (Wi-Fi Protected Access) is the standard network security protocol, largely used in replacement of WEP. It was regarded as safe as it dynamically generates new keys to encrypt packets. However, WPA2 isn't as safe is it may seem.
KRACK exploits all modern Wi-Fi networks. Any device that supports Wi-Fi, are likely to be already affected.
During their research, it was found that Android, Linux, Apple, Windows, OpenBSD, MediaTek, Linksys and other devices were all susceptible to this vulnerability in some shape or form.
What makes KRACK even worse is that the attacks using it, can be manipulated for a wide range of devices. But the worst is for devices on Android 6.0 or higher, as they have a version 2.4 or higher wpa_supplicant.
In total, 41 percent of all Android devices are vulnerable to this "exceptionally devastating variant" of the attack. All Wi-Fi devices are susceptible to it, regardless of operating system.
A permanent fix has been released not long after the flaw was found, with many many other companies are working on the solution. It requires both vendors and also users to update their routers to the latest firmware.
How KRACK Attacks
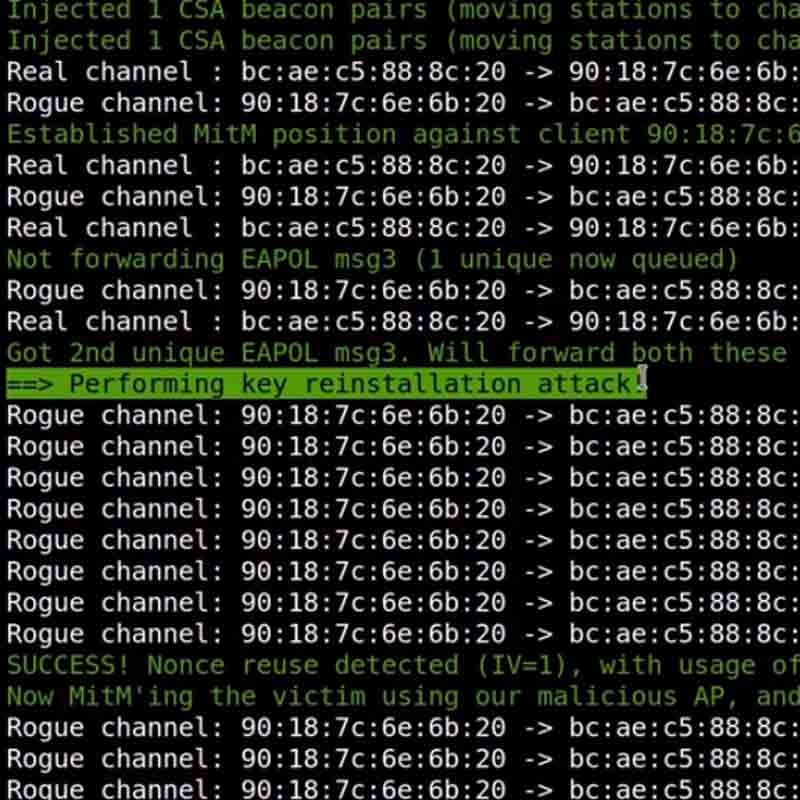
KRACK works by first creating a second Wi-Fi network by exploiting 802.11 traffic between a Wi-Fi router and a connected device, copying all attributes of the original except working on a different channel.
KRACK then attempts to contact the device it is targeting, forcing it to connect to the new network on a separate channel using what's called a CSA Beacon, or Channel Switch Announcement.
As the affected device connects to the rogue network, the network forces the device to forward internet through it to another connection. This allows the attacker to later steal the decrypted data.
Next the program sslstrip runs and manipulates all traffic that isn't on port 80 (HTTP requests), and move it to port 10000 (used by the program modifying the data). Any HTTPS requests that usually use port 443 are redirected to port 10000 when sslstrip is running. This makes secure data request stripped and then sent through as decrypted.
What this means, HTTPS link will convert to HTTP version of the website.
If the website that has the link is properly configured, the request will be denied. However, those that are Improperly configured, will allow users to access it, making them prone to hacks.
WireShark is then set up to monitor all traffic running through the network card of the computer. As data is being forwarded, any requests by the device connecting will also be seen. While HTTPS requests cannot be viewed in WireShark as they are encrypted, HTTP is be read by attackers/
Forms that has username and password for example, can be clearly seen.

This happens because the attacker can simply request the third handshake out of four in the key generation. Connecting to a Wi-Fi network requests 4-way security handshakes between the device and the network. This ensures devices and access points have the same password when joining a Wi-Fi network.
Simply by resending the third handshake over and over again, the encryption key generation can be manipulated.
Vanhoef explained that this exploit may allow packet sniffing, connection hijacking, malware injection, and even decryption of the protocol itself.
KRACK has many variants of attacks. The above is the simplest and the most effective.
