
Researchers have found several security flaws in popular corporate VPNs, which allowed malicious actors to break into clients' networks and steal business secrets.
According to Devcore researchers Orange Tsai and Meh Chang, the flaws were found on Palo Alto Networks, Pulse Secure and Fortinet. The three corporate VPN providers are said to be “easy” to remotely exploit.
Corporate VPNs like the three, allow employees to enter their corporate username and passwords, often using a two-factor authentication for improved security.
Using Secured Sockets Layer (SSL) connection, these VPN providers would then create a secure encrypted tunnel between the user's computer and the corporate network.
The bug the researchers found, allows malicious actors to enter the corporate intranet without needing any authentication.
According to Tsai:
“The SSL VPN is the most convenient way to connect to corporate networks. On the other hand, for hackers, SSL VPN must be exposed to the internet, so it’s also the shortest path to compromise their intranet."
"A few SSL VPN vendors dominate the market — therefore, if we find any vulnerability on these vendors, the impact is huge."
In the researchers' first write-up detailing the bug, they said that a format string flaw, such as an inputted text that isn’t properly understood by the server, can crash the service altogether.
The researchers tested their findings on Palo Alto’s GlobalProtect VPN by hacking to Uber's internal servers. The researchers also tested it on Twitter, saying that: “We got the root privilege on Twitter’s most important VPN server successfully and got the highest severity and the highest bounty from their bounty program," Tsai said.
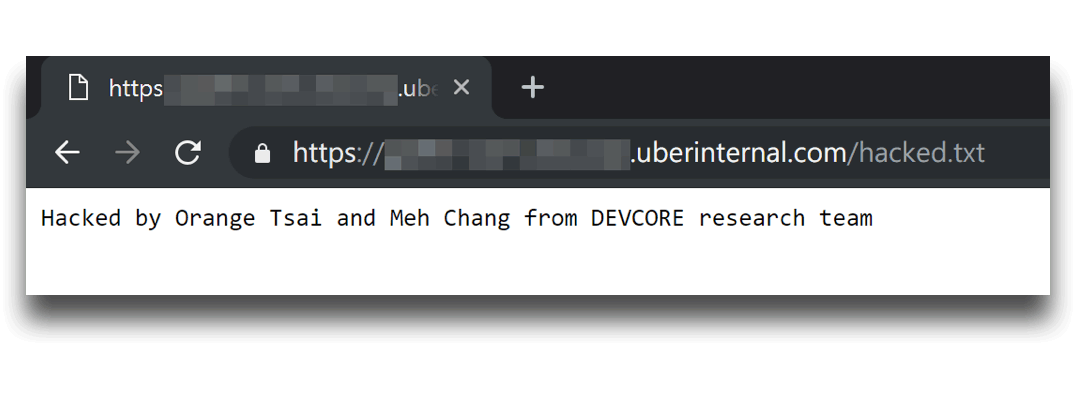
Tsai further explained that:
The researchers contacted Palo Alto about the bug.
The company responded by saying that the bug in question has already been "found internally", explaining why it didn't issue any public security advisory. But after Tsai and Chang’s write-up, Palo Alto eventually issued an advisory.
Pulse Secure’s chief marketing officer Scott Gordon said the company notified its customers of the vulnerability, and had pushed a patch to all of its users. Fortinet also released advisory to the bug, and updated its software to fix the issue.
Fortinet also released advisories for their respective bugs and have updated new firmware to fix the vulnerabilities. The company advises all system administrators to update their vulnerable gateways to the latest versions.
While consumers utilize VPNs to bypass region blocks and to protect their online privacy, businesses often use corporate VPNs to allow employees who work remotely to access resources from their corporate network.
The flaws here, happened not on how the VPNs work, but on the VPNs themselves.