
Businesses of all kinds hold some sorts of secrets and funds. And the larger they are, the more they have them.
In the modern days of the internet, data is stored locally, but more are relying on online servers or the clouds for convenience. And with many businesses start relying on blockchain and cryptocurrencies, money aren't anymore stored inside banks.
The advantages these two give however, pose security concerns.
Cybersecurity researchers from Prevailion found a dangerous kind of botnet on the loose that specifically target businesses to steal sensitive information and cryptocurrencies.
Dubbed the 'MasterMana Botnet', the researchers said that it's connected to the ongoing campaign by the 'Gorgon Group,' a hacker group that is linked to worldwide criminal activities and repeated attacks on governments.
According to Prevailion on its blog post:
"While most companies fear they may become compromised by advanced actors, this particular report highlights that actors do not have to rely on advanced tools or techniques to have a serious business impact."
The botnet works with hackers first tricking victims into opening a phishing email.
Opening this malicious email would force the victim's machine into downloading a malicious .Net DLL file. This file when installed, will assume system processes, before installing a trojan that acts as a backdoor for RAT (Remote Access Trojan).
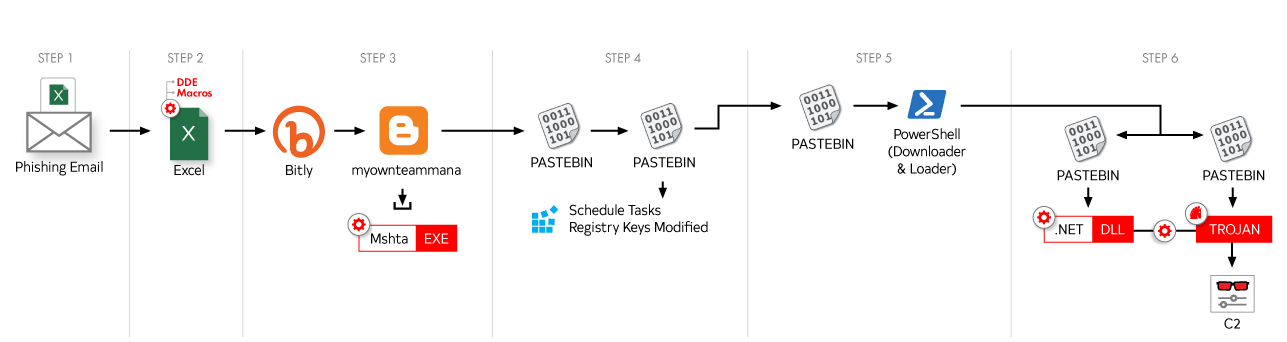
This RAT resembles the Revenge RAT or the Azorult variant, as it can remotely upload and download files, take screenshots of the victim's machine, and deploy additional attacks, such as planting cryptomining malware.
It can go worse than that, as the RAT can also install ransomware, steal login credentials, browsing history, cookies, and steal cryptocurrencies from wallets.
MasterMana Botnet is capable of evading detection by relying upon trusted placed in a number of third-party websites and services, like Bitly, Blogspot, and Pastebin, rather than remote domains controlled by the hackers.
Prevailion highlighted how cheap this hacking campaign is to run, as it leverages well-known trojans sold on dark web forums for $100, and additional costs coming from leasing Virtual Private Servers, which cost about $60.
"The cost for the threat actors to deploy and maintain the campaign was virtually nonexistent," concluded the researchers, adding that about 3,300 machines have been infected as of the discovery.
The firm warns that this botnet may continue to spread, with the hackers persisting their campaign.
"[P]revious public reporting has not deterred them, therefore we wanted to highlight their new modus operandi, so that network defenders may more easily identify their operations," the researchers said.