When the demand and usage of cryptocurrency rises, so do cryptominers and the cryptojacking craze.
Some people have said that using scripts to mine cryptocurrencies when people visit websites could be a legitimate form of monetization, providing revenue so websites can live without ads. However, such feat requires websites to let visitors know that they are using the CPU resources of visitors.
But the thing is, it's not quite clear how effective this "legitimate" cryptojacking would work on a long-term basis.
And this resulted to thousands of websites, including government websites, caught serving cryptominers script to mine the cryptocurrency. This happens not because those websites were willing to put the mining script on their pages themselves, but have the scripts put without their knowledge.

Knowing The Weak Link
Most if not all cryptominers have one common strategy:
If you want to load one cryptominer to 1000+ websites, you don't attack all that 1000+ websites. Instead, just attack 1 website that the remaining 999+ use to load their contents from. In this case, the it's a compromised third-party script provider.
By loading JavaScript directly from a compromised third-party script provider, the websites were becoming prone to injection-style attacks. This particular approach is appealing to attackers who are able to compromise users at scale by attacking dependencies being loaded dynamically.
Even if the third party providers are known to be reliable, they can still be unknowingly compromised, allowing attackers to use them as a method for malicious injections.
How To Protect Your Website
It's nothing new to hear CDNs or other websites that host website assets becoming prime targets. Compromising one CDN, for example, allows attackers to potentially attack thousands of other websites that use resources hosted by the CDN.
But the thing is, you as a website owner can defend yourself easily against this type of attack.
The best approach is to add Subresource integrity (SRI), and use Content Security Policy (CSP) to enforce the use of SRI tags.
SRI here allows visitors' browser to determine if the file has been modified, which allows it to reject the file. You can generate the appropriate script tags using the SRI Hash Generator and adding the generated tag to your website to ensure that the cryptominer won't load on your pages. And as for the CSP, it's a directive to make sure that no script is allowed to load on the page without having a SRI attribute on it.
The example below shows a standard way to load a script file. Using the following, visitors' browser will go to the URL and fetch that file and include it on your page. If compromised, it can include a call for a cryptominer.
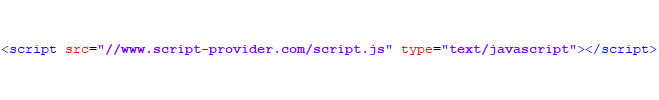
Change this to:
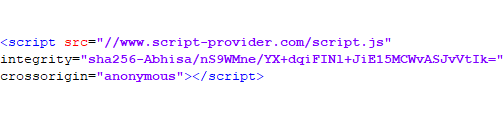
This would alter how the script is loaded, making possible attack to be completely neutralized. The SRI attribute allows visitors' browser to reject the script file when it knows that the file has been compromised.

The method by Scott Helme can certainly help many websites out there that want to prevent any compromised scripts to run on their websites,
However, it should be noted that it may not work well if the script needs to be updated regularly. CSP here is useful in restricting external JavaScripts from being loaded on a website, but it's not meant to assure the integrity of scripts that it expects to load.
Implementing whitelist-based CSP can be difficult, and skilled attackers may still be able to initiate their attack because CSP for prevention won't work on whitelisted domains.
If you see that SRI and CSP are falling short, the solution is to monitor your Webpage DOM and JavaScript environment for any injection. With you paying attention to any changes in real-time, you can search for DOM modifications, JS poisoning attacks, JS event-hijacking and XSS, detecting any changes that may have happened.
Because after all, in worse case scenario, attackers may not just care about stealing your visitors' CPU resources for mining cryptocurrency.
Scripts can do a lot of things to your website, and being compromised may allow them to execute arbitrary JavaScript on your pages to collect any sensitive information that the user accesses, such as credit card details or banking information.
Attackers can also modify the DOM to trick your users into giving away their credentials or perform actions that only for the interest of the attackers.
Further reading: Cryptocurrency Mining, And How You Can Be Part Of It, In A Good Way