
The U.S. Federal Bureau of Investigation (FBI) said that restarting a model router can reduce the exposure of malware.
A Cisco cybersecurity team said that at least 500,000 routers in 54 countries were impacted by the malware, known as VPNFilter. The software reportedly targets consumer-level routers that are popular for home and small offices uses.
With the malware infecting the devices, hackers can steal website credentials, control local traffic and even wipe the routers, destroying them and cutting users off from the internet. Routers from Linksys, Netgear, TP-Link, and MikroTik were reportedly vulnerable, as well as QNAP network-attached storage (NAS) devices, according to researchers at Cisco.
But for a workaround, the FBI recommends users to restart their routers.
According to the FBI in a warning posted to the Internet Crime Complaint Center (IC3) website:
"The actors used VPNFilter malware to target small office and home office routers. The malware is able to perform multiple functions, including possible information collection, device exploitation, and blocking network traffic."
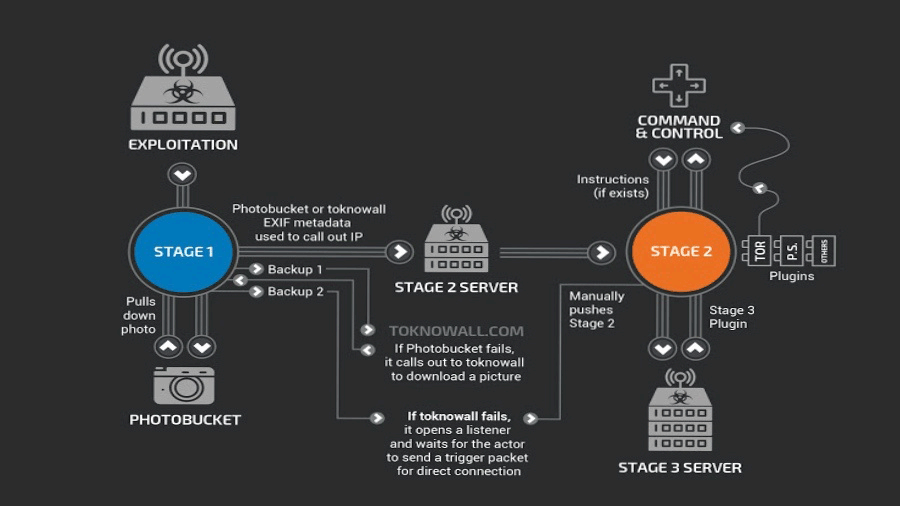
According to a report, VPNFilter is a product of a group known by names of "APT28," the security industry codename for a "Fancy Bear” and the “Sofacy Group.”
This is the same group that is said to be state-sponsored, responsible for the hacks of emails from the Democratic National Committee and the Hillary Clinton campaign in 2016. The group has also been linked with the Russian government.
The malware is "one of the few Internet-of-Things infections that can survive a reboot," because its persistent first stage of infection can use automated remote systems to install or re-install its second or third stages. But according to the FBI, rebooting also means that the hackers will be more likely to require more labor-intensive method to re-infect those devices.
This is because unplugging the router sets this complicated malware back to stage one of the infection.
Rebooting can also help the government teams "identify and remediate the infection worldwide," by tracking communications sent by infected devices after they’re rebooted.
Further reading: FBI Seizes Domain Responsible For Major Russian Botnet