In the evergrowing world of internet, data transactions happen all the time. And this is why there should be a way to properly secure sensitive data as they are delivered from one place to another.
One of which, is by isolating the data and state to increase the security and robustness of many applications. Examples include protecting cryptographic keys against exploits like OpenSSL's Heartbleed bug or protecting a language runtime from native libraries written in unsafe languages.
However, isolating cryptographic session keys in a network-facing application or isolating frequently invoked native libraries in managed runtimes, require very frequent domain switching.
This can result in bloated overhead, affecting performance.
As a solution, ERIM which uses hardware-enforced isolation with low overhead, is seen an improvement to previous approaches.
Even at high switching rates, ERIM’s average overhead is less than 1% for 100,000 switches per second. And when applied to NGINX web server, ERIM can decrease web requests throughoutput to within 5% of a normal server.
In other words, ERIM should perform faster.
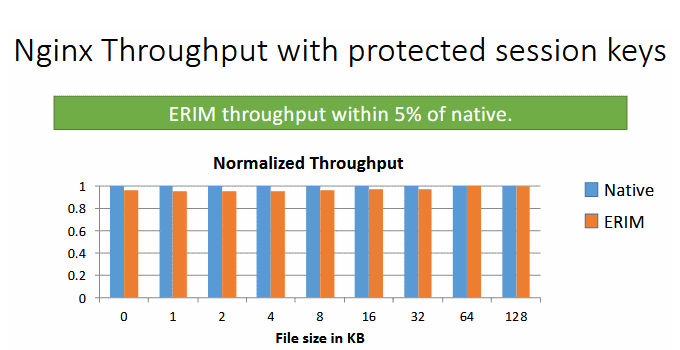
ERIM is faster, but also secure.
The key idea, according to its researchers' paper (PDF) titled 'ERIM: Secure, Efficient In-process Isolation with Protection Keys (MPK)', is by combining memory protection keys (MPKs), a feature added to Intel CPUs that allows protection domain switches in userspace, with binary inspection to prevent circumvention.
This allows data to be processed directly inside an Intel CPU, and to be split across multiple CPU memory virtual pages.
Using ERIM, each memory page is signed by a 4-bit domain ID, allowing an app's process space to be split into smaller domains where data can be safely processed, and achieved using in-process data isolation.
As a result, ERIM has a near-zero performance overhead.
To keep security intact, ERIM also uses binary inspection technique to watch out for PKRU modifications (a register that controls which app components can write to which CPU virtual memory page).
Here, ERIM can determine if these PKRU modifications are "safe" and even rewrite binary code to eliminate "unintentional occurrences of PKRU-updating instructions," effectively keeping an app's MPK implementation secure from malicious code attempting to bypass the feature.
Traditionally, when an app uses Intel MPK security feature, switching between domains can slow down the speed of an app to read data, resulting in performance loss.
Furthermore, just using MPK doesn't guarantee in-process data isolation, as a malicious component can grant itself the ability to modify the PKRU, effectively neutralizing MPK as a security feature.
By combining MPK with binary inspection, ERIM can preserve security while keeping low overhead.
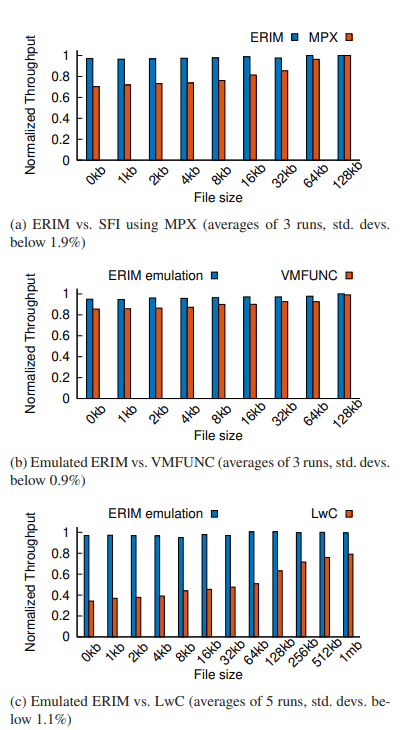
According to its researchers, ERIM outperformed all other code isolation techniques, such as SFI MPX, VMFUNC, or LwC.
So here, ERIM's approach benefits both worlds.
With servers around the world processing a lot of sensitive data at any given time, security and speed are certainly in demand. Both end users and providers want to benefit the two, as they are expecting more and more information transaction.
ERIM can be applied with little effort to new and existing applications, doesn’t require compiler changes, can run on a stock Linux kernel, and has low runtime overhead even at high domain switching rates.
These advantages should make the method a cost-effective way to protect sensitive data such as encryption or session keys on web servers, as well as eliminating all other issues that made in-process code isolation a problem for the developer community.