
Intel, one of the biggest computer chip maker for PCs, has benefited from a huge market share, competing directly against AMD, IBM and Nvidia.
But a big pie of the market doesn't mean that its products are flawless. Take for instance, the 'Meltdown' and the 'Spectre' vulnerabilities, or the 'Zombieland', 'Ridl' and 'Fallout' bugs.
This time, researchers from BitDefender have discovered yet another vulnerability.
On its report, the team at the cybersecurity solutions provider found a flaw in all modern Intel processors running Microsoft Windows operating system.
And what makes it concerning is that, the flaw is capable of bypassing most hardware-level protections introduced after the forementioned flaws have been patched.
When exploited, the flaw could allow attackers to infiltrate victim's computer kernel memory, and gain access to sensitive information, such as passwords, tokens and private conversations.
Related: The Spectre Bug Returns With Eight New Variants, With Four Of Them Critical
The flaw happened to reside on all Intel processors that support the SWAPGS system call, the functionality that allows the processor to swap between the kernel mode and user mode memory, found in most Intel CPUs released after 2012, which include third-generation Intel Core processors and beyond..
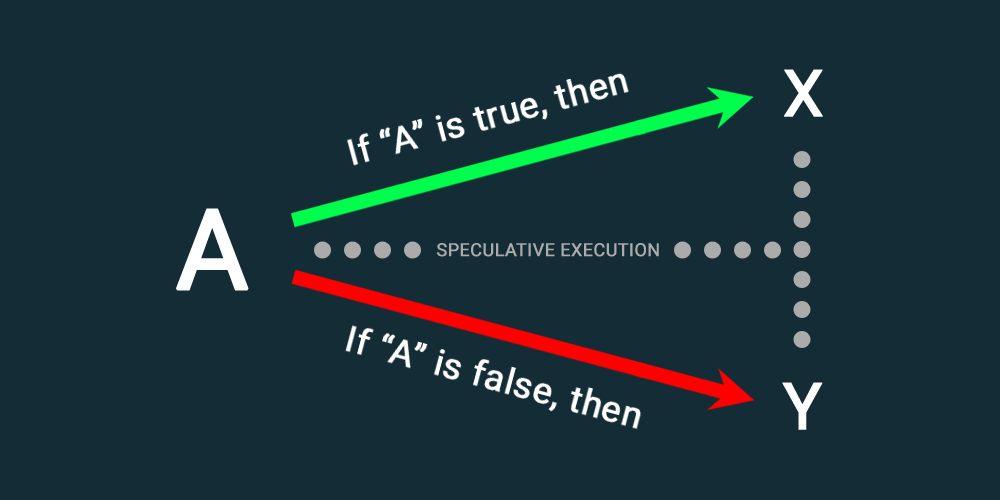
This feature is part of the 'speculative execution' features present in most modern processors, which allow the CPU to predict what users are going to do by making educated guesses.
While speculation execution is meant and indeed can improve performance for end-users, but it also allows attackers to access sensitive data, simply because speculative execution can leave traces of data inside its cache.
To exploit this vulnerability, attackers can combine this Intel's speculative execution of instructions, and the use of a specific instruction by Windows s within what is known as a gadget.
According to Gavin Hill, Vice President, Datacenter and Network Security Products at Bitdefender said:
"Research into these attacks is on the cutting edge as it gets to the very roots of how modern CPUs operate and requires a thorough understanding of CPU internals, OS internals, and speculative execution side-channel attacks in-general."
Because the flaw happens on the hardware itself, anyone who use the affected processors on a shared computer are among those with the greatest risk.
BitDefender predicts that the vulnerability can pose serious risks to all Intel processor users, both personal and corporate. However, due to the inherent complexity of chip-level exploits, the company doesn’t foresee a situation where attackers can exploit for mass destruction.
In other words, the bug in question my not be that alarming as the NSA-developed exploit EternalBlue when it was tweaked to spread the infamous WannaCry ransomware.
But still, the vulnerability is a big one.
Since Intel processors power most modern computers, this ubiquity presents a troubling security challenge.
While security fixes can mitigate the issue, it's always a challenge to push the security patch on a software level, to computers that are already online. This is because the fixes are often pushed through microcode patches, which means that many users may neglect to install them.
Pretty similar to Meltdown and Spectre, the patches can also cause dramatic deterioration in computer performance.
