Vulnerable File Manager plugin versions for WordPress have exposed at least 600,000 websites to hackers.
The flaw allowed unauthenticated users to run the file manager commands by directly accessing an unprotected file from its elFinder package. The flaw was patched within hours after the plugin's developers updated it to version 6.9, which solves the issue.
But apparently, things were far from over.
Attacks continue to happen as hackers kept on trying to exploit the flaw.
It was reported that at least 1.7 million WordPress websites were probed by actors with malicious intentions between September 1 and September 3.
A week later, on September 10, that number went up to 2.6 million.
The zero-day flaw was first reported by Seravo's security researcher Ville Korhonen.
What made the incident interesting is that, multiple threat actors are somehow in a war against each other.
With the many WordPress websites vulnerable if they haven't update to File Manager 6.9, hackers that managed to compromised a WordPress website using the old File Manager plugin, also injected code to harvest user credential.
They also inject a backdoor, and also attempt to block other hackers from hacking the site, by password-protecting the exploitable file on the compromised sites.
This effectively prevented other hackers form exploiting the same vulnerability.
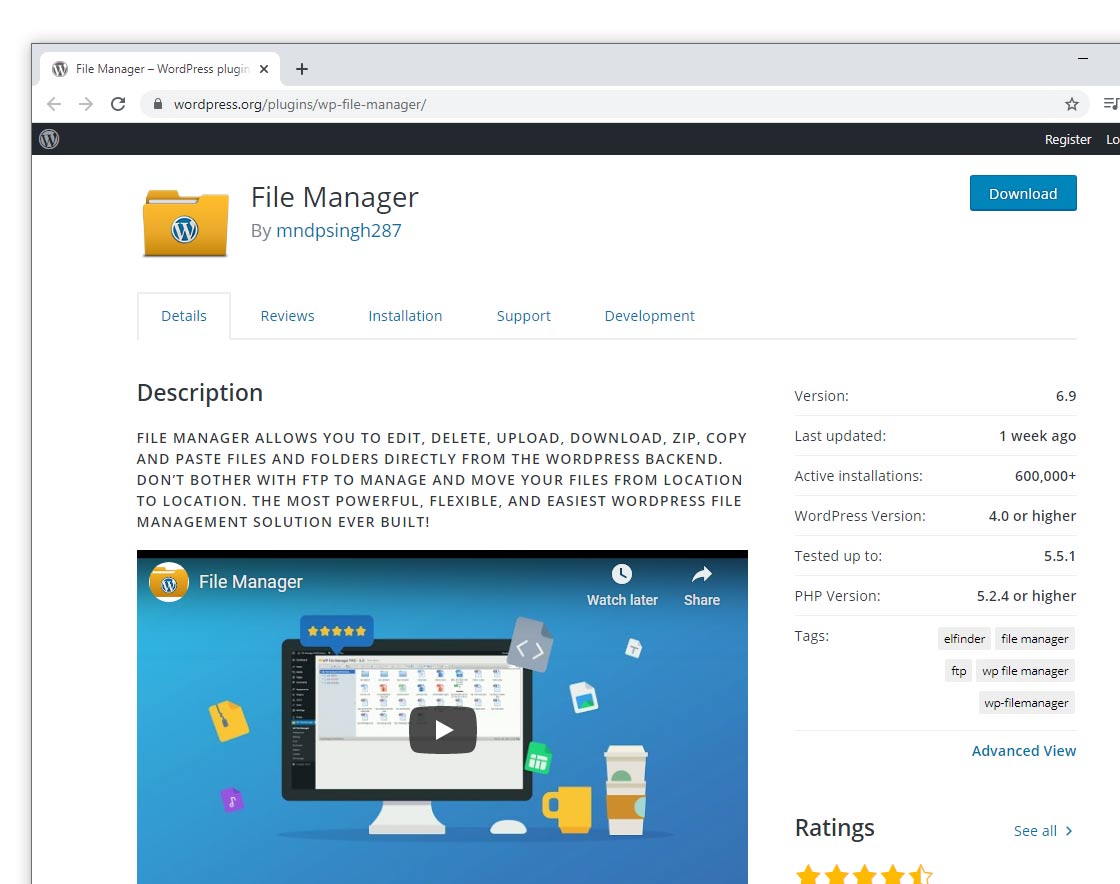
What makes this File Manager bug so devastating is that, the plugin is popular for administrators to manage files on their sites.
The plugin contains an additional file manager known as elFinder, an open source library that provides the core functionality in the plugin, along with a user.
"A file manager plugin like this would make it possible for an attacker to manipulate or upload any files of their choosing directly from the WordPress dashboard, potentially allowing them to escalate privileges once in the site's admin area," Chloe Chamberland, a researcher at Wordfence, in a blog post.
"For example, an attacker could gain access to the admin area of the site using a compromised password, then access this plugin and upload a webshell to do further enumeration of the server and potentially escalate their attack using another exploit."
It should go without saying that anyone running a WordPress website, or any other Content Management Systems (CMS) should be very picky about what third-party plugins they install.
They need to have an eye on every security updates, and apply them as soon as possible, or as necessary.