In the tech world where businesses need to compete to get even the slightest increase in users, Apple doesn't really much care.
After all, the tech giant is almost synonymous with iPhones, iPads and the tech culture, and that the company is already a $3 trillion business. But there is a problem with that, in which it stems from the way Apple is conducting its business.
Apple has a number of software, but most of its software products aren't meant to run on any other platform other than Apple's.
What this means, if an issue happened to be found in one of its products, it's like saying all Apple users are affected.
And this time, a bug in Safari's API is leaking information about users' browsing habit.
The leak can be worse if the data is attached to users Google Account, according to findings from FingerprintJS, a browser fingerprinting and fraud detection service.
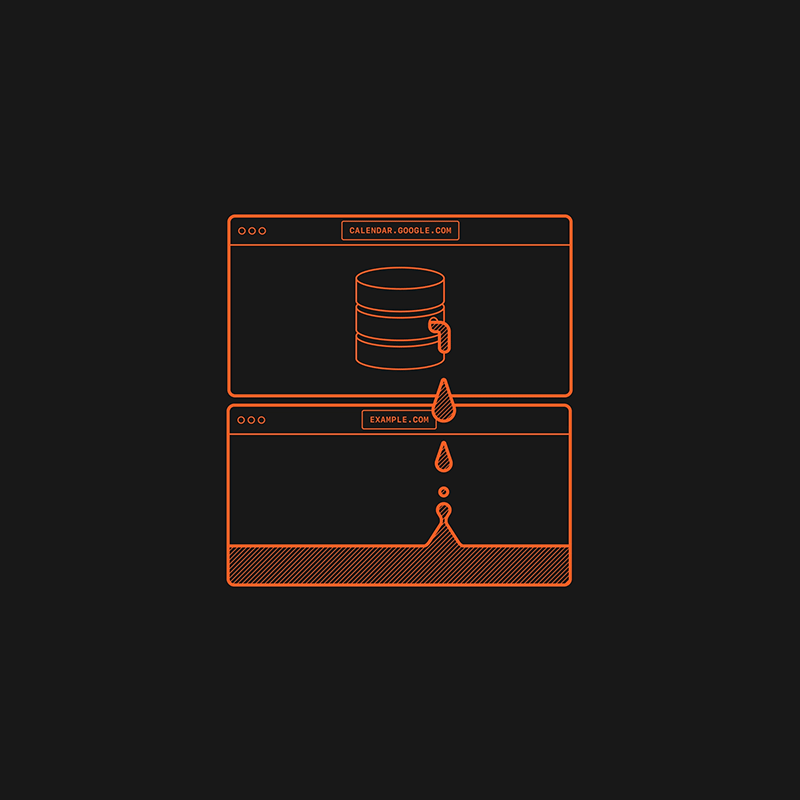
The vulnerability issue stems from the way Apple's iOS implements IndexedDB, a low-level JavaScript application programming interface (API).
IndexedDB API is widely used by browsers as their client-side storage, in order to store databases.
Normally, the use of a "same-origin policy" by the IndexedDB API should limit what data can be accessed by which website, and typically makes it so that a site can only access data that it generated, not those of other sites.
Same-origin is a fundamental security mechanism to ensure that resources retrieved from distinct origins, like for example, using a combination of the scheme (protocol), host (domain), and port number of a URL, ensuring that they are isolated from each other.
By restricting how a script loaded by one origin can interact with a resource from another origin, the API is meant to prevent potentially malicious scripts to steal data or run arbitrary code.
But here, indexedDB on Safari 15 for macOS, iOS, and iPadOS, was found to violate that same-origin policy.
"In Safari 15 on macOS, and in all browsers on iOS and iPadOS 15, the IndexedDB API is violating the same-origin policy," Martin Bajanik wrote in FingerprintJS' blog post. "Every time a website interacts with a database, a new (empty) database with the same name is created in all other active frames, tabs, and windows within the same browser session."
This issue can allow websites to learn from other websites Safari 15 users have visited in different tabs or windows within the same session.
In part, this is due to databases having generally unique and website-specific names.
"A tab or window that runs in the background and continually queries the IndexedDB API for available databases can learn what other websites a user visits in real-time," the blog post said. "Alternatively, websites can open any website in an iframe or popup window in order to trigger an IndexedDB-based leak for that specific site."
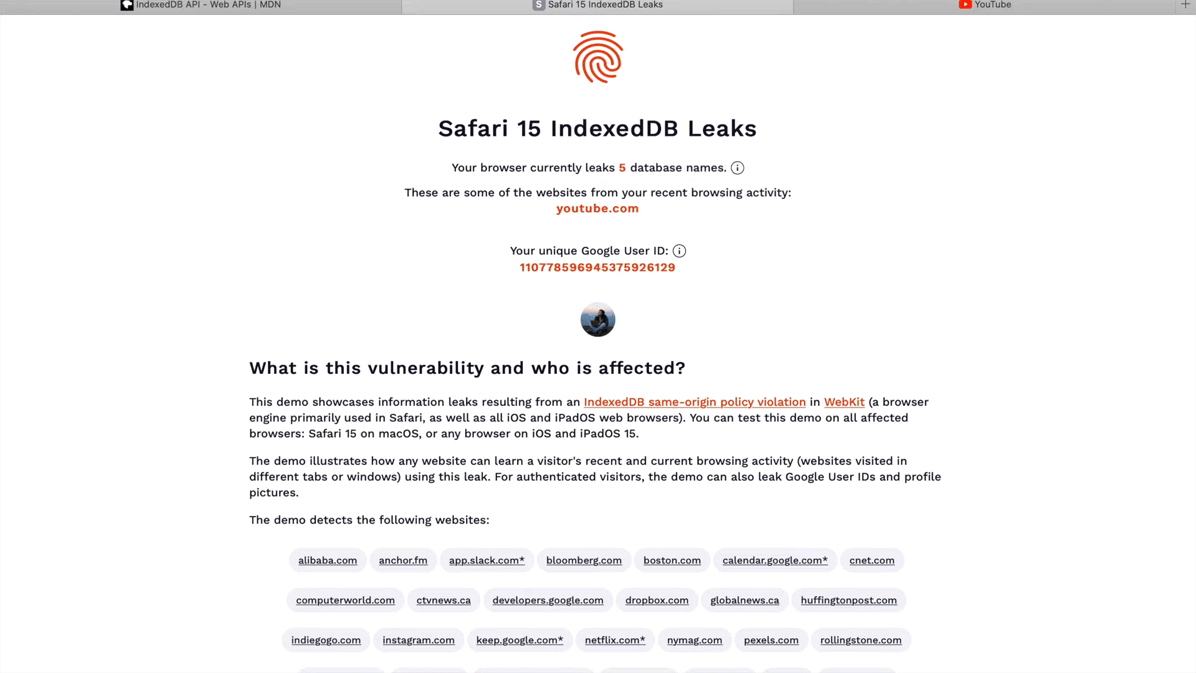
The problem is worsened as some websites use database names that include unique identifiers specific to a user. For websites that can share the same authentication credentials, such as Gmail and YouTube, the database name can include the same authenticated Google User ID.
This bug can potentially leak sensitive information about users' browsing habits, an issue that could be used to reveal the users' identity.
As for the latter, the problem is caused by the internal identifier Google uses in Google User IDs.
The leak in question can be used to pull personal information directly from Google's APIs using this identifier, which could help websites to fully identify users.
In a test that was conducted by the researchers, it was found that indexed databases with universally unique identifiers were created by ad networks.
"Not only does this imply that untrusted or malicious websites can learn a user's identity, but it also allows the linking together of multiple separate accounts used by the same user," Bajanik said.
It's worth noting that using a private window doesn't protect users from this issue. But for what it's worth, browsing sessions using a single tab can extremely limit its effect.
And fortunately, Safari's tracking prevention features are able to prevent database names from being leaked in this manner.
The issue is only found on Safari 15, due to their use of WebKit.
The bug also affects third-party browsers like Chrome on iOS 15 and iPadOS 15, as Apple requires all browsers running on iPhones and iPads to use WebKit.
A bug report has been submitted to the WebKit maintainers on November 28, 2021, with hopes that the bug gets fixed as soon as possible.
But since Apple failed to release a fix for the bug, the researchers have no other choice but to publicize their findings so the public can know about its existence and take precautions.
Apple has continuously attempted to make Safari privacy-focused, with the introduction of initiatives to prevent cross-site tracking and the Safari Privacy Report meant to help protect users. Unfortunately for Apple, this bug can literally undone everything.
Due to the way the problem manifests, there's little that Safari users can actually do.
Users can block JavaScript by default and enables it only on trusted site. But the thing is, this will greatly harm browsing experience.
Another alternative is to use a different browser that doesn't use WebKit. This is possible on macOS, but the option is not available to iOS and iPadOS users.
Ultimately, the researchers admit, "the only real protection is to update your browser or OS once the issue is resolved by Apple."
"This is a huge bug," said developer advocate for Google Chrome Jake Archibald tweeted. "On OSX, Safari users can (temporarily) switch to another browser to avoid their data leaking across origins. iOS users have no such choice, because Apple imposes a ban on other browser engines."
This is a huge bug. On OSX, Safari users can (temporarily) switch to another browser to avoid their data leaking across origins. iOS users have no such choice, because Apple imposes a ban on other browser engines. https://t.co/aXdhDVIjTT
— Jake Archibald (@jaffathecake) January 16, 2022
