
Crypromining malware isn't anything new. But when it comes with a more sinister purpose, that malware is indeed something else.
Cybersecurity researchers from TrendMicro have identified a strain of Linux malware that does two things: First, it can mine cryptocurrency illicitly on infected systems, and second, it can also provide the attackers with universal access to an infected system via a “secret master password.”
Called the 'Skidmap', this malware can hide itself and its cryptocurrency mining activities by faking network traffic and CPU-related statistics.
According to TrendMicro’s researchers on a blog post announcing their finding:
"These kernel-mode rootkits are not only more difficult to detect compared to its user-mode counterparts — attackers can also use them to gain unfettered access to the affected system."
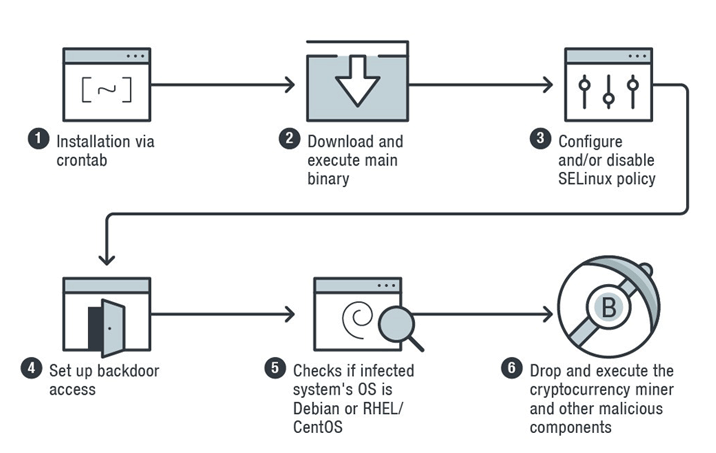
To infect a machine, the malware installs itself via 'crontab', which is the standard process that periodically schedules time jobs in Unix-like systems.
Skidmap then installs multiple malicious binaries, with the first payload is to minimize the infected machine’s security settings so that it can begin mining cryptocurrency undetected.
"Upon execution of the 'pc' binary, it will decrease the affected machine’s security settings. If the file /usr/sbin/setenforce exists, the malware executes the command, setenforce 0. This command configures the system’s Security-Enhanced Linux (SELinux) module, which provides support in the system’s access control policies, into permissive mode — that is, setting the SELinux policy so that it is not enforced," explained the researchers.
"If the system has the /etc/selinux/config file, it will write these commands into the file: SELINUX=disabled and SELINUXTYPE=targeted commands. The former disables the SELinux policy (or disallows one to be loaded), while the latter sets selected processes to run in confined domains."
After that, Skidmap sets up a way for it to gain backdoor access to the machine.
It does this by having the binary to add the public key of its handlers to the authorized_keys file, which contains keys needed for authentication.
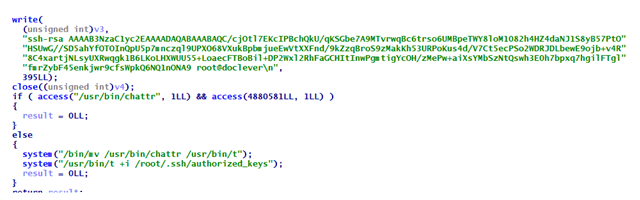
Then, it creates another way for its operations to gain full access to the infected machine.
This is by replacing the infected system'spam_unix.so file (the module responsible for standard Unix authentication), with its own malicious version, that accepts specific password for any users. Doing this allows attackers to log in to the infected system as any user they wish.
And for last, more binaries are installed into the system to monitor the cryptocurrency miners as they work to generate digital money for the attackers, and making sure that the miners can work without being detected.
Skidmap "uses fairly advanced methods to ensure that it and its components remain undetected," to an extent that TrendMicro warned that removal of the malware can be difficult.
This is because the malware uses Linux Kernal Module (LKM) rootkits, which essentially overwrite or modify parts of the OS kernel.
Furthermore, Skidmap is also reportedly designed to be capable of reinfecting machines that have been cleaned or restored following an infection.
"Cryptocurrency-mining threats don’t just affect a server or workstation’s performance — they could also translate to higher expenses and even disrupt businesses especially if they are used to run mission-critical operations," wrote TrendMicro.
To protect against Skidmap, TrendMicro urges system administrators to always the adopt best practices, like keeping systems and servers patched and updated, and beware of unverified, third-party repositories, and enforce the principle of least privilege to prevent suspicious and malicious executables or processes from running.
