The end-to-end encrypted messaging app Signal, is popular due its way of preserving its users' identity and messages.
Signal is not the only app in the business, as others like Telegram and even WhatsApp also use end-to-end encryption. However, all of those apps actually still leave some metadata information behind that can reveal who sent the message to whom and when.
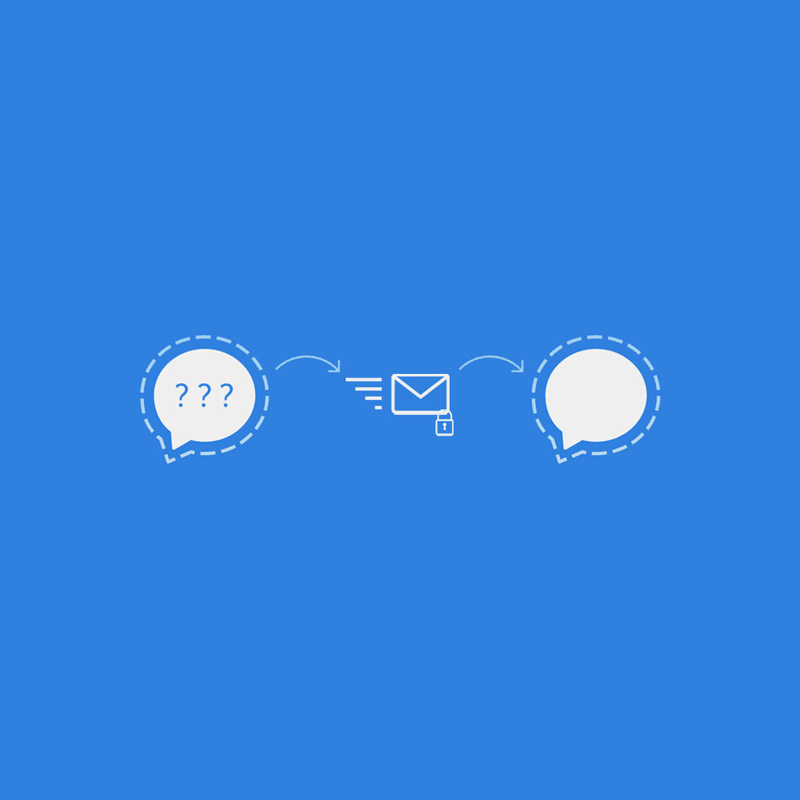
This is where Signal is introducing 'Sealed Sender', a method to further reduce the amount of information that is accessible, including to the company itself.
While Signal claims to never store metadata or logs, Sealed Sender aims to protect users' identity in case of the communication is somehow intercepted. When this happens, hackers sitting inside the service will only see encrypted messages going to their destinations, and won't be able to see where they came from.
According to a blog post published by Signal, the Sealed Sender feature uses an encrypted "envelope" containing the sender's identity and the message ciphertext, which is then decrypted at the recipient part with their own identity keys.
"While the service always needs to know where a message should be delivered, ideally it shouldn't need to know who the sender is," Signal developer Joshua Lund said. "It would be better if the service could handle packages where only the destination is written on the outside, with a blank space where the 'from' address used to be."
The Sealed Sender process can be summarized into the following steps:
- The app encrypts the message using Signal Protocol, just like usual.
- Signal includes the sender's certificate and encrypted the message in an envelope.
- Signal then encrypts this envelope using the sender and recipient identity keys.
- Without authenticating, Signal sends the encrypted envelope to the service, with the recipient’s delivery token.
- The message recipient can then decrypt the envelope by validating the identity key to know the sender of the message.
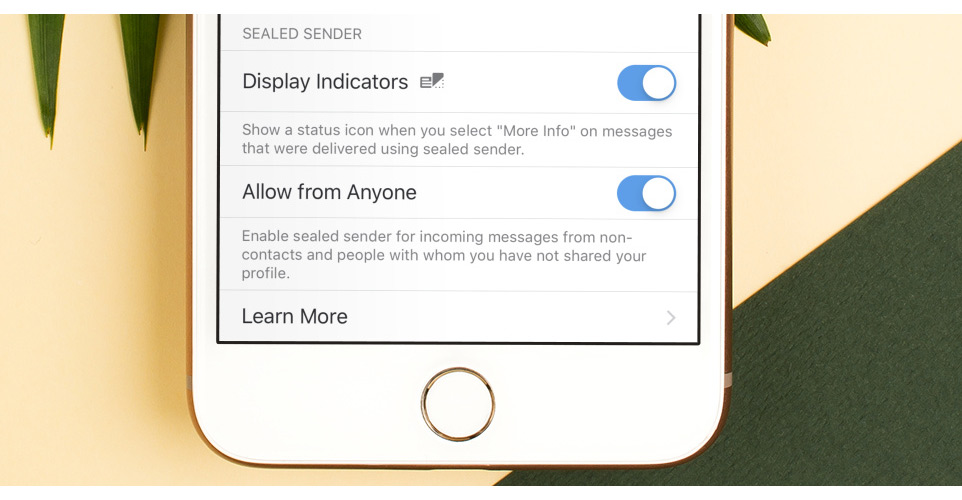
As much as it values privacy, Signal still needs to see where users' messages are going so it can delivering them to the right recipients. The service has also relied on seeing what account a message came from to help verify that the sender is legit, limit the number of messages an account sends in a period of time to prevent it from spamming, and offer other types of anti-abuse checks.
"While the service always needs to know where a message should be delivered, ideally it shouldn’t need to know who the sender is," explained Moxie Marlinspike, the creator of Signal. "It would be better if the service could handle packages where only the destination is written on the outside, with a blank space where the 'from' address used to be."
This is where Sealed Sender takes its role. Initially the feature is introduced in beta version of the Signal app.
Sealed Sender can improve users' privacy and identity to a new level. What should be noted is that, this technique also eliminates Signal's ability to validate senders' certificate that was being used to prevent abuse and spoofing. However, the company has introduced additional workarounds that still allow users to verify who sent the incoming messages.
Most importantly, Signal only allows Sealed Sender messages to go between accounts that have already established trust, particularly by being in each others' contact lists.
Besides protecting users using the Sealed Sender feature, Signal is also developing ways to also encrypt users' IP addresses and other sensitive metadata information that could be revealed by analyzing users' network traffic.
"These protocol changes are an incremental step, and we are continuing to work on improvements to Signal’s metadata resistance," said Signal.