
Google and Apple are two adversaries. But that doesn't mean one should stay quiet when an exploit is found on its competitor.
Working with Google's Threat Analysis Group (TAG), researchers from Google Project Zero have discovered what appears to be a concentrated malware campaign targeting iPhones, which utilizes zero-day vulnerabilities in iOS to lurk for at least two years and steal user data.
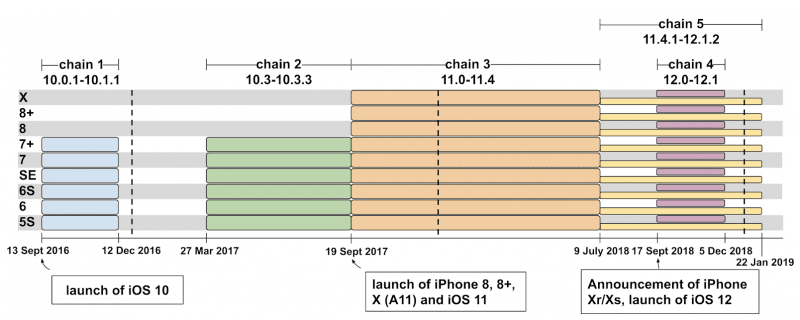
Project Zero, the search giant’s security team that is tasked with finding vulnerabilities in the wild, said that a small collection of websites could be used to hack iPhones, using previously undisclosed five different exploit chains.
The chains leveraged 14 different vulnerabilities that happened to be found on every version of iOS from 10 to 12.
According to Ian Beer from Project Zero, in a blog post.
"There was no target discrimination; simply visiting the hacked site was enough for the exploit server to attack your device, and if it was successful, install a monitoring implant. We estimate that these sites receive thousands of visitors per week."
The exploits that are called 'Watering Hole Attacks', allow hackers to compromise specific group of iPhone users by first infecting websites that they are known to visit.
Using the malware and/or maladvertisements, the hack involves 14 exploits that span across Safari and the iOS kernel (the core of the operating system), aside from two separate instances of sandbox escapes, wherein arbitrary code can be executed outside of an application’s confinement.
The five attack chains can grant hackers an elevated "root" access, giving them full permissions to install malware and access files that are otherwise hidden, as well as the ability to upload photos, messages, contacts and user location once every 60 seconds to its Command and Control server.
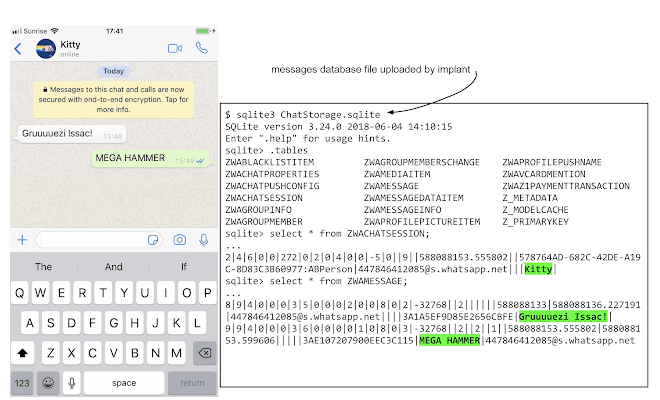
Making things worse, the malware also uploads the keychain, which is used by iPhones to securely store data such as Wi-Fi passwords, login credentials, and certificates, as well as data containers associated with a hard-coded list of third party apps like WhatsApp, Telegram, Skype, Facebook, Viber, Gmail, and Outlook.
It's alarming because this method particularly bypasses end-to-end encryption (E2EE) used on apps like WhatsApp, Signal and Telegram.
E2EE secures data from man-in-the-middle attacks when it’s in transit. But because the malware infects the 'end' part of the process, the E2EE serves no purpose. This is why the attackers can get their hands on the what-supposed-to-be-encrypted data, as plain text.
Fortunately, the malware wasn't persistence, meaning that "if the phone is rebooted then the implant will not run until the device is re-exploited when the user visits a compromised site again" explained Beer.
"All that users can do is be conscious of the fact that mass exploitation still exists and behave accordingly; treating their mobile devices as both integral to their modern lives, yet also as devices which when compromised, can upload their every action into a database to potentially be used against them," Beer added.
Project Zero usually give 90-days disclosure period when it finds vulnerabilities in the wild and disclosed them to the developers behind the product.
But in this case, it only gave the iPhone maker a week to fix the vulnerabilities given the seriousness of the vulnerabilities.
While the worst should be over, the researchers at Project Zero warns that it's possible for others that are yet to be seen.
In the meantime, iPhone users should check for their iOS version to ensure that it's already updated to at least version 12.1.4, which was released on 7 February 2019.
That software update has included all the necessary patches needed for preventing the Watering Hole Attacks.