There are many kinds of malware in the wild, and stalkerware is considered one of the worst for privacy.
Stalkerware in apps allows the software maker to spy on users' information, as well as accessing their messages, call information and GPS location. They can also be developed to covertly record emails, and to eavesdrop on phone calls
According to a finding by Kaspersky, the cybersecurity firm recorded 518,223 cases where the presence of stalkerware on users’ devices was registered, or attempted without the consent of the victims involved.
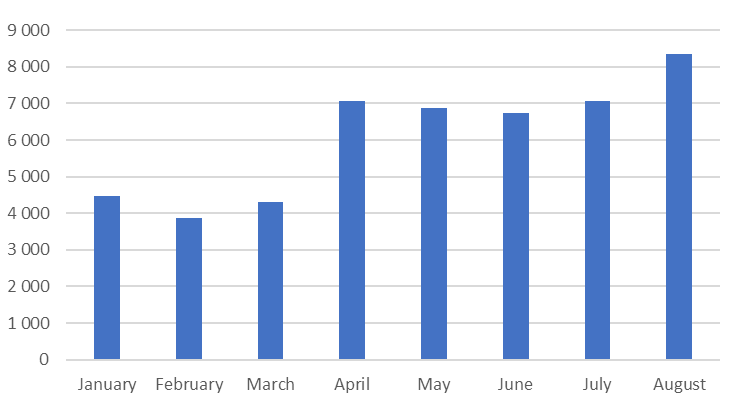
This is a staggering 373 percent increase during the first eight months of 2019, when compared to the same period the year before.
Kaspersky also found 37,532 users who encountered such apps at least once, a 35 percent jump year over year.
Globally, most of the stalkerware victims come from Russia, India, Brazil, and the U.S.. And in Europe, the top three are Germany, Italy, and the UK.
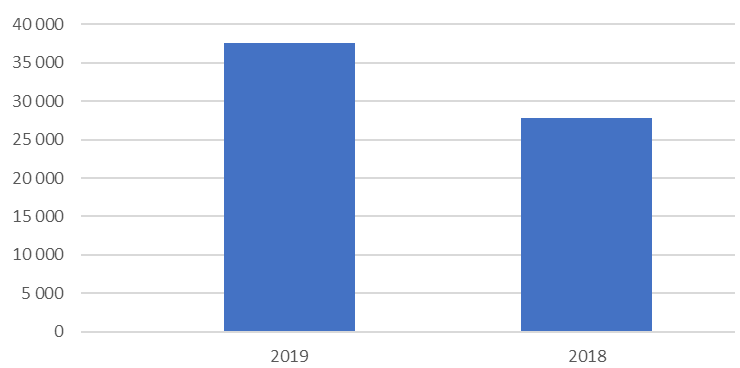
Stalkerware is considered a 'nuisanceware' because just like spyware, it's annoyingly malicious. Both software result in the theft of personal data.
But the main difference between stalkerware and spyware is that, the former is mostly used by individuals to spy on people that are close to them. And as for the latter, it's most often deployed to hunt as many personal information as possible, no matter who's the victim.
According to the researchers at Kaspersky:
Kasperky continued by saying that:
"In addition, the application provides the ability to remotely control the device. As well as all of this, there is a possibility of working in a hidden mode under the disguise of system applications."
As for the method of infection, stalkerware needs a vector to infiltrate a target’s mobile device defenses.
Most often, this can be accomplished by manually installing the app on victim's device. Other times, stalkerware apps can also remotely administered through spear phishing emails containing malicious attachments or links. When opened, the victim's device will automatically download the payload without the victim's knowledge.
What makes stalkerware difficult to apprehend is because it's often masqueraded as parental control apps or an anti-theft apps.
The most prolific stalkerware family in 2019, according to Kaspersky:
Monitor.AndroidOS.MobileTracker.a, which affected 6,559 unique users.Monitor.AndroidOS.Cerberus.a, which was detected on the devices of 4,370 users.Monitor.AndroidOS.Nidb.a, found on 4,047 users.
This is not the first time stalker apps have been found on Android. Earlier, researchers from cybersecurity firm Avast detected at least seven stalkerware apps on the Google Play Store.
Kaspersky's finding however, is unlike Avast's discovery, as the majority of the stalkerware encountered aren't available on official app stores.
In other words, the "installation requires access to a dedicated website and access to the victim’s device."