There is no end to malware as people continue to spread and install them.
Avast security researchers have found a malware strain named 'Rietspoof'. This multi-stage malware capable of dropping multiple malicious payloads have been spreading through social messaging apps like Facebook Messenger and Skype.
In the report, the researchers at the company said that the malware was first spotted in August 2018. But at that time, it was largely ignored due to its limited infection and much-less frequent activities.
But since January 2019, the malware experienced a noticeable uptick in distribution efforts, with it being updated nearly every single day.
"When we began tracking Rietspoof, it was updated about once a month. However, in January 2019, we noticed the update cadence change to daily," said the team at Avast.
And this is why the researchers are worried.
Avast's Threat Intelligence team has been tracking this particular malware due to its striking and unique features.
This malware is "multi-stage", and utilizes several different file formats combined. This makes it a potentially more versatile strain of malware.
Rietspoof is considered a downlaoder, and it's main role is to infect victims, gain persistence on infected hosts, and then download other malware strains, or depending on the orders it receives from a central command & control (C&C) server.
According to Avast on its blog post:
"The CAB file is expanded into an executable that is digitally signed with a valid signature, mostly using Comodo CA. The .exe installs a downloader in Stage 4."
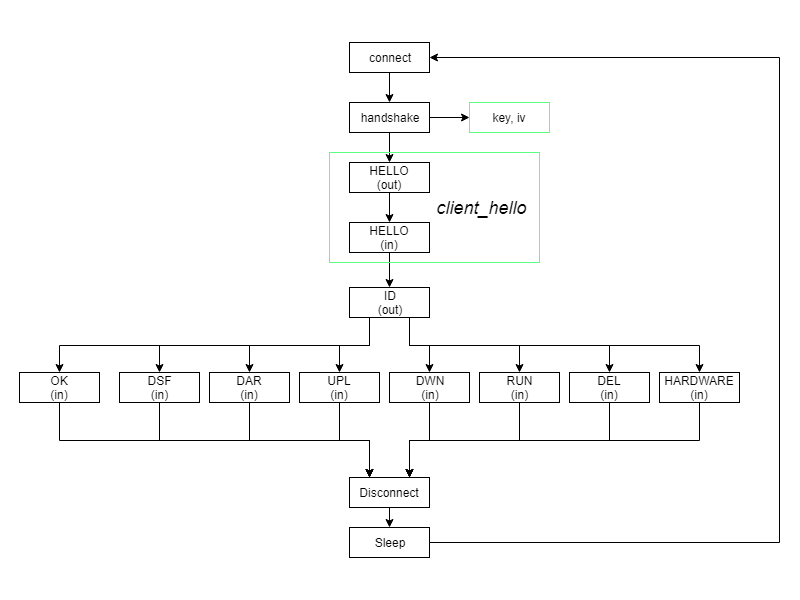
The malware's downloader uses a homegrown protocol to retrieve Stage 4 from a hard-coded address. While Stage 3 protocol includes bot capabilities, Stage 4 only acts as a designated downloader.
The C&C server was found to communicate to only with IP addresses in the U.S.. This leads to Avast in speculating that the malware is specifically made for targeted attacks, or only for testing reasons.
What makes this malware particularly dangerous is that, it can gain persistence by placing a LNK (shortcut) file in the Windows/Startup folder with the name WindowsUpdate.lnk.
This file runs an expanded PE file after startup to ensure the executable will run if the machine is rebooted.
This strategy is risky as most antivirus products do keep an eye on this folder. But according to Avast, this Rietspoof malware is signed using legitimate certificates, allowing it to bypass most security checks.
The infection routine is made up of four different stages: The actual Rietspoof malware is dropped in the first three stages, with the last stage being reserved for downloading a more intrusive and potent malware strain.
"We noticed that development of this third stage is rapidly evolving, sometimes running two different branches at once. During our analysis, the communication protocol was modified several times and new features were added. For example, string obfuscation was supported in earlier versions, implemented several days later, and then on the 23rd of January, we saw samples that rolled back some of these changes," said Avast.
Because Rietspoof is considered a "dropper" or "downloader," the malware strain is designed for the sole purpose of infecting victims with "something stronger."
While on its own, the malware's functionality is limited, it still can download, execute, upload or delete files. And in case of emergencies, it can also delete itself.
"Our research still cannot confirm if we’ve uncovered the entire infection chain. While the malware has bot capabilities, it seems to have been primarily designed as a dropper," said Avast.
"it is possible that there are more stages that haven’t been revealed yet."